Secure Access. Enable AI. Build on Zero Trust
Implement Microsoft Entra ID and Zero Trust principles to protect identities, secure access, and prepare for AI-driven innovation.
Why Identity & Access Management Matters
Modern organizations face evolving threats and compliance challenges. IAM ensures the right people - and now AI agents - have the right access at the right time. With Zero Trust and AI-driven security, you can reduce risk, enable productivity, and future-proof your business.
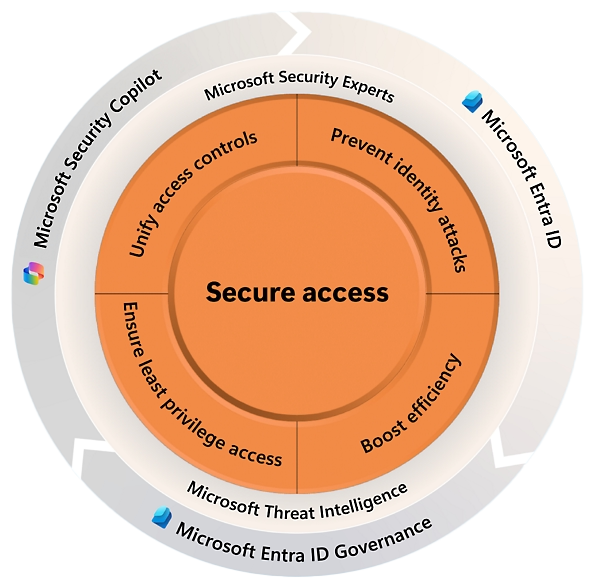
Microsoft Security solutions are field-tested and proven to secure identity access across on-premises and cloud environments. Partner with Netwoven to leverage these solutions and strengthen your identity and network access security posture—making your organization more resilient, user-centric, and efficient.
Services
Entra ID Implementation & Migration
Entra ID Implementation & Migration
Customer Identity & Access Management (CIAM)
Customer Identity & Access Management (CIAM)
Passkey & User Experience Optimization
Passkey & User Experience Optimization
Managed IAM Services
Managed IAM Services
AI Agent Identity Management
AI Agent Identity Management
Identity Governance & Compliance
Identity Governance & Compliance

Security Migration Solution

Security Migration Solution
Get Started
Insights
Thought Leadership
Identity as the New Perimeter The security landscape has shifted. According to the Verizon 2024 Data Breach Investigations Report, 74% of breaches involve the human element—stolen credentials, phishing, and insider… Continue reading Securing Microsoft 365: The Identity Health Check Imperative
Introduction AI agents are rapidly transforming the way organizations operate, collaborate, and innovate. But as enterprises embrace these powerful tools, a new and often overlooked challenge has surfaced: AI agent… Continue reading How to Prevent AI Agent Sprawl: Lessons from Microsoft and Netwoven
Introduction Agentic AI and conversational AI present exciting opportunities to transform how organizations conduct and manage access reviews. Here’s a breakdown of how to use Agentic AI in access review… Continue reading The Future of Access Reviews: Opportunities with Agentic and Conversational AI
Introduction In this blog, I share details on how to go about initiating an access review and managing the initiative. To find out more about access reviews, you can review my… Continue reading Initiating an Access Review Project: A Comprehensive Guide
Introduction IGA stands for Identity Governance and Administration. It’s a core component of identity and access management (IAM) that focuses on managing digital identities and their access rights across an… Continue reading Mastering Access Reviews: The Key to Smarter Identity Governance & Administration in 2025
Why Choose Netwoven?
Secure your digital assets with confidence. Netwoven’s Identity and Access Management (IAM) solutions are designed to help organizations take control of their security landscape. From identity governance to cloud access protection, we combine deep expertise with industry-leading technologies to deliver solutions that are both compliant and efficient — empowering your teams to work securely and seamlessly.
Contact Us- 1Microsoft Entra ID SpecialistsDeep knowledge of Conditional Access, MFA, and Zero Trust frameworks.
- 2Proven Expertise20+ years securing identities across hybrid and cloud environments.
- 3AI-Ready SecurityPrepare for AI-driven identity governance and Copilot integration.
- 4Automation and Best PracticesStreamlined onboarding/offboarding with automation scripts.
- 5Compliance Built-InSolutions aligned with GDPR, HIPAA, and other regulations.

Prefer to call?1-877-638-9683
Drop us a mailinfo@netwoven.com
Talk with an Expert
Find out how we can help you with your organization’s digital transformation journey.



















