Security Transformation with AI
Safeguard your business with a three-step security transformation framework that unlocks Microsoft’s AI-Powered security suite and delivers industry-leading protection.
Accelerate your security transformation with AI-powered automation and trusted expertise from a Microsoft security partner
Cyber threats are evolving faster than ever—and so must your defenses. According to IBM, 83% of organizations experience more than one data breach in their lifetime, with financial and reputational damage that can take years to recover from. These challenges demand more than reactive measures—they require intelligent, automated, and adaptive security strategies.
Netwoven’s three-step security modernization framework empowers organizations to unlock the full potential of Microsoft’s AI-powered security suite. By combining automation, advanced analytics, and deep integration, we help you mitigate threats, reduce risk, and accelerate adoption of enterprise-grade protection.
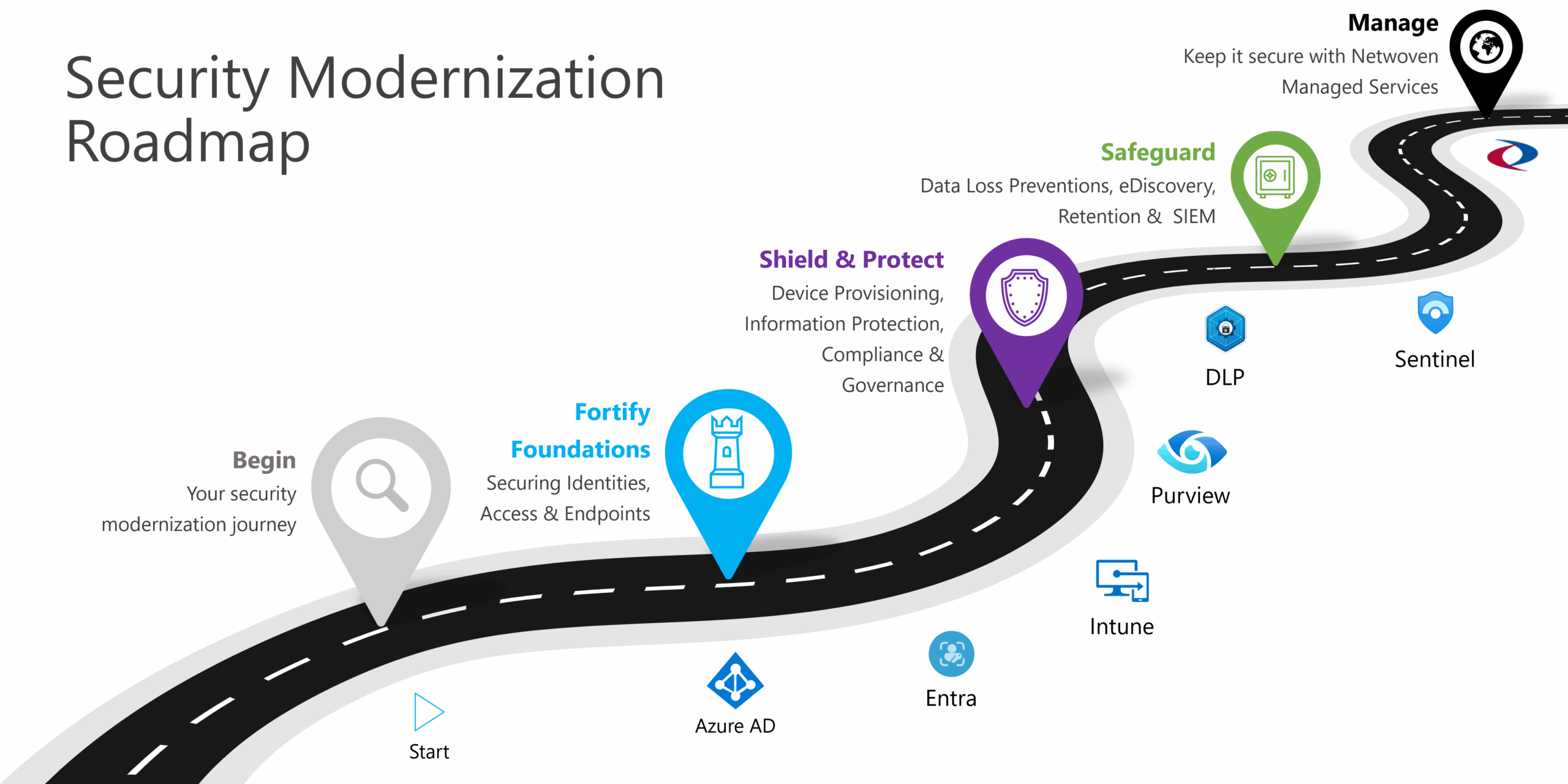
Start by fortifying your foundations, then shield and protect, and finally safeguard and manage your security protocols for continuous defense across four critical pillars:
- Secure Identity and Access with AI-driven authentication and governance
- Manage Your Endpoints using automated provisioning and real-time analytics
- Protect Against Threats with intelligent detection and rapid response
- Protect Your Data through automated classification, labeling, and compliance workflows
With Netwoven, security becomes a strategic enabler—powered by AI, streamlined by automation, and built for resilience.
Netwoven’s Security Transformation services harness Microsoft’s AI-powered security suite to deliver proactive threat detection, automated incident response, and continuous compliance—so your business stays resilient and secure.
Security Transformation Solutions
We provide the required fences at every checkpoint in your security journey
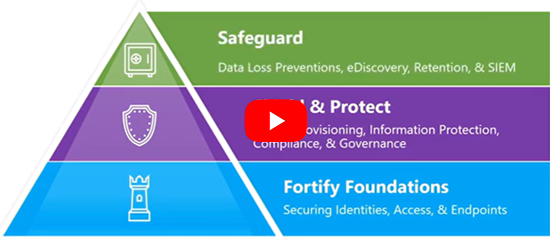
Fortify Foundations
Securing identities, access and endpoints
Shield & Protect
Device provisioning, information protection, compliance and governance
Safeguard
Data loss preventions, eDiscovery, retention and SIEM
|
|
Secure Identity & Access |
Endpoint Management |
Threat Protection |
Data Protection |
|---|---|---|---|---|
| Fortify Foundations |
|
|
|
|
| Shield & Protect |
|
|
|
|
| Safeguard |
|
|
|
|
To learn more, download our eBook: Three-Steps to a Successful Security Modernization Journey
Strategic Outcomes
The following are the significant improvements that occur between organizations with fully deployed security AI and automation versus organizations with no security AI and automation deployed.
Netwoven’s proven security modernization methodology delivers rapid time-to-value, measurable cost savings, and a resilient security foundation for the AI era. Schedule a complimentary AI Security Assessment with Netwoven’s experts.
Implementation Framework
Entra (Identity & Access Management)
Entra (Identity & Access Management)
Purview (Data Governance & Compliance)
Purview (Data Governance & Compliance)
Defender (Threat Protection Suite)
Defender (Threat Protection Suite)
Sentinel (Cloud-Native SIEM & SOAR)
Sentinel (Cloud-Native SIEM & SOAR)
Intune (Endpoint & Device Management)
Intune (Endpoint & Device Management)
Get Started

Insights
Thought Leadership
Today, the world witnessed one of the most significant cybersecurity outages in recent history. CrowdStrike, a leading provider of cybersecurity solutions, experienced a massive outage that rippled across the globe,… Continue reading What Really Happened? The CrowdStrike Outage Explained
Introduction In today’s rapidly expanding digital landscape, the demand for robust and secure network infrastructure is growing rapidly. As businesses grow and their operations span multiple geographic locations, the need… Continue reading Building A Global Secure Transit Network Using Azure Virtual Wan
Introduction In today’s digital age, businesses are increasingly relying on cloud services to store, manage, and process their data. While the cloud offers unparalleled flexibility and scalability, it also introduces… Continue reading 11 Best Practices for Securing Data in the Cloud
In today’s digital landscape, where organizations face an ever-increasing barrage of cyber threats, investing in robust cybersecurity measures is no longer an option but a necessity. Among the multitude of… Continue reading Why Microsoft Security Modernization Should Top Your Investment Priority List
As cyber threats continue to evolve and grow in sophistication, organizations need to constantly evaluate and optimize their cybersecurity investments to stay ahead of the curve. One solution that has… Continue reading How XDR and Sentinel Can Revolutionize Your Threat Detection and Response
Why Choose Netwoven?
As a Microsoft Preferred Solutions Partner, we bring extensive deployment expertise and exclusive access to Microsoft product teams, ensuring high-impact solutions. Our differentiators include the use of proven templates and reusable assets for on-time, on-budget delivery, a global delivery model that reduces implementation and management costs, and a phased implementation approach that minimizes risk through incremental progress aligned with a proven solution roadmap.
Contact Us- 1Microsoft Preferred Solutions PartnerExtensive deployment expertise and exclusive access to Microsoft product teams by being a Microsoft Preferred Solutions Partner.
- 2Templates and Reusable AssetsOn-time and on-budget solution delivery by applying industry best practices and our proven techniques
- 3Global Delivery ModelReduced implementation and management costs by utilizing our proven global delivery model
- 4Phased ImplementationReduced risk by taking incremental steps leveraging our proven solution roadmap

Prefer to call?1-877-638-9683
Drop us a mailinfo@netwoven.com
Talk with an Expert
Find out how we can help you with your organization’s digital transformation journey.