Introduction
In today’s interconnected business landscape, cybersecurity isn’t just an IT concern-it’s a business imperative. With cyber threats evolving at breakneck speed and becoming increasingly sophisticated, organizations find themselves navigating a complex maze of security solutions, each promising to be the silver bullet against digital adversaries.
The alphabet soup of cybersecurity acronyms-EPP, EDR, MDR, XDR-can leave even seasoned executives scratching their heads. But here’s the thing: understanding these solutions isn’t just about keeping up with tech jargon. It’s about making informed decisions that could mean the difference between business continuity and catastrophic data breaches.
Let’s cut through the complexity and explore these cybersecurity solutions in plain English, helping you build a defense strategy that actually makes sense for your organization.
Understanding the Cybersecurity Landscape: A Corporate Building Security Analogy
Imagine your organization’s digital infrastructure as a modern corporate headquarters-a multi-story building housing your most valuable assets, sensitive data, and critical operations. Just as you wouldn’t rely on a single security guard to protect an entire corporate campus, cybersecurity requires multiple layers of protection, each serving a specific purpose.
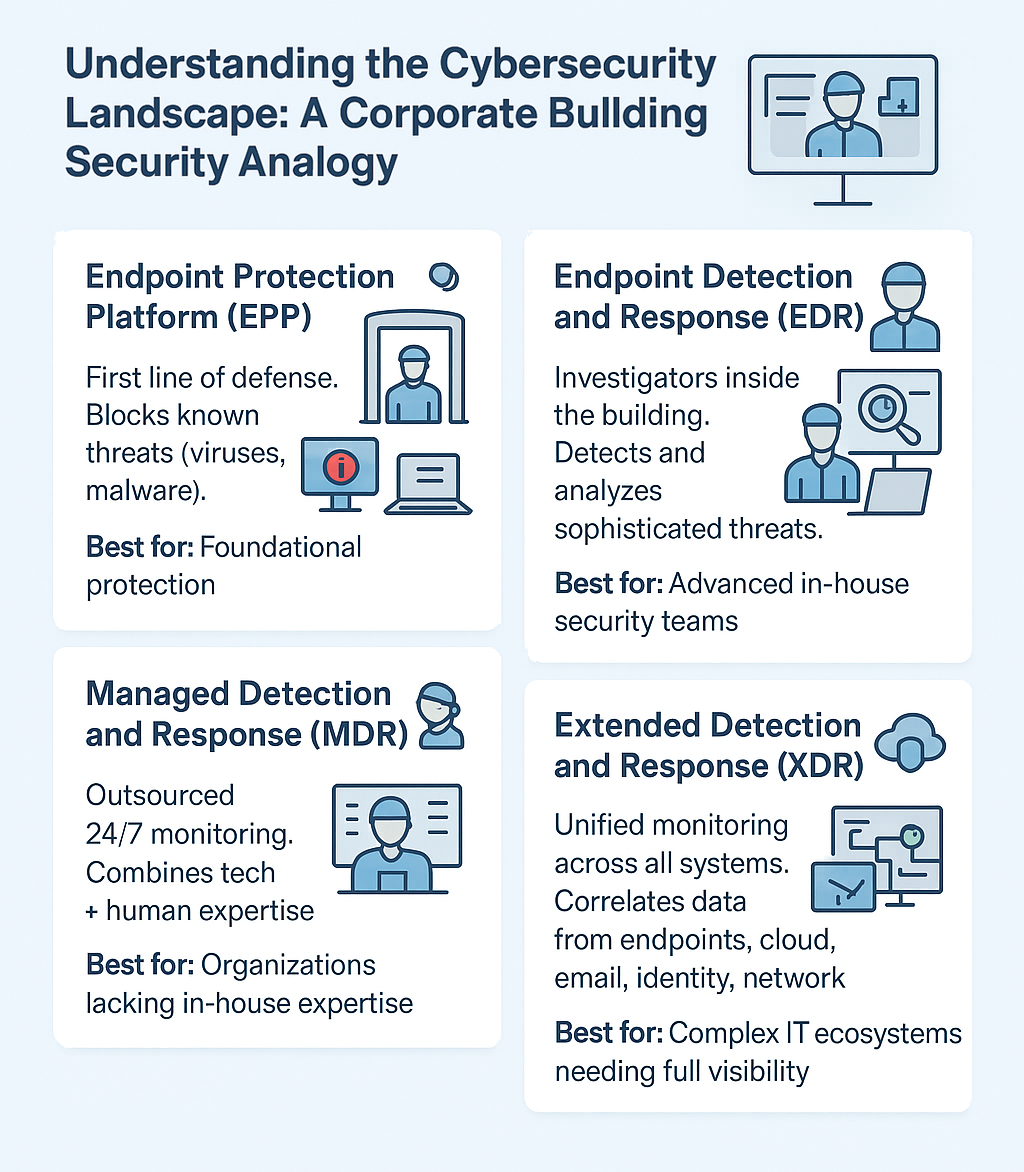
Endpoint Protection Platform (EPP): Your Digital Security Checkpoint
Think of EPP as the sophisticated security checkpoint at your building’s main entrance. Just as visitors must pass through metal detectors, show identification, and have their bags scanned, EPP scrutinizes every piece of data trying to enter your network endpoints—laptops, desktops, servers, and mobile devices.
EPP solutions are your first line of defense, using signature-based detection and behavioral analysis to identify and block known threats like malware, viruses, and suspicious files before they can establish a foothold in your system. They’re excellent at preventing the “usual suspects” from getting through the door, but they operate on the assumption that threats can be identified upfront.
Best for: Organizations seeking foundational protection against known threats with straightforward deployment and management requirements.
Endpoint Detection and Response (EDR): Your Internal Security Investigation Team
While EPP guards the entrance, EDR functions like a dedicated security investigation team that continuously patrols your building’s interior. These aren’t just security guards walking the halls—they’re forensic investigators with advanced surveillance capabilities, monitoring employee behavior, tracking unusual activities, and maintaining detailed logs of everything happening within your digital premises.
EDR solutions excel at detecting sophisticated threats that have bypassed initial security measures. They provide deep visibility into endpoint activities, allowing security teams to investigate incidents, understand attack patterns, and respond to threats with surgical precision. When something suspicious happens—like an employee accessing files they shouldn’t or unusual data transfers occurring at odd hours—EDR raises the alarm and provides the context needed for effective response.
Best for: Organizations with dedicated security teams who need advanced threat hunting capabilities and detailed forensic analysis.
Managed Detection and Response (MDR): Your Outsourced Security Operations Center
Not every organization has the resources to maintain a full-time, expert security investigation team. This is where MDR comes in—imagine outsourcing your entire security operations to a specialized firm that provides 24/7/365 monitoring and response services.
MDR providers combine advanced technology with human expertise, offering the same investigative capabilities as EDR but with the added benefit of experienced security professionals who monitor your environment around the clock. They don’t just detect threats—they investigate, contain, and remediate them, often before your internal team even knows an incident occurred.
Best for: Organizations lacking internal security expertise or those requiring continuous monitoring without the overhead of building an in-house security operations center.
Extended Detection and Response (XDR): Your Integrated Security Command Center
XDR represents the evolution of security operations-imagine a centralized command center that doesn’t just monitor your building’s interior but integrates with city-wide surveillance systems, traffic cameras, communication networks, and even weather monitoring systems to provide a comprehensive view of potential threats.
XDR solutions break down the traditional silos between different security tools, correlating data from endpoints, networks, email systems, cloud workloads, and identity management platforms. This holistic approach enables security teams to detect complex, multi-stage attacks that might appear benign when viewed through individual security tools but reveal malicious intent when analyzed collectively.
Best for: Mature organizations with complex IT environments seeking unified threat detection and response across their entire digital ecosystem.
The Executive Decision Matrix: Choosing Your Cybersecurity Strategy
Strategic Considerations for CISOs and CTOs
Selecting the right cybersecurity solution isn’t just a technical decision—it’s a strategic business choice that impacts your organization’s risk posture, operational efficiency, and bottom line. Here’s how to approach this decision from an executive perspective:
1. Organizational Maturity Assessment
Emerging Organizations: If you’re a growing company with limited security infrastructure, start with EPP for foundational protection. It’s cost-effective, easy to deploy, and provides essential security without overwhelming your IT team.
Established Organizations: Companies with dedicated IT teams but limited security expertise should consider MDR. You get enterprise-grade protection without the complexity of building internal security operations.
Mature Enterprises: Large organizations with complex environments and existing security teams should evaluate EDR or XDR based on their integration requirements and threat landscape complexity.
2. Risk and Compliance Framework
- Highly Regulated Industries (Financial Services, Healthcare, Government): XDR or MDR with comprehensive logging and reporting capabilities
- Standard Compliance Requirements (SOC 2, ISO 27001): EDR with proper documentation and incident response procedures
- Basic Compliance Needs: EPP with regular updates and patch management
3. Resource Allocation Strategy
| Solution | Initial Investment | Ongoing Costs | Internal Resources Required | ROI Timeline |
|---|---|---|---|---|
| EPP | Low | Low | Minimal | Immediate |
| EDR | Medium | Medium | Dedicated security analyst | 3-6 months |
| MDR | Medium-High | High | Minimal | 1-3 months |
| XDR | High | High | Security operations team | 6-12 months |
4. Integration and Scalability Considerations
Current Technology Stack: Evaluate how well each solution integrates with your existing security tools, SIEM systems, and IT infrastructure. XDR solutions typically offer the best integration capabilities but require more complex implementation.
Growth Trajectory: Consider your organization’s growth plans. EPP might suffice today, but will it scale with your expanding digital footprint? MDR services can grow with you without requiring additional internal resources.
Cloud Strategy: Organizations with significant cloud adoption should prioritize solutions with strong cloud-native capabilities. XDR platforms typically offer the most comprehensive cloud security integration.
Building Your Layered Defense Strategy
Here’s a crucial insight that many organizations miss: these solutions aren’t mutually exclusive. The most effective cybersecurity strategies combine multiple approaches to create a comprehensive defense ecosystem.
Recommended Implementation Roadmap
Phase 1 – Foundation (Months 1-3): Implement EPP across all endpoints to establish baseline protection. This provides immediate value while you plan more advanced capabilities.
Phase 2 – Detection (Months 4-9): Add EDR capabilities or engage an MDR provider based on your internal resources. This phase focuses on improving threat detection and response capabilities.
Phase 3 – Integration (Months 10-18): For mature organizations, consider XDR implementation to unify security operations and improve threat correlation across your entire environment.
Making the Business Case
When presenting cybersecurity investments to your board or executive team, frame the discussion around business outcomes rather than technical features:
- Risk Reduction: Quantify the potential cost of data breaches in your industry and demonstrate how your chosen solution reduces this risk
- Operational Efficiency: Highlight how automated threat detection and response reduce the burden on your IT team
- Compliance Assurance: Show how the solution helps maintain regulatory compliance and avoid potential fines
- Business Continuity: Emphasize how proactive threat detection minimizes business disruption

Whitepaper: Choosing the Right SOC Model in the Age of AI
Download our exclusive whitepaper, “Choosing the Right SOC Model in the Age of AI,” and discover how to evaluate in-house, MSP, MSSP, MDR, and MXDR models through the lens of cost, control, scalability, and AI-driven threat response.
Get the WhitepaperConclusion
Cybersecurity isn’t about finding the perfect solution, it’s about building the right defense strategy for your organization’s unique needs, risk profile, and resources. Whether you start with EPP’s foundational protection, leverage MDR’s expertise, or implement XDR’s comprehensive approach, the key is to begin building your defenses today.
Remember: The best cybersecurity solution is the one that gets implemented, maintained, and continuously improved. Don’t let perfect be the enemy of good. Start where you are, use what you have, and build from there.























