Introduction
A recent research by Elastic reveals that 44% of security professionals, including 51% of CEOs and 52% of CTOs, are eyeing a security information and event management (SIEM) migration. In fact, SIEM is going to be the top investment area in cybersecurity — along with identity and access management (IAM) — within the next two years.
Splunk has long been a popular choice for security information and event management (SIEM) due to its robust data analytics and log management capabilities. However, many organizations are now considering a migration to Microsoft Sentinel—a cloud-native SIEM solution that offers a more scalable, cost-effective, and integrated approach to modern security operations.
Why Consider Migrating from Splunk to Sentinel?
Splunk, while a powerful data platform, can present certain challenges for organizations. Here are some common issues that users may encounter:
1. Complexity
Steep learning curve: Splunk can be complex to learn and use, especially for users without a strong technical background. Configuring Splunk to meet specific needs can be time-consuming and require technical expertise.
2. Performance and Scalability
Performance bottlenecks: Handling large volumes of data can lead to performance issues if not properly configured and optimized. Scaling Splunk to accommodate growing data volumes can be expensive and complex.
3. Cost
Licensing costs: Splunk can be expensive, especially for large organizations with high data volumes. Users may incur additional costs for storage, support, and customizations.
4. Integration Challenges
Integration with other systems: Integrating Splunk with other tools and platforms can be complex, especially for organizations with heterogeneous environments.
5. Data Quality and Governance
Data quality issues: Ensuring data accuracy and consistency can be challenging, especially when dealing with multiple data sources. Establishing data governance policies and procedures can be time-consuming and complex.
6. User Experience
Complexity for non-technical users: Splunk’s interface can be complex for users without a strong technical background. Customizing the user interface to meet specific needs can be difficult.
Splunk vs Microsoft Sentinel: A Comparison
| Feature | Splunk | Microsoft Sentinel |
|---|---|---|
| Core Functionality | Enterprise-grade data platform for machine data | Cloud-native security information and event management (SIEM) solution |
| Data Ingestion | Ingests data from various sources, including logs, metrics, and events | Ingests data from Azure resources and other sources, including logs, alerts, and security events |
| Search and Analysis | Powerful search capabilities with advanced analytics | Advanced search, analytics, and threat detection capabilities |
| Visualization | Customizable dashboards and reports | Built-in visualizations and threat detection rules |
| Machine Learning | Machine learning capabilities for automated data analysis | Built-in machine learning for threat detection and anomaly detection |
| Integration | Integrates with various tools and platforms | Deeply integrated with Microsoft 365 and Azure services |
| Deployment | On-premises, cloud, or hybrid deployment options | Cloud-native solution, deployed in Azure |
| Pricing | Subscription-based pricing with various tiers | Subscription-based pricing with different plans |
Splunk to Microsoft Sentinel Migration Checklist
Please find the checklist for the migration below
1. Understand data across your SIEM
Begin by thoroughly understanding your current SIEM environment within Splunk. This involves identifying key data sources, data types, and data volumes. A comprehensive analysis will help you map these elements effectively when transitioning to Microsoft Sentinel. Ensure that the SIEM infrastructure aligns with Sentinel’s capabilities, allowing for smooth continuity. Finally consider the mapping of the SIEM infrastructure to Microsoft Sentinel for smooth continuity.
2. Analyze and Prioritize the Data Sources
Please identify the data sources that are significant for security and compliance in your organization. Prioritize the data sources that are critical for security, compliance, and business operations. These sources should be reviewed for compatibility with Sentinel. Since Sentinel can ingest data from both on-premise and cloud environments, ensure that all necessary data sources, such as firewalls, intrusion detection systems, and logs from applications, are configured for ingestion into Microsoft Sentinel.
3. Review the Microsoft Sentinel Licensing
Microsoft Sentinel’s pricing is heavily influenced by data ingestion and retention rates. It’s crucial to ensure that your organization has the right capacity for data storage and processing under its licensing plan. Consider Sentinel’s pay-as-you-go model and confirm that your subscription covers all essential data volumes without unexpected cost overruns. Additionally, evaluate if you need add-ons such as advanced machine learning models or automated threat detection features.
4. Evaluate Data Transformation Rules
Check and re-evaluate all your current data transformation and parsing rules. These rules are essential for maintaining data consistency between Splunk and Sentinel. Sentinel’s use of Kusto Query Language (KQL) offers advanced parsing and querying capabilities, so review your existing transformation logic to ensure compatibility with KQL, adjusting parsing rules as necessary for smoother data processing.
5. Migrate Dashboards, Alerts, and Log Collection
Set up Azure Log Analytics Workspaces as the primary data repository in Sentinel. Connect your prioritized data sources to ensure smooth data flow. Following that, replicate and customize your Splunk dashboards in Sentinel, taking advantage of its visual analytics capabilities for real-time threat detection and analysis. Migrate existing alerts and set up custom alerts using Azure Monitor and Logic Apps. Make sure your team tests these thoroughly to verify that alerts, dashboards, and data flows function as expected, ensuring seamless transition of your monitoring and analytics.
6. Check Data Ingestion Rate and Adjust Accordingly
Microsoft Sentinel’s data ingestion limits are tied to your subscription level, and exceeding those rates can lead to increased costs or data loss. Assess your current data ingestion rate in Splunk and compare it with the ingestion capabilities of your Sentinel subscription. If required, adjust data collection strategies or retention policies to align with Sentinel’s limitations and optimize for cost and performance. Additionally, monitor Sentinel’s built-in AI to ensure that alert volumes and thresholds are well-balanced for timely responses.
7. Migrate Detection Rules with Precision
Microsoft Sentinel uses machine learning and built-in analytics to reduce noise from false positives, but not all Splunk detection rules will fit Sentinel’s analytics model. Begin by auditing your existing detection rules. Prioritize migrating rules that are both business-critical and efficient. Sentinel’s AI-driven analytics might replace some low-level rules, so discard those that no longer add value. When migrating, ensure to test detection rules on relevant use cases, revising KQL queries as necessary until you’re satisfied with the accuracy of detections. Playbooks can also be used to automate rule actions for more complex security needs.
8. Migrate SOAR Automations
Sentinel’s Security Orchestration, Automation, and Response (SOAR) capabilities simplify incident response through playbooks and automation rules. Review the automation workflows currently in use with Splunk and migrate the relevant ones to Sentinel. If necessary, create new automation playbooks leveraging Azure’s Logic Apps for more advanced use cases. These playbooks can streamline response actions, such as automatically isolating compromised devices or tagging incidents for priority response.
9. Export Historical Data from Splunk
Exporting historical data from Splunk will allow your organization to retain valuable records for compliance and analysis. Depending on the data volume, you can either use Splunk Web for low-volume exports or REST and SDK tools for more extensive data. Ensure you export data in compatible formats like CSV for ingestion into Microsoft Sentinel. This allows your team to continue working with historical security events within the new SIEM environment.
10. Run Splunk and Microsoft Sentinel Side by Side
It is advisable to run Splunk and Microsoft Sentinel in parallel for a transitional period to ensure a seamless migration. This side-by-side approach helps with testing the data flow, alerts, and incident response capabilities in Sentinel before fully decommissioning Splunk. For organizations that aren’t ready for a complete migration, this hybrid approach allows you to migrate over time, focusing initially on cloud data sources. Running them in tandem for a period ensures that security operations remain uninterrupted while allowing for phased adoption of Sentinel’s advanced analytics.
11. Train the Team on Microsoft Sentinel
Lastly, train your security operations and IT team to ensure they’re comfortable with the Microsoft Sentinel interface, data analytics, and custom rule creation. This includes hands-on training for utilizing Sentinel’s AI-driven threat detection, running KQL queries, managing dashboards, and implementing automated response workflows through SOAR playbooks. This step ensures that your team maximizes the potential of Microsoft Sentinel for security monitoring and threat response.

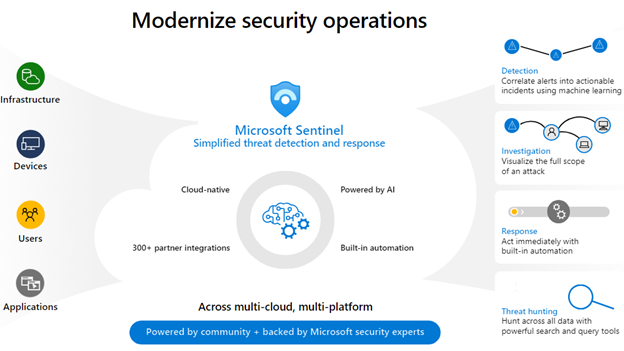
Ebook: Transform your security operations center with simplified threat detection and response
This eBook, brought to you by Netwoven, a global leader in Microsoft consulting services deep dives into Microsoft Sentinel, a next-generation cloud-native Security Information and Event Management (SIEM) solution.
Get the eBookConclusion
The complicated nature of migration makes it difficult to manage everything on your own. Thus, it becomes crucial to rely on a migration expert. Netwoven is an expert in SIEM migration and has been doing all sorts of migrations for more than 2 decades now. Netwoven can help you streamline your planning, assessment, monitoring and analyzing for a better transition. If you think you need expert support, reach out to us and we will assist you further.
Also, don’t forget to check out Netwoven’s free 1-hour workshop on “Migrate Your SIEM to Sentinel”.























