Introduction:
After a major security product re-brand and feature/functionality enhancements, the Defender Suite takes shape:
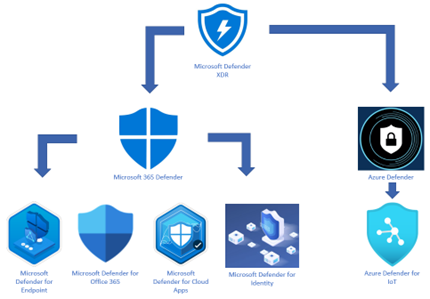
Defender Branding Updates
| New Name | Old Name |
| Microsoft 365 Defender | Microsoft Threat Protection |
| Defender for Endpoint | Microsoft Defender Advanced Threat Protection |
| Defender for Identity | Microsoft Defender for Identity |
| Defender for Office 365 | Microsoft Defender for Office 365 |
| Azure Defender for Servers | Azure Security Center Standard |
| Azure Defender for IoT | Azure Security Center for IoT |
| Azure Defender for SQL | Advanced Threat Protection for SQL |
What is Endpoint Detection & Response?
Endpoint Detection & Response (EDR), also known as Endpoint Threat Detection & Response (ETDR), is a cybersecurity technology that continually monitors an ‘endpoint’ (e.g., mobile phone, laptop, Internet-of-Things device) to mitigate malicious cyber threats.
Endpoint Detection & Response technology is used to identify suspicious behavior and Advanced Persistent Threats on endpoints in an environment, and alert administrators accordingly. It does this by collecting and aggregating data from endpoints and other sources. That data may or may not be enriched by additional cloud analysis. EDR solutions are primarily an alerting tool rather than a protection layer, but functions may be combined depending on the vendor. The data may be stored in a centralized database or forwarded to a SIEM (Security Incident & Event Management) tool.
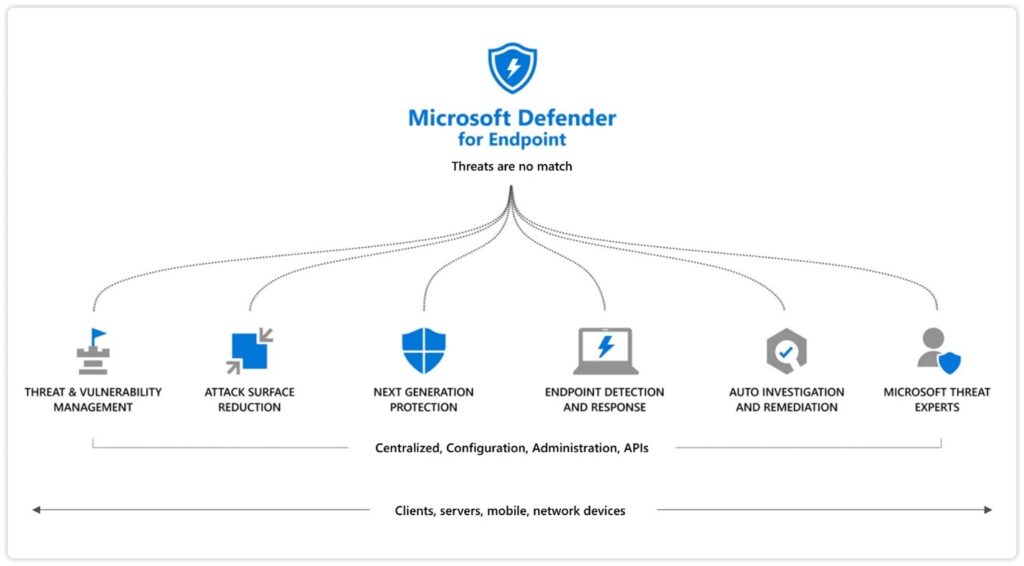
Why Defender for Endpoint
Defender for Endpoint is one of the most powerful yet underrated in this group of products – just think about it for a moment, it covers every endpoint, or in other words, entryways into your organization. So, as you can see it profoundly affects the security posture on an organization-wide level.
The cyber-security landscape is rapidly changing and evolving, so you can argue that legacy ‘old-school’ security products/platforms just cannot keep up and this is often overlooked. You absolutely need Artificial Intelligence and device learning/machine learning at the backbone to keep pace.
Defender for Endpoint EDR – Behavioral blocking & containment
This is just one part of Microsoft’s ‘next-gen protection’ – this helps identify and stop threats that are identified based on their behaviors and the process trees from them – and even be identified after the threat has kicked off.
Here is where the beauty of Microsoft’s Marketing punchline ‘Better-together’ comes into play- these next-gen protection features with EDR and other components in Endpoint Protection work seamlessly to block and contain these anomalies:
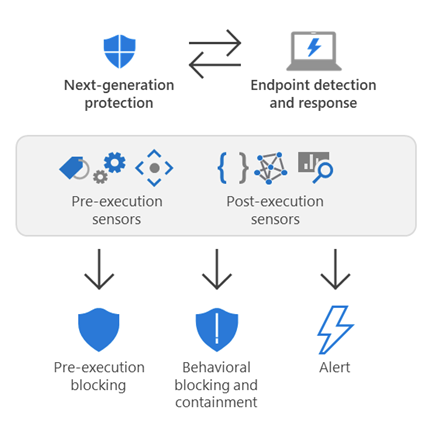
- Next-gen protection- Detect threats by analyzing behaviors and stop threats that have already started executing
- Endpoint Detection & Response (EDR) receives security signals across the network, devices, and kernel behavior.
- As threats are detected, alerts are created. Many alerts of the same type are grouped into incidents, which makes it easier for your security operations team to investigate and respond
- Defender for Endpoint has a wide range of optics across identities, email, data, and apps, in addition to the network, endpoint, and kernel behavior signals received through EDR
- A component of Microsoft 365 Defender, Defender for Endpoint processes and correlates these signals, raises detection alerts and connects related alerts in incidents
Behavioral Blocking Examples:
Behavioral blocking and containment capabilities have blocked attacker techniques like these:
- Credential dumping from LSASS
- Cross-process injection
- Process hollowing
- User Account Control bypass
- Tampering with antivirus (such as disabling it or adding malware as exclusion)
- Contacting Command and Control (C&C) to download payloads
- Coin mining
- Boot record modification
- Pass-the-hash attacks
- Installation of root certificate
- Exploitation attempts for various vulnerabilities
In Part 2 of this blog series, we will discuss in detail how to enable Endpoint Detection & Response.
Netwoven Assessment Workshops
If you like this blog topic, then have a look at our Endpoint Manager Assessment Workshop where you will learn how to empower your mobile workforce while keeping business-critical information secure.























