Introduction
SessionShark is a newly discovered phishing-as-a-service (PhaaS) toolkit serves as an adversary-in-the-middle (AiTM) designed to bypass Microsoft Office 365 multifactor authentication (MFA) protections. It enables attackers to hijack authenticated sessions by stealing session tokens, rendering MFA ineffective.
How does SessionShark Work?
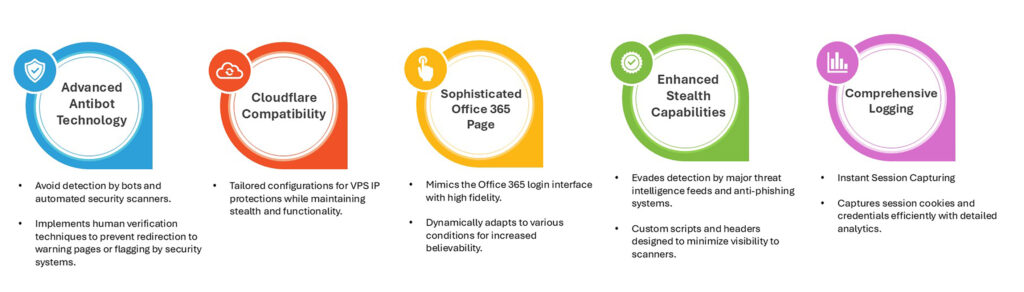
- Session Hijacking – Captures session cookies after a legitimate login, allowing attackers to bypass MFA.
- Highly Realistic Phishing Pages – Mimics Microsoft’s login interface dynamically to trick users.
- Cloudflare Integration – Masks phishing servers, making takedowns harder.
- RealTime Credential Theft – Sends stolen credentials and session tokens to attackers via Telegram notifications.
- Advanced Anti Detection Measures – Uses CAPTCHAs and antibot technology to evade security scanners.
Why is it a Concern?
This is a new challenge, and you may refer to this. “Finally, new cybersecurity threats include the “SessionShark” phishing toolkit, designed to bypass Office 365 MFA, and a massive breach by the hacking group R00TK1T, which compromised over 900,000 TikTok user credentials.” – Source
- MFA is No Longer Foolproof – Attackers bypass it via session hijacking.
- Phishing Kits Are Becoming More Accessible – Lowering the barrier for cybercriminals.
- Rapid Account Takeovers – Realtime alerts mean breaches happen before defenses react.
How to Defend Against It?
- Monitor for Suspicious Session Activity – Look for logins from unusual locations/devices.
- Implement Conditional Access Policies – Restrict sessions based on risk factors.
- Educate Employees on Advanced Phishing – Teach them to spot adversary in the middle (AiTM) attacks.
- Use AIDriven Threat Detection – Solutions like Microsoft Defender for Office 365 can help.
- Consider Zero Trust Security – Verify every access request, even after authentication.
Netwoven SOC: Proactive Defense Against Session Hijacking Attacks
With the rise of sophisticated phishing-as-a-service (PhaaS) toolkits like SessionShark, traditional security measures like multi-factor authentication (MFA) alone are no longer enough. Attackers are bypassing authentication controls by stealing session tokens, allowing them to hijack legitimate user sessions without triggering new MFA prompts. Recognizing these evolving threats, the Netwoven SOC team has implemented proactive security measures to mitigate risks and protect enterprise environments.
Conditional Access Policy Refinement
One of the core strategies in defending against session hijacking is refining Conditional Access policies to ensure continuous verification beyond the initial authentication.
The Netwoven SOC team has strengthened security controls by
- Enforcing token protection– Ensuring authentication tokens are bound to the originating device, preventing their misuse on attacker-controlled endpoints.
- Implementing risk-based conditional access – Leveraging Microsoft Entra ID to dynamically assess user risk based on device compliance, IP reputation, and location anomalies.
- Shortening session lifetimes – Reducing token validity periods to minimize exposure to hijacking attempts and forcing frequent reauthentication.
End-User Behavior Analysis
Detecting session hijacking requires continuous monitoring of user authentication trends and anomalies.
To combat this, Netwoven SOC analysts have deployed
- KQL-based anomaly detection queries in Microsoft Sentinel, tracking unusual session activity, multiple login locations, and first-time device access.
- Behavioral profiling – Establishing user authentication patterns to detect deviations, such as sudden logins from new locations or devices.
- Automated phishing risk scoring – Identifying users targeted by malicious campaigns and enforcing step-up authentication for at-risk accounts.
For example, below are some sample KQL queries used by the SOC team
Detect Suspicious Sign-ins from Multiple Locations in Short Time
SigninLogs
| where TimeGenerated > ago(7d)
| where Status == "Success"
| summarize login_count = count(), distinct_locations = dcount(Location)
by UserPrincipalName
| where distinct_locations > 2
| order by login_count desc Detect Potential Attacker Persistence via Session Hijacking
SigninLogs
| where TimeGenerated > ago(14d)
| summarize first_seen = min(TimeGenerated), last_seen = max(TimeGenerated), login_count = count()
by UserPrincipalName, SessionId
| extend session_duration = last_seen - first_seen
| where session_duration > 7d
| order by session_duration descContinuous Monitoring & Threat Hunting
SessionShark attacks thrive in environments where attackers can maintain persistent access undetected.
To prevent unauthorized sessions from lingering within the system, Netwoven SOC has implemented:
- Real-time session tracking – Monitoring ongoing sessions in Microsoft Sentinel to identify unusually long-lived authentications indicative of hijacking.
- Suspicious URL click analysis – Leveraging Defender for Office 365 logs to detect interactions with known phishing domains, preventing credential theft.
- Automated session revocation – Implementing policies to force session sign-outs when high-risk activity is detected, ensuring attackers lose access instantly.

Whitepaper: Choosing the Right SOC Model in the Age of AI
Download our exclusive whitepaper, “Choosing the Right SOC Model in the Age of AI,” and discover how to evaluate in-house, MSP, MSSP, MDR, and MXDR models through the lens of cost, control, scalability, and AI-driven threat response.
Get the WhitepaperConclusion
By refining Conditional Access, continuously analyzing user behavior, and monitoring sessions for anomalies, the Netwoven SOC team has taken a proactive stance against evolving threats like SessionShark. As adversaries adapt their tactics, continuous security evolution is key to preventing unauthorized access and ensuring enterprise resilience against session hijacking attacks.























