There is a critical security vulnerability found in the Credential Security Support Provider protocol (CredSSP) that could potentially lead to remote code execution. This vulnerability allows an attacker to intercept and relay user credentials, enabling them to execute malicious code on the targeted system.
CredSSP serves as an authentication provider for various applications, making any application reliant on CredSSP susceptible to this type of attack.
For instance, an attacker could leverage this vulnerability to exploit Remote Desktop Protocol (RDP) sessions by running a specially crafted application and conducting a man-in-the-middle attack. By doing so, the attacker gains the ability to install unauthorized programs, access, modify, or delete data, or even create new user accounts with complete privileges.
To address this critical issue, a security update has been developed to rectify the authentication process in the Credential Security Support Provider protocol (CredSSP). This update ensures the proper validation of authentication requests, effectively mitigating the vulnerability and safeguarding systems from potential exploitation.
1. SCENARIO
![[Solved] CredSSP Encryption Oracle Remediation](https://netwoven.com/wp-content/uploads/2023/05/img1-2-2.jpg)
2. RDP SESSION
An update released by Microsoft (KB 4093492) on May 8, 2018, for Windows 10 Operation System was targeted to change the default settings CredSSP from Vulnerable to Mitigated.
A full list of the update and patches for all platforms can be obtained from here.
However, post patching this caused an issue where the patched clients were blocked from communicating with unpatched servers over RDP protocols.
This has been reported to cause an error thrown by Windows RDP as below:
![[Solved] CredSSP Encryption Oracle Remediation](https://www.netwoven.com/wp-content/uploads/2020/06/img2-2.jpg)
3. WORKAROUND
Use the group policy settings changes described below to rollback the changes to ‘Vulnerable’ state to allow RDP access.
- Open Group Policy Editor, by executing gpedit.msc
- Policy path: Computer Configuration -> Administrative Templates -> System -> Credentials Delegation
- Run gpedit.msc and expand Administrative Templates
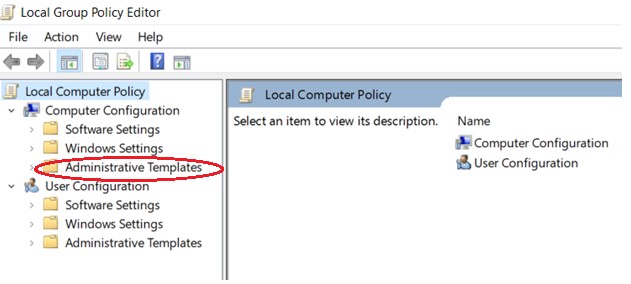
Expand System
![[Solved] CredSSP Encryption Oracle Remediation](https://www.netwoven.com/wp-content/uploads/2020/06/img4-2.jpg)
Expand Credential Delegation
![[Solved] CredSSP Encryption Oracle Remediation](https://www.netwoven.com/wp-content/uploads/2020/06/img5-2.jpg)
Edit Encryption Oracle Remediation
![[Solved] CredSSP Encryption Oracle Remediation](https://www.netwoven.com/wp-content/uploads/2020/06/img6-2.jpg)
Select Enabled and change Production Level to Vulnerable
![[Solved] CredSSP Encryption Oracle Remediation](https://www.netwoven.com/wp-content/uploads/2020/06/img7-2.jpg)
3. Run the command gpupdate /force to apply group policy settings.
4. Your remote desktop connection will be working fine now.
CONCLUSION
This is just a workaround and defeats the purpose of the patching. However, we need to ensure that future updates are installed as and when released by Microsoft so that the vulnerability is not exposed. Please let us know if this has solved your error.
Note: The post was originally published on May 15, 2018, and updated on June 23, 2023























thank u , my problem has been resolved
Thank you so much. My problem resolved
I am not able to find the ENCRYPTION ORACLE REMEDIATION option. Any solution for this issue
Hi Sirisha,
Microsoft’s recent updates discarded the ENCRYPTION ORACLE REMEDIATION option from Group Policy Editor because this group policy is the main issue.
Hence, you can run this below command in the command prompt to achieve the same result,
REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2
Solved it for me, thanks!
many many thanks. its work for windows 10 home single language too.
don’t know if you’ll see this or not but, I couldn’t use rdp after updating my windows 10. now if I would do this, will i still be able to use rdp after uploading?
i have tried but invalid key error found
Hi,
I am unable to find ENCRYPTION ORACLE REMEDIATION option from Group Policy Editor after ran ” REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2 “in the comand prompt. Please advise on this issue.
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4103723
I installed this patch on my windows 2016 standard and restarted, now iam able to take my server through RDP.
Try this it will definitely help you…….
Dhana
Thanks a lot..it solved my issue
thnk u so much..
Thank you, Got worried after several attempt on connecting to RDP was abortive. But after following the process you listed it worked.
Thank you so much for the solution
Thank you so much. Remote login problem has resolved
pefect solutions, thank you very much saving so much time and efforts.
hats off 🙂
Thanks a million pal, worked just perfect for me.
tried all these, it is still not working for me. do i need to restart the system or something?
you can run this below command in the command prompt to achieve the same result,
REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2
Thank you very much Priyam, it worked for me
This is the thing that actually worked for me!! Thanks!!
hello
i tried all the things you said and the changes were done fine but i still am finding the very same error. how do i get it resolved ?
same me
Hi
REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2
Please run this command in cmd for which comp you want to take RDP of other comp this will solve the problem.
This resolved my issue when connection to HYper-V Manager
thanks for your help the info given is very good and did it’s work
my problem has been solved
I am no getting the option “oracle encryption remediation” at the given path, other than that all the options are here
same here in Windows 2012 r2
It worked for me 🙂 Thank you.
Its worked for me
Windows 10 Pro
Jan, 2020
I’m working with;
REG ADD HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\ /v AllowEncryptionOracle /t REG_DWORD /d 2
Thank you so much. My problem resolved
thank you so much..problem solved
Thank you very much bro, my problem is solved instantly
Thank you so much. My problem resolved too
Thanks. It worked for me.
Thank you so much Sir, this works for me.
thank you so much.
my problem has been resolved
Yeah, its working.
Thanks a lot!!
Gr8. Thanks
Instructions were very simple and easy to follow. This resolved my issues. Thanks for the help provided.
Solved… GR8…
Is it safe after this settings or we need to do some other settings too for it to work safe
Solved. Thank you!
solved. thanks
command gpupdate /force is the thing nobody point on before you. Thanks!
Awesome thank you!
Thanks friend
Thank you! It’s helpful! 🙂
Thanks
Issue has been solved.
Worked like a charm … Sanchu
Thanks, error Solved
What if the Encryption Oracle Remediation is not listed when I expand Credentials Delegation?
having the same issue
it is not listed
Many Thanks Issue solved
Yes! It is resolved! Thank You!
Thanks alot, problem solved!
Thanks for the help, really helpful
Thanks for all
Hi Priyam. Thanks for the article.
It helped a lot.
Google first and best selection 🙂
thanks much it worked perfectly