Your Azure applications were working fine till yesterday, but suddenly you are unable to login to the hosted application and drilling down you found errors like “Invalid client secret is provided” or “Invalid issuer or signature” in error logs. This means the App-secret key has expired and you want to create and extend the expired App-Secret. Further you want to extend it say; for 3 years, before or after expiration, and this is the tricky part.
This article will guide you through the steps to perform Azure App-Secret Replacement, extending 3 years expiration period, where default is 1 year.
Get expiration dates of the SharePoint Add-ins installed to the Office 365
- Connect to Office 365 Tenant with PowerShell ISE
Connect-MsolService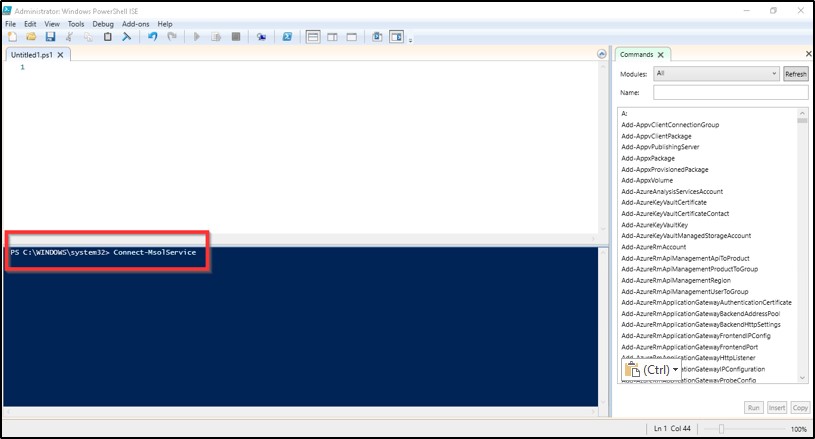
- When prompted Login with Global Admin Credential
- Once logged in to Office 365 tenant Keep the PS windows open for upcoming step
- Now create a PS1 script which will filter out MS own applications and add-ins under development. Also, exclude non-SharePoint add-ins and add-ins that use asymmetric keys and save the rest in a text file, Say for instance appsec.txt
Syntax :
$applist = Get-MsolServicePrincipal -all | Where-Object -FilterScript { ($_.DisplayName -notlike "*Microsoft*") -and ($_.DisplayName -notlike "autohost*") -and ($_.ServicePrincipalNames -notlike "*localhost*") }
foreach ($appentry in $applist)
{
$principalId = $appentry.AppPrincipalId
$principalName = $appentry.DisplayName
Get-MsolServicePrincipalCredential -AppPrincipalId $principalId -ReturnKeyValues $false | Where-Object { ($_.Type -ne "Other") -and ($_.Type -ne "Asymmetric") }
$date = get-date
Write-Host "$principalName;$principalId;$appentry.KeyId;$appentry.type;$date;$appentry.Usage"
} - Go to Script Path Say c:\temp and run the script followed by > c:\temp\appsec.txt to save the result in text file

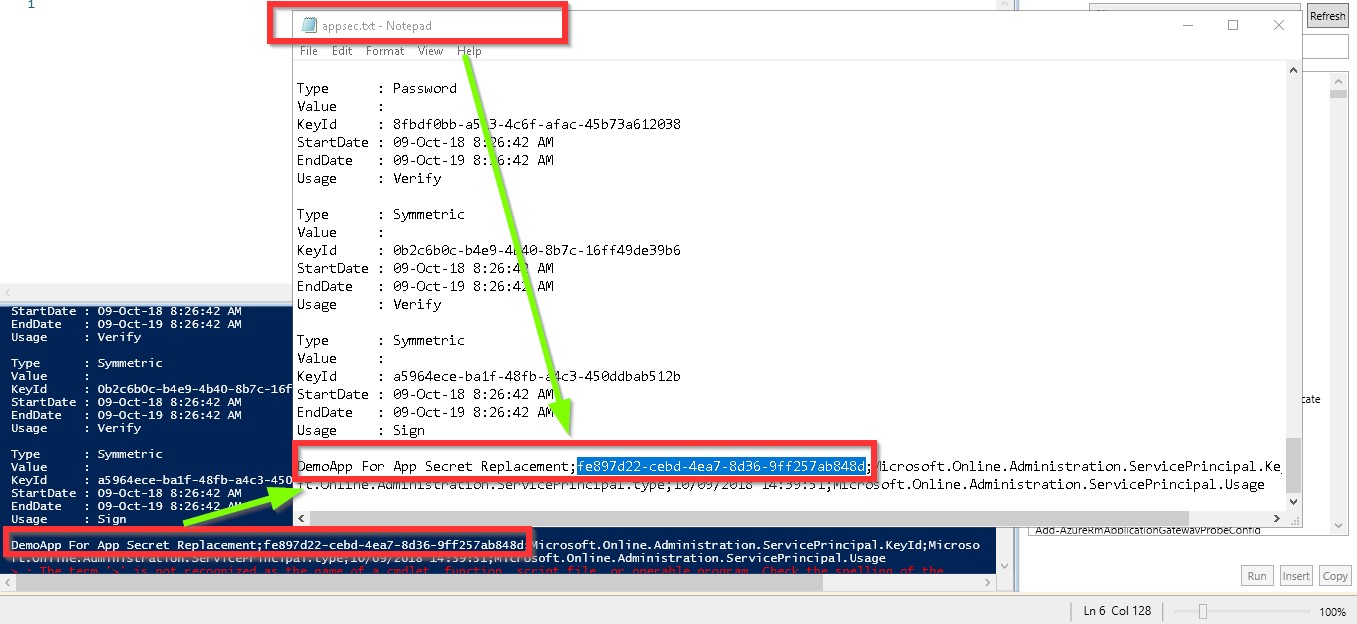
- Once the script is executed, collect the txt file and look if any of the secrets are near expiration or already expired. Or simple copy the result from PowerShell Screen.

- Now we got the APP ID (e.g. DemoApp For App Secret Replacement; fe897d22-cebd-4ea7-8d36-9ff257ab848d
- Keep the information safe for next step
Verify the application
- Open your O365 tenant URL with < Your Tenant URL>/_layouts/15/AppInv.aspx
For example : https://XXXXXXXXXXXXXXX.sharepoint.com/_layouts/15/AppInv.aspx
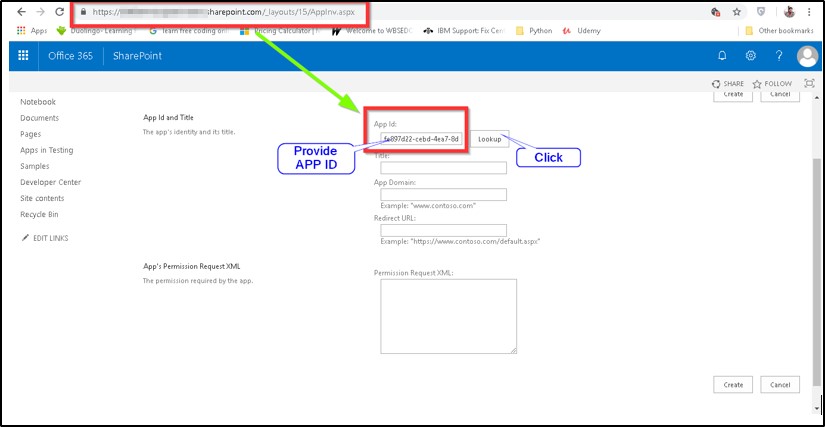
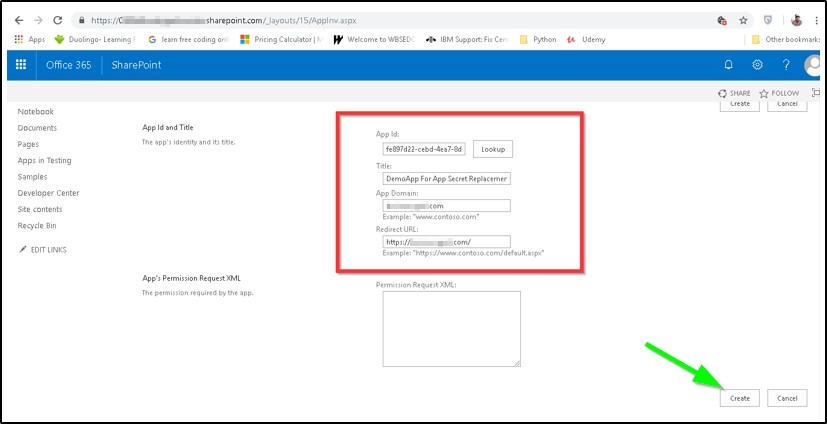
Generate a New App Secret for Three Years
- Open the PowerShell ISE console and create client ID variable with the following line,
- Import PowerShell module for O365
import-module MSOnline
$msolcred = get-credential
connect-msolservice -credential $msolcred- Below script, returns three records. Replace each KeyIdin KeyId1, KeyId2, and KeyId3. You also see the EndDate of each key. Confirm whether your expired key appears there.
$clientId = fe897d22-cebd-4ea7-8d36-9ff257ab848d
$keys = Get-MsolServicePrincipalCredential -AppPrincipalId $clientId
Remove-MsolServicePrincipalCredential -KeyIds @("KeyId1"," KeyId2"," KeyId3") -AppPrincipalId $clientIdNote: Only valid for already expired App Secret
- Create and then run below PS script “PS1” to generate a new client Secret
Syntax:
$clientId = fe897d22-cebd-4ea7-8d36-9ff257ab848d
$bytes = New-Object Byte[] 32
$rand = [System.Security.Cryptography.RandomNumberGenerator]::Create()
$rand.GetBytes($bytes)
$rand.Dispose()
$newClientSecret = [System.Convert]::ToBase64String($bytes)
$dtStart = [System.DateTime]::Now
$dtEnd = $dtStart.AddYears(3)
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Symmetric -Usage Sign -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Symmetric -Usage Verify -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Password -Usage Verify -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
$newClientSecretNote: In demo app shown here, throws some exception as the App-secret is not yet expired. Please ignore if you want to simply extend the App-Secret expiration period from (default) 1 year to number of years you want.
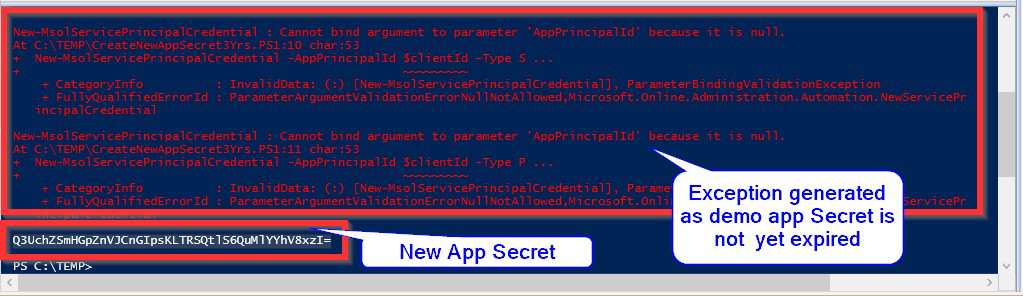
- Tested by comparing pre-captured old with new app secret for our demo app
New App Secret: Q3UchZSmHGpZnVJCnGIpsKLTRSQtlS6QuMlYYhV8xzI=
Old App secret: eWBG4M0CaaQhloPQ/OGg8zQhieTURZTVNMA4jqCFiMs=
Make change in Web.Config
- Go to your application system and locate config file
- Open with Admin privilege in notepad
- Search for “appsettings” and replace the configwith this ClientId and ClientSecret. You don’t need SecondaryClientSecret app settings.
Example:
<appSettings>
<add key="ClientId" value="your client id here" />
... other settings may be here ...
</appSettings>Ensure the App ID have full permission
- Go to URL < Your Tenant URL>/_layouts/15/AppInv.aspx
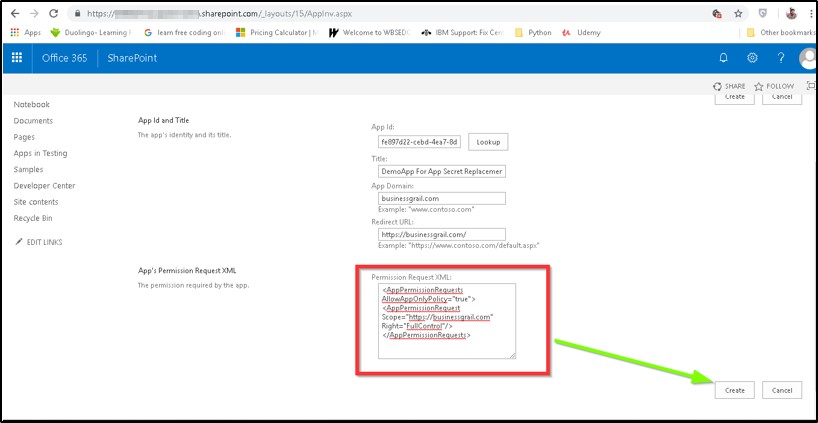
E.g. https://XXXXXXXXXXXXX.sharepoint.com/_layouts/15/AppInv.aspx - Verify below XML fragment in the text box “App’s Permission Request XML “
- Your URL would differ from demo URL
<AppPermissionRequests AllowAppOnlyPolicy="true"><AppPermissionRequest Scope="https://XXXXXXXXX.com" Right="FullControl"/></AppPermissionRequests>Note : If XML entry not, present or FullControl not mentioned, then you need to enter and click on create again to update permission
Hope, this will help you on the context. Please keep on visiting our Blog for more interesting contents.
























Hello, do you know if there’s a way to go beyond the 3 year limit on expiration?
As of now, Microsoft has not documented and mentioned how far you can extend though the new portal https://portal.azure.com/#home allows you to define as infinite, but we are yet to see if that really works because we still need to wait beyond 3 years to figure out. Hope that helps.