Unlocking The Power of Data Governance: Mastering Microsoft Purview Security Best Practices
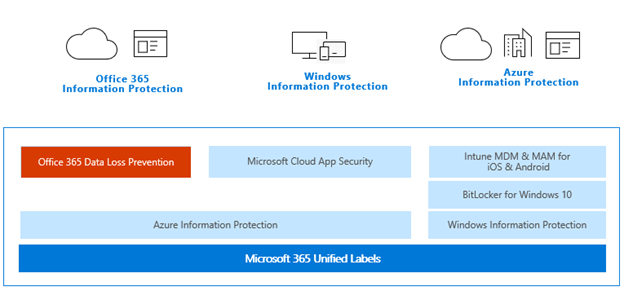
1. Microsoft Information Protection (capabilities)
Sensitivity Labels:
With sensitivity labels, you can classify and help protect your sensitive content. Protection options include labels, watermarks, and encryption. Sensitivity labels use Azure Information Protection.
Data Loss Prevention:
With DLP policies, you can identify, monitor, and automatically protect sensitive information across Office 365. Data loss prevention policies can use sensitivity labels and sensitive information types to identify sensitive information.
Sensitive Information Types:
Microsoft 365 includes many sensitive information types that are ready for you to use in DLP policies and for automatic classification with sensitivity and retention labels.
Office 365 Message Encryption (OME):
With Office 365 Message Encryption, your organization can send and receive encrypted email messages between people inside and outside your organization. Office 365 Message Encryption works with Outlook.com, Yahoo!, Gmail, and other email services.
Azure Information Protection:
Azure Information Protection (sometimes referred to as AIP) helps an organization to classify, label, and optionally, protect documents and emails. Administrators can automatically apply labels by defining rules and conditions.
You may like: [Updated] Best Practices for Microsoft Azure Information Protection
2. The ways to prevent Data Loss in Cloud
- Use the strongest methods of authentication for employee access to cloud resources.
- Ensure that PCs and windows devices connect and access applications in secure ways.
- PCs and email are protected from malware.
- Permissions on cloud-based digital assets define who can access what and what they can do and are designed for least privilege access
- Sensitive and highly regulated digital assets are labeled, encrypted, and stored in secure locations
- Highly regulated digital assets are protected with permissions
- IT security can monitor security posture from central dashboards and get notified of security events for quick response and mitigation
You may also like: Learn how to proactively identify and protect your sensitive information
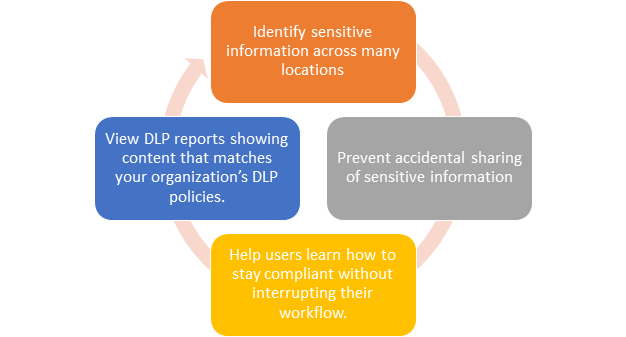
2.1 What we can do with AIP & DLP?
- Identify sensitive information across many locations, such as Exchange Online, SharePoint Online, OneDrive for Business, and Microsoft Teams. For example, you can identify any document containing a credit card number that’s stored in any OneDrive for Business site, or you can monitor just the OneDrive sites of specific people.
- Prevent the accidental sharing of sensitive information. For example, you can identify any document or email containing a health record that’s shared with people outside your organization, and then automatically block access to that document or block the email from being sent.
- Monitor and protect sensitive information in the desktop versions of Excel, PowerPoint, and Word. Just like in Exchange Online, SharePoint Online, and OneDrive for Business, these Office desktop programs include the same capabilities to identify sensitive information and apply DLP policies. DLP provides continuous monitoring when people share content in these Office programs.
- Help users learn how to stay compliant without interrupting their workflow. You can educate your users about DLP policies and help them remain compliant without blocking their work. For example, if a user tries to share a document containing sensitive information, a DLP policy can both send them an email notification and show them a policy tip in the context of the document library that allows them to override the policy if they have a business justification. The same policy tips also appear in Outlook on the web, Outlook, Excel, PowerPoint, and Word.
- View DLP reports showing content that matches your organization’s DLP policies. To assess how your organization is complying with a DLP policy, you can see how many matches each policy and rule has over time. If a DLP policy allows users to override a policy tip and report a false positive, you can also view what users have reported.
2.2 Locations to create DLP/AIP Policies
A DLP policy can find and protect sensitive information across Office 365, whether that information is in Exchange Online, SharePoint Online, OneDrive for Business, or Microsoft Teams, or On-premises. You can choose to protect content in Exchange email, Microsoft Teams chats and channels, and all SharePoint or OneDrive libraries, or select specific locations for a policy. Microsoft Information Protection provides the comprehensive solution irrespective of where the data resides.
2.3 Protect content using rules
- Conditions:the content must match before the rule is enforced. For example, a rule might be configured to look only for content containing Social Security numbers that’s been shared with people outside your organization.
- Actions:that you want the rule to kick-in automatically when content matching the conditions is found. For example, a rule might be configured to block access to a document and send both the user and compliance officer an email notification.
Information Protection Best Practices
- Protect sensitive and highly regulated digital assets with Azure Information Protection labels. Determine three levels of data protection and deployed Azure Information Protection labels that users apply to digital assets. For trade secrets and other intellectual property, use Azure Information Protection sub-labels in a scoped policy for highly regulated data that encrypts content and restricts access to specific security groups.
- Prevent intranet data leaks with Office 365 Data Loss Prevention. Implement Data Loss Prevention policies for Exchange Online, SharePoint Online, and OneDrive for Business to prevent users from accidentally or intentionally sharing sensitive data.
- Prevent device data leaks Windows Information Protection. Implement Windows Information Protection (WIP) to protect against data leakage through Internet-based apps and services and enterprise apps and data on enterprise-owned devices and personal devices that employees bring to work.
- Cloud monitoring with Microsoft Cloud App Security. Implement Microsoft Cloud App Security to map their cloud environment, monitor its usage, and detect security events and incidents.
- Device management with Microsoft Intune. Use Microsoft Intune to enroll, manage, and configure access to windows devices and the apps that run on them. Device-based conditional access policies also require approved apps and compliant PCs.
3.1 Plan for Information Protection
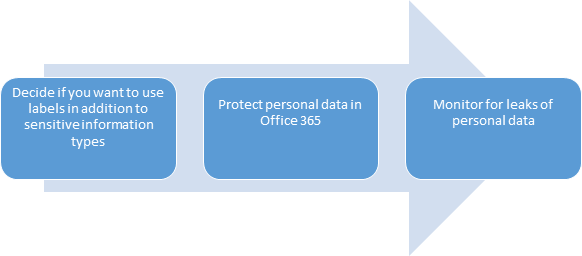
This demonstrates how to protect sensitive data that is stored in Office 365 services. It includes prescriptive recommendations for discovering, classifying, protecting, and monitoring personal data.
Step 1 : Decide to Classify, protect, and monitor personal data in Office 365 and other SaaS apps
Step 2 : Use Content Search to find personal data (Optional)

Step 3 : Search for sensitive information types using Content Search

Step 4 : Develop/Customize/Create labels that includes personal data
Example of classification & Labeling
| Label name | Description |
| Personal | Non-business data, for personal use only. |
| Public | Business data that is specifically prepared and approved for public consumption |
| Customer data | Business data that contains personal identifiable information. Examples are credit card numbers, bank account numbers, and social security numbers |
| HR data | Human Resource data about employees, such as employee number and salary data. |
| Confidential | Sensitive business data that could cause damage to the business if shared with unauthorized people. Examples include contracts, security reports, forecast summaries, and sales account data. |
| Highly confidential | Very sensitive business data that would cause damage to the business if it was shared with unauthorized people. Examples include employee and customer information, passwords, source code, and pre-announced financial reports. |
Step 5 : Apply Label & Priorities Auto-apply Label
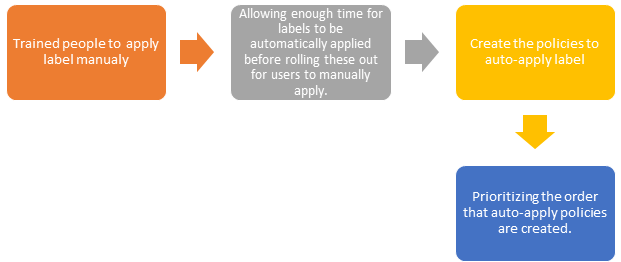
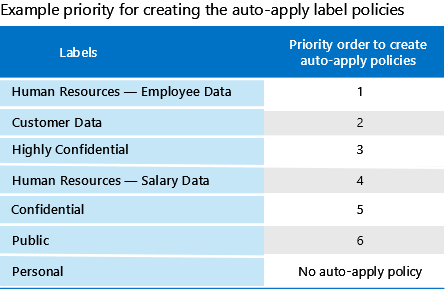
Step 6 : Apply protection to sensitive data
Example protection levels that can be configured with DLP policies
| Protection level | DLP configuration for documents | Benefits and risks |
| Awareness |
|
|
| Prevent external sharing |
|
|
| Prevent internal and external sharing |
|
|
Step 7 : Site and library-level protection
Permissions for SharePoint and OneDrive for Business libraries:
Use permissions in SharePoint to provide or restrict user access to the site or its contents. Add individual users or Azure Active Directory groups to the default SharePoint groups. Or, create a custom group for finer-grain control.
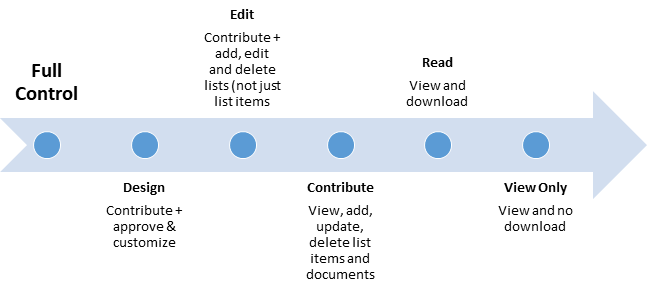
| Type of sharing | Prevention for external users | Notifications |
|
|
|
Device access scenarios and dependencies:
| Objective | Only allow access from specific IP address locations | Prevent users from downloading files to nondomain joined devices | Block access on nondomain joined devices | Prevent users from downloading files to non-compliant devices | Block access on noncompliant devices |
| SharePoint admin center | x | x | x | x | x |
| Azure Active Directory | x | x | x | x | |
| Microsoft Intune | x | x |
Step 8 : Monitor for leaks of data
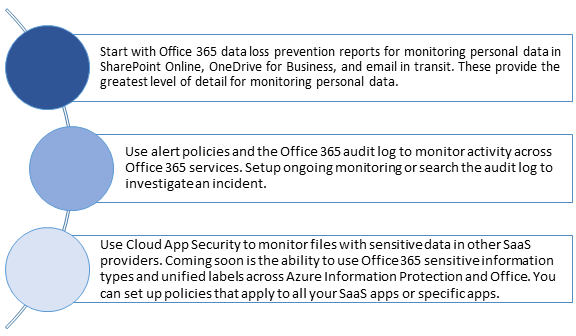
DLP Reports:
- Focus on specific time periods and understand the reasons for spikes and trends.
- Discover business processes that violate your organization’s DLP policies.
- Understand any business impact of the DLP policies.
- View the justifications submitted by users when they resolve a policy tip by overriding the policy or reporting a false positive.
- Verify compliance with a specific DLP policy by showing any matches for that policy.
- View a list of files with sensitive data that matches your DLP policies in the details pane.
3.2 Deployment Roadmap
Prepare Tenant to use AIP
- The user accounts and groups will be used by Azure Information Protection to authenticate and authorize users.
Configure and deploy classification and labeling
- If you do not already have a classification strategy, review the default Azure Information Protection policy and use this as the basis for deciding what classification labels to assign to your organization data.
- Reconfigure the default Azure Information Protection labels to make any changes you need to support your classification decisions.
Azure Information Protection Default Policy
Deploying Client
- Then deploy the Azure Information Protection client or the Azure Information Protection unified labeling client to users and provide user training and specific instructions on how to select the labels.
Introduce more advanced configuration
- After a period of time, when users are comfortable labeling their documents and emails, introduce more advanced configurations.
- Prompt users for justification if they chose a label with a lower classification level or remove a label.
- Mandate that all documents and emails have a label
- Customized headers, footers, or watermarks
Prepare for data protection
- When users are comfortable labeling documents and emails, you’re ready to start introducing data protection for your most sensitive data.
- Decide whether you want Microsoft to manage your tenant key (the default), or generate and manage your tenant key yourself (known as bring your own key, or BYOK).
- Install the PowerShell module for AADRM on at least one computer that has Internet access.
- Make sure that the protection service is activated so that you can begin to protect documents and emails. If a phased deployment is required, configure user onboarding controls to restrict users’ ability to apply protection.
Configure your Azure Information Protection policy, applications, and services for data protection
- Update your labels to apply protection
- Configure services such as Exchange Online (transport rules, data loss prevention, do not forward, and message encryption) and SharePoint Online (protected libraries).
Use and monitor your data protection solutions
- Reporting for Azure Information Protection
- Client files and usage logging for the Azure Information Protection client
- Logging and analyzing usage of the Azure Rights Management service
Download the Datasheet to learn more about Netwoven’s Information Protection and Compliance service.
Download the Solution Brief to learn how Netwoven’s solution proactively identifies and protects your sensitive data.
We hope the information is of value to you. In addition, we’re offering a FREE one-hour customized workshop to help assess your current security stance, discuss common threats and best practices to counter them. Contact us here to learn more
[Updated] Best Practices for Microsoft Azure Information Protection
.























I have queries regarding microsoft dlp.
Please feel free to ask