Introduction
Protecting confidential project details and ensuring communication compliance is crucial for businesses. Microsoft Purview offers a comprehensive solution to manage and safeguard sensitive data across various workloads, including generative AI. This blog discusses the business benefits of using Microsoft Purview Communication Compliance, shares successful implementation examples, and provides practical steps for deployment.
The benefits of using Microsoft Purview Communication Compliance
- Centralizing data governance and protection helps organizations reduce risks related to data breaches and unauthorized access.
- Ensuring compliance with industry-specific regulations and standards to avoid potential fines and legal repercussions.
- Streamlining data management processes to minimize complexity and improve productivity.
- Using accurate and secure data for strategic business decisions.
Which industries should consider adopting this approach?
- A leading financial institution adopted Microsoft Purview to protect customer data and ensure compliance with financial regulations. By implementing comprehensive data classification and encryption policies, they have significantly reduced the risk of data leakage and improved their overall security posture.
- A healthcare provider utilized Microsoft Purview to safeguard patient records and comply with HIPAA regulations. Through automated data discovery and protection mechanisms, they were able to secure sensitive health information and enhance patient trust.
- A manufacturing company implemented Microsoft Purview to protect intellectual property and maintain compliance with export control laws. By deploying data loss prevention policies, they successfully prevented the unauthorized transfer of proprietary information.
In what situations can Adaptive Protection and Communication Compliance be beneficial?
Scenario 1: Suspicious Activity Detection with Sequence Analysis
Situation: An employee begins engaging in activities that indicate potential data exfiltration, such as:
- Downgrading file classification
- Obfuscating document contents
- Copying files to a USB drive
- Deleting files
Adaptive DLP Response:
- Sequence detection identifies unusual patterns of activity.
- The user is assigned a moderate risk score, triggering a block with override on further file transfers.
- Microsoft Purview Communication compliance alerts security teams to review recent internal messages for indications of intent to exfiltrate data.
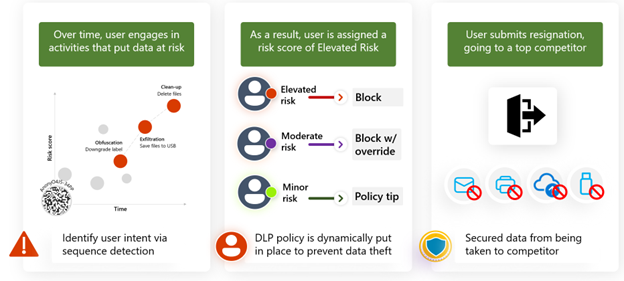
Scenario 2: High-Risk Behaviour Leading to Elevated Risk Score
Situation: An employee, previously under moderate risk, attempts to upload confidential files to an external cloud service (e.g., personal Google Drive, Dropbox).
Adaptive DLP Response:
- The user is assigned an elevated risk score, resulting in an automatic block on file transfers.
- The security team receives real-time alerts.
- A DLP policy is enforced to prevent any sensitive files from being downloaded or shared externally.
- Communication compliance scans emails, Teams, and chats to detect discussions about job resignations or data-sharing attempts.
Scenario 3: Employee Resigns and Attempts to Transfer Data to a Competitor
Situation: An employee submits a resignation and is planning to join a competitor. They attempt to send sensitive information via personal email or print important documents.
Adaptive DLP & Communication Compliance Response:
- All external file sharing, USB file transfers, and cloud uploads are automatically blocked for high-risk users.
- The user’s recent communications are analyzed for policy violations (e.g., discussing confidential information outside the company).
- Security teams are notified to conduct a final risk assessment before offboarding.
Scenario 4: Insider Threat Prevention in Mergers & Acquisitions
Situation: A senior employee in the finance department is involved in a merger discussion. They start sharing confidential financial reports in encrypted emails.
Adaptive DLP & Communication Compliance Response:
- Adaptive DLP flags encryption attempts on confidential files and blocks unauthorized recipients.
- Communication compliance identifies policy violations in email conversations discussing confidential details outside approved channels.
- The risk score increases, and restrictions escalate based on ongoing behaviour.

Unlock the Power of Enterprise Data Loss Prevention (DLP) with Microsoft Purview
Organizations face increasing challenges in protecting sensitive data due to rising cyber threats and expanded risk perimeters from remote work. This solution brief outlines a strategic approach to implementing Microsoft Purview DLP, ensuring data security, preventing unauthorized access, and maintaining regulatory compliance.
Get the Solution BriefA case study demonstrating how Netwoven’s strategy effectively prevented data exfiltration using Microsoft Purview communication compliance and Adaptive Protection
Background
In the bustling city of Metropolis, a renowned financial services firm, ABCXYZFin, prided itself on its impeccable reputation for safeguarding client information. The firm had recently taken on a high-profile project involving a major merger between two industry giants. The stakes were high, and the confidentiality of the project details was paramount.
Amidst the excitement, Alex, a diligent analyst at ABCXYZFin, received an urgent email from his manager, Mark. The email contained sensitive information about the merger, including financial projections and strategic plans. Alex knew that any leak of this information could jeopardize the entire deal and damage the firm’s reputation.
How is data exfiltration monitored and prevented?
Let us examine how he tried to exfiltrate the data. He sought to obtain all the additional details of the project in Copilot instead of directly forwarding emails.
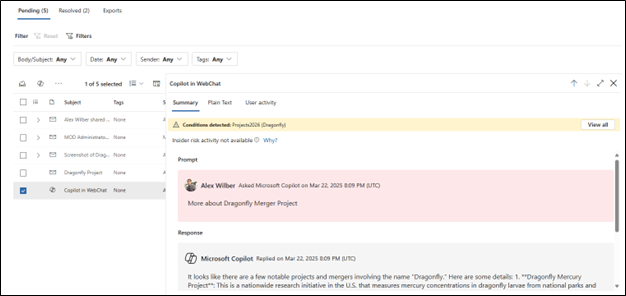
He then attempted to share the copilot information with another user who is his associate, but it was unsuccessful.
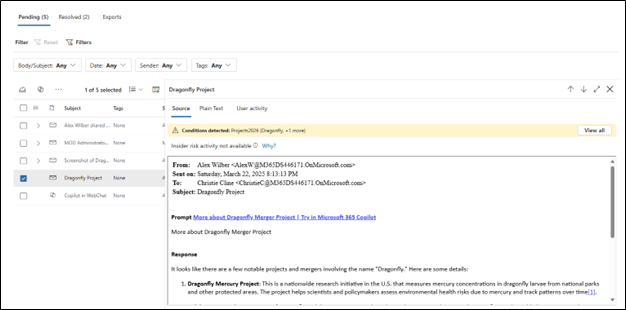
The attempt was unsuccessful and blocked when he tried to share the screenshot with the associate.
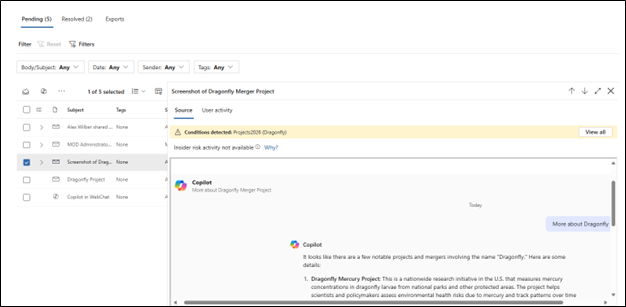
Finally, he attempted to extract data by directly sharing it from SharePoint.
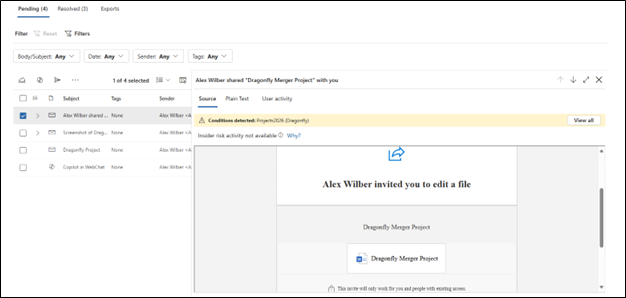
Solution – Communication Compliance Copilot
We implemented Adaptive Data Loss Prevention (DLP) protection to ensure that sensitive information remained secure. The system dynamically adjusted its policies based on the risk level of users, providing tailored protection. Alex’s email was flagged by the DLP system, which detected the presence of confidential project details. We mitigate data exfiltration through a comprehensive, multi-layered security strategy incorporating Communication Compliance features. This approach includes sophisticated Data Loss Prevention (DLP) tools that monitor and manage sensitive information across all channels. By integrating DLP with sensitive information types, we ensure the prevention of data exfiltration and minimize the risk of oversharing.
Takeaways
Integrating adaptive Data Loss Prevention (DLP) solutions and communication compliance strategies is crucial for organizations aiming to safeguard sensitive information and adhere to regulatory mandates. These solutions offer enhanced data protection, proactive threat detection, regulatory compliance, improved incident response, and comprehensive auditing capabilities. This empowers organizations to maintain a strong security posture and build trust with stakeholders. By adopting these technologies and practices, organizations can confidently address the challenges of data protection and communication compliance.






















