Introduction
In December 2024, PowerSchool, a big player in education tech, suffered from a major ransomware attack. Hackers stole sensitive information and demanded ransomware to not reveal any of this stolen data. The stolen data included students’ and teachers’ names, contact info, birthdays, Social Security numbers, health alerts, and school records.
PowerSchool paid them the ransom, but the attackers didn’t delete the stolen data. Instead, they started extortion demands targeting individual school districts. This whole chaos indicates why paying ransom to hackers is a risky business. You can’t trust them to get rid of your data or stop coming after you.
Source: PowerSchool Paid Ransom to Hackers After Breach
Some sources have mentioned ransomware groups like Medusa when talking about attacks on schools and colleges. However, we don’t have solid proof linking these groups to the PowerSchool breach. So, without an official statement, we still don’t know which ransomware group is behind the PowerSchool attack.
Scale of Cybersecurity Incidents in the Education Sector
In the recent past, the education industry has faced an increasing number of cybersecurity issues, specially in K-12 schools.
From July 2023 to December 2024, a whopping 82% of K-12 schools said they felt the effects of cyber threats. This period saw a total of 14,000 security events, with 9,300 of these confirmed cybersecurity incidents. The education sector is particularly vulnerable, with a 35% increase in attacks between 2023 and 2024. The financial implications are staggering, with the average cost of a data breach reaching $4.88 million. These incidents not only disrupt educational activities but also put sensitive student and staff data at risk.
Source: 2025 CIS MS-ISAC K-12 Cybersecurity Report
Phishing emails have emerged as one of the most common vulnerabilities, exploiting the lack of awareness and training among staff and students. Additionally, the use of outdated software remains a critical issue, as it often lacks the necessary security updates to defend against evolving cyber threats.
Key Challenges of Implementing a SOC in the Educational Sector
A full-fledged Security Operations Center (SOC) can undoubtedly serve to fortify cybersecurity. However, in most cases, it has significant challenges in a few areas.
Limited Budget
Most educational institutes experience limited funding for IT and cybersecurity infrastructure.
Lack of Skilled Professionals
Given a nationwide shortage of skilled cybersecurity professionals, educational institutions find it particularly difficult to compete with private-sector remunerations to hire effective personnel.
Fragmented IT Infrastructure
In most cases, especially in K–12 school districts, IT systems are fragmented across schools, campuses, or departments. Over a period, institutions are seen to have adopted multiple disjointed security tools (antivirus, firewall, email filtering, etc.) hindering an integrated and unified monitoring system.
Evolving Threat Canvas
The proliferation of threats -ransomware, phishing, data breaches, and insider threats poses immense challenges to the education sector.
Regulatory Compliance
Maintaining compliance with laws like FERPA, CIPA, COPPA, and increasingly HIPAA for health-related data has proven to be a great challenge in the education sector.
Continuous Monitoring
A fully operational SOC requires 24×7 staffing and monitoring to respond to incidents in real time.
Leadership Participation
As observed across industries, the governing bodies often consider cybersecurity risks with a lower priority than operational needs till such a significant breach happens.
Microsoft 365 in Education
Now look at Microsoft 365 penetration in US high schools and other academic institutions. M365 has seen significant adoption within the U.S. education sector, encompassing both K–12 schools and higher education institutions. Microsoft 365 Education is extensively utilized across U.S. educational institutions, supporting hybrid learning environments and enhancing collaboration among students and educators. Microsoft Teams, a component of Microsoft 365, has become a central tool for communication and collaboration in educational settings, facilitating virtual classrooms and administrative coordination.
Therefore, a low footprint, scalable SOC optimizing on existing M365 infrastructure could come in handy, particularly for the educational sector. In many cases, it may be beneficial if the SOC operation can be outsourced to partners taking the IT burden away from the primary focus of the academic institutes.
A Model SOC
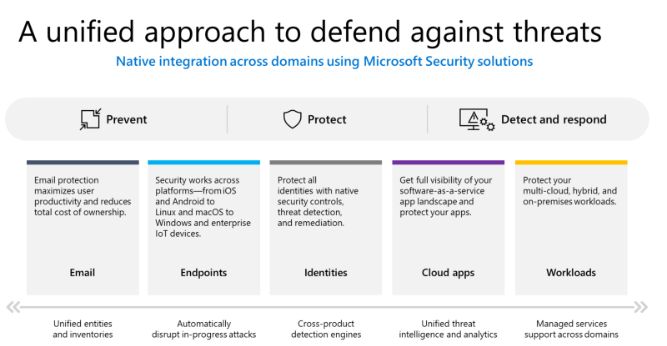
The nuts and bolts of an ideal SOC may be conceived as follows.
M365 Managed SOC Services Provider (MSSP)
For educational institutions, it could be very relevant to look at a Managed SOC Service Provider offering key security services as below.
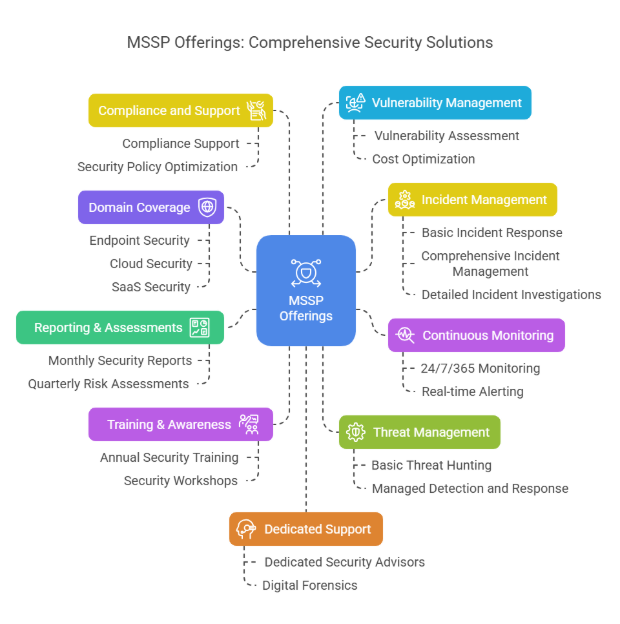
The Value Proposition of MSSP
The value of such a managed service can be appreciated when one looks at it through the lens of cost, control, scalability, and AI-driven threat response riding on the existing M365 infrastructure. It offers strategic security with effective MSSP solutions for business continuity. The highlights of such an offering are the following.
Comprehensive security
Protection of data, identities, endpoints, email and collaboration, and hybrid and cloud infrastructure.
Expertise
Deep knowledge and extensive experience in deploying Microsoft Defender XDR and Microsoft Sentinel
Risk management
Assistance in meeting your diverse regulatory, industry, or local requirements
Cost efficiency
Optimization of SIEM, XDR, and GenAI capabilities of the Microsoft Unified Security Operations platform
Proactive threat detection
Detection and response to threats quickly and efficiently
Data protection
Data security and privacy that helps you avoid penalties and maintain trust with your stakeholders

Whitepaper: Choosing the Right SOC Model in the Age of AI
Download our exclusive whitepaper, “Choosing the Right SOC Model in the Age of AI,” and discover how to evaluate in-house, MSP, MSSP, MDR, and MXDR models through the lens of cost, control, scalability, and AI-driven threat response.
Get the WhitepaperFeel free to contact Netwoven for further details on MSSP and how it utilizes MS security workloads to achieve each one of the above.























