National Institute of Standard and Technology (NIST) – is a great organization that helps us assess risk with their measurement standards and guidance. Their Cyber Security Framework (CSF) is a voluntary system consisting of standards, guidelines, and best practices geared towards cyber-security risks. NIST CSF has 4 core pillars: Identify – Protect – Detect – Respond.
| Identify | Protect | Detect | Respond |
 |  |  |  |
Microsoft embraces this with Office 365 and Azure and is certified to the objectives laid out by NIST CSF. Within these 4 core pillars from NIST CSF are categories, these map out to the various Microsoft Security & Compliance technologies. Just to acknowledge, we have used references from NIST, and Microsoft in this article.
| Identify | Protect | Detect | Respond |
 |  |  |  |
| Asset Management | Identity Management and Access Control | Anomalies and Events | Response Planning |
| Business Environment | Awareness and Training | Security Continuous | Communications |
| Governance | Data Security | Monitoring | Analysis |
| Risk Assessment | Protective Technology | Detection Processes | Mitigation |
| Risk Management Strategy | Information Protection Processes and Procedures | Improvements | |
| Supply Chain Risk Management | Maintenance |
Microsoft Services that are covered by the NIST CSF in your tenant:
| Applicability | Services in scope |
|---|---|
| Office 365 | Office Online, Exchange Online, SharePoint Online, OneDrive for Business, Delve, Azure Active Directory, Teams, Planner, Forms, PowerApps, Flow, Stream, Office Pro Plus, Security and Compliance Center, MyAnalytics, PowerBI, Advanced Compliance, Compliance Manager, Office 365 Advanced Threat Protection, Office 365 Customer Portal, Office Service Infrastructure |

You may also like: Learn how to proactively identify and protect your sensitive information
NIST CSF – Identify
Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Under this pillar, the goal is to have a better understanding of your organization’s IT environment and be able to identify which assets are at risk of attack. Then you line up these assets and their risks with the overall business goals – which can include regulatory and industry requirements governing your business; next, prioritize these assets that require your focus.
Microsoft 365 Security Solutions help us identify and manage these assets – for example, user identity, corporate data, mobile phones, cloud applications. Provisioning these in Microsoft Azure Active Directory gives us great asset and user identity management; for example, from this we get:
- Application Access
- Single Sign-on
- Device Management
With hybrid cloud and Azure AD Connect, we link on-premises directory with Azure Active Directory which gives us a common secure identity for users to access their applications.

NIST CSF – Protect
Develop and implement the appropriate safeguards to ensure the delivery of critical infrastructure services.
With this area, we focus on policies and procedures to protect data from cybersecurity attacks. Microsoft Identity Management and access control category is for managing assets and limiting authorization to devices, activities, and transactions. First, priority to protect against threats or attackers is to maintain strict, reliable, and appropriate access control – Azure Active Directory Conditional Access is a great example – it evaluates a set of fluid conditions – user, device, application, and risk – then based on the conditions it gives the right level of access control.

NIST CSF – Detect
Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event
As quickly as possible the Detect function covers systems and procedures that help you monitor your environment and detect a security breach.
- Device-based attacks – Windows Defender Advanced Threat Protection provides near-instant detection and blocking of new and emerging threats using advanced file and process behavior monitoring and other heuristics.
- Email-based attacks – Office 365 Advanced Threat Protection protects your emails, attachments, online storage, files, and the environment through a variety of technology, including Safe Attachments, Exchange Online Protection, and rich reporting and tracking insights
- Identity credential attacks – Azure Advanced Threat Protection Azure ATP takes information from logs and network events to learn the behavior of users in the organization and build a behavioral profile about them. Then it detects suspicious activities, searching for malicious attacks, abnormal behavior, and security issues and risks.

NIST CSF – Respond
Response processes and procedures are executed and maintained to ensure timely response to detected cybersecurity events
The Respond Function gives guidelines for effectively containing a cybersecurity incident once it has occurred – through the development and execution of an effective incident response plan.
- Continuing from a cybersecurity incident
- Develop and execute the incident response plan
- Azure AD Access & Usage Reports -review routinely
Download Netwoven Security and Compliance Services Datasheet Here!
Microsoft Compliance Center can assess your Compliance posture with a “Compliance Score” – this coupled with the NIST CSF Template that is imported into the Compliance Center to give fantastic guidance to organizations wishing to adopt NIST CSF. Here is how:
- Access the latest v3 (preview) Compliance Center which is in the Service Trust Portal of your tenant: https://servicetrust.microsoft.com/ComplianceManager/V3 your account needs to have ideally the Compliance Manager role added (rather than global admin).
- You see “Assessments” (a compliance template applied to your tenant), “Templates” house all the currently available compliance standards, “Action Items” (the activities you need to complete under that compliance assessment), and “Controls Info”
- Under Controls Info you’ll see the top-level summary showing the Categories from NIST CSF (after we’ve created our NIST CSF Assessment in a moment) like this:
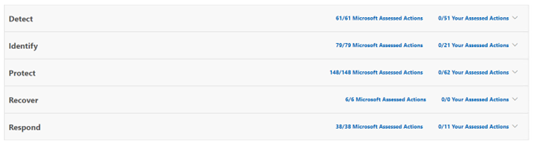
- The left-hand column is all the Microsoft tasks that they (as our Tenant ‘Landlords’) are responsible for and on the right the action that we are responsible for as subscribers (or ‘Renters’) in our tenant. Note, of course, all the Microsoft tagged items are done.
- Select “Assessments”
- Select “Add Assessment”
- Enter the Title and then Select the “NIST CSF” template
- Create a new Group and name it
- Click Save
Your screen should look something like this:
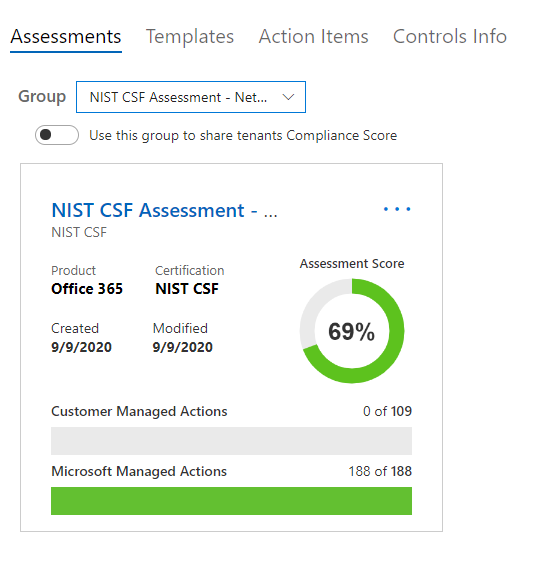
You can have multiple Assessments in your Compliance Manager.
Now click on “NIST CSF Assessment – ……” and that takes you into the assessment we just created:
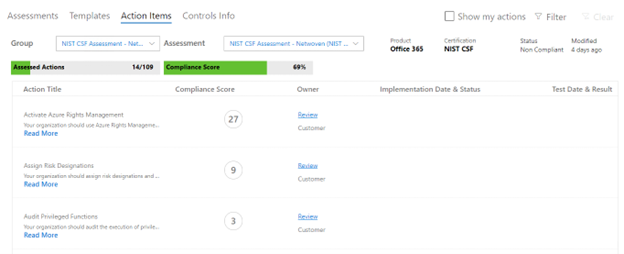
You will see columns for Action Title, Compliance Score, Owner, Implementation Date and Status, Test Date and Status. Each line item is a workstream we need to complete. Notice the Compliance Score in a circle – the higher the score the more important the workstream is and the more your score will increase by implementing it. Workstreams are arranged alphabetically.
Click on “Read More” brings up a slide-out menu that details the specific workstream details and what is needed. Also, relevant links are posted here along with links to the actual area in administration where the workstream is housed. For example:
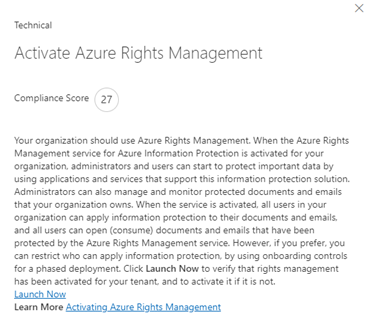
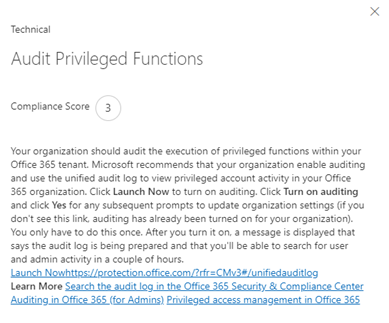
Close the slide out by clicking the X
Now click “Review” under the Owner column on a workstream:
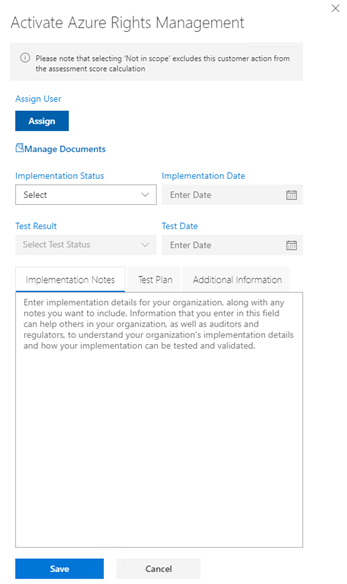
One of the many great things is to be able to assign these workstreams to colleagues – so you can split up the workload, or have the relevant workloads completed by colleagues in different departments connected with Compliance and set its priority. The Compliance Administrator can then see immediately the status of your organization’s trip to completing the assessment.
You will see “Manage Documents” this is where you upload resources specific to that workstream: deployment configurations, implementation plans, test plans etc. All the “supporting evidence” for want of a better term!
The status of the workstream implementation along with dates, test results and test dates are also collected for each one – including the notes, test plans and anything additional you feel pertinent. Do complete all these fields for each one, so if you get hit by a bus, another team member can quickly be brought up to speed in the console.
Regarding Implementation Status – having this updated is critical, when complete selected Implemented, or if the workstream is handled by a 3rd party solution or platform select Alternative Implementation.
Now work through the HIGHEST scored items with a “Not implemented” and “Failed high risk” – you’ll notice that their scores have a red ring around it, for example:
After working through those red-ringed items, next work through the highest scores down to the lowest scores as the priority.
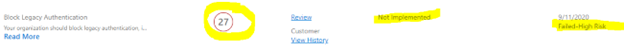
Of course, if there are some “quick wins” with small scores you can cross those off easily, then do.
I hope this has given you a good introduction to your path on compliance you desire – this incredibly powerful and labor-saving tool is a fantastic addition to your Tenant.
Download the Datasheet to learn more about Netwoven’s Information Protection and Compliance service.
Download the Solution Brief to learn how Netwoven’s solution proactively identifies and protects your sensitive data.























