Introduction
At Netwoven, we guide organizations through complex identity transitions daily. While the online guides often simplify an Okta-to-Entra ID migration into a straightforward sequence – assess, configure, migrate – our experience shows the reality is more nuanced.
The core technology switch is predictable when managed by experts. What often dictates the timeline and success of the project is not the technical complexity, but the internal readiness of the client organization.
Our goal is not just to perform a technical cutover; it is to accelerate your outcomes and mitigate business risk. This requires tackling internal organizational gaps before the migration begins.
This article details the critical, pre-migration challenges we consistently help clients solve, establishing the robust foundation necessary for a smooth and predictable transition.
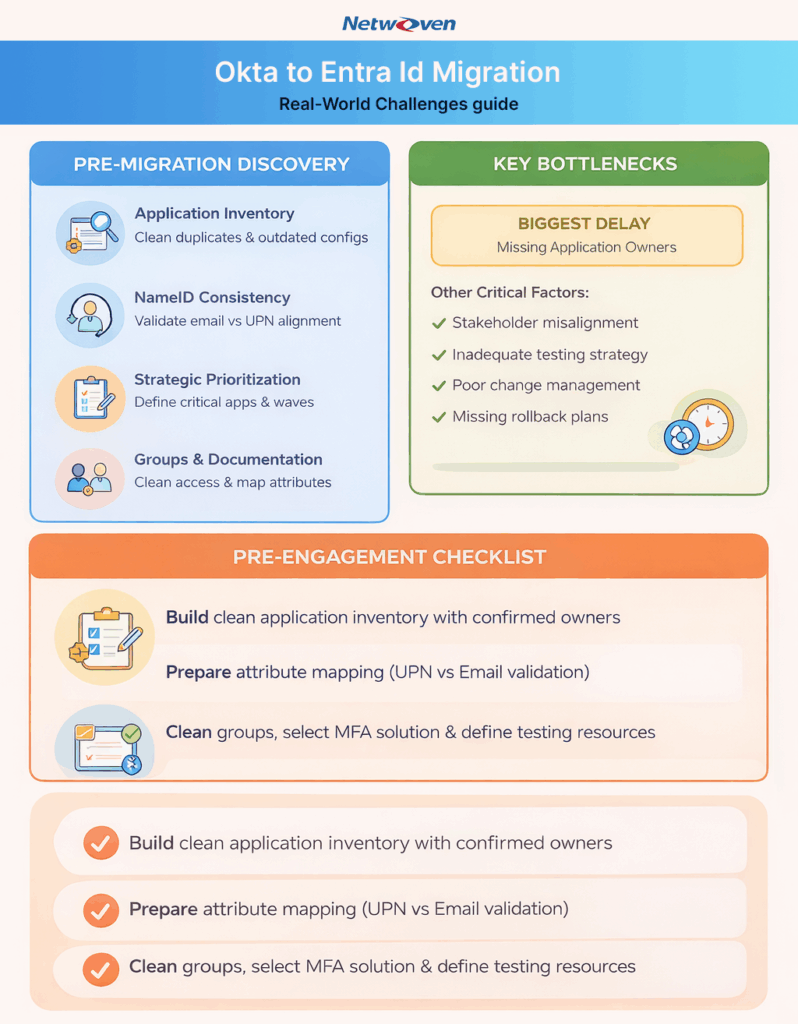
1. What We Help Uncover Before Migration
The fastest way to stall a migration project is to proceed with incomplete data. Our discovery process is designed to expose these internal gaps, ensuring our team and yours operate from a single, accurate source of truth.
The Foundation: Cleansing the Application Inventory
Many organizations are surprised by the volume of “identity debris” in their current Okta tenant: duplicate entries, outdated test configurations, or forgotten, yet still active, applications.
Our Expertise
We start by partnering with your team to conduct a comprehensive application inventory clean-up. This crucial step prevents us from wasting valuable time migrating redundant configurations and ensures our efforts are focused on business-critical systems.
Strategic Prioritization for Minimal Disruption
A successful migration requires a phased, strategic approach. Without a clear matrix defining mission-critical vs. low-impact applications, migration waves can become chaotic and risky.
Our Expertise
We work with stakeholders to define and document a precise prioritization strategy. This allows us to structure migration waves logically, ensuring high-impact applications are handled with maximum caution and resource allocation, reducing overall business risk.
The User Identifier Mismatch Trap (NameID Consistency)
A common post-migration failure involves the primary user identifier. Okta is highly flexible, often using an email address as the primary login identifier (NameID). Entra ID frequently defaults to the User Principal Name (UPN).
Our Expertise
We pre-empt this issue by performing rigorous attribute mapping and NameID consistency validation. We establish an identity consistency framework to guarantee that the application receives the exact same identifier post-migration that it expected from Okta, ensuring zero friction for end-users.
Taming Technical Documentation and Attribute Gaps
Custom-built or legacy applications often lack essential documentation (SAML metadata, Redirect URIs, required claims). If original developers have left, or if user attributes are inconsistent across systems (e.g., AD, HRMS), authentication issues are inevitable.
Our Expertise
We have proven methodologies for working backward to reverse-engineer configurations. We define the Source of Truth and manage the complexity of custom attributes, transforming unknown variables into actionable migration tasks.
Addressing Group Sprawl and Permission Mapping Risks
Okta tenants often contain hundreds of unused or poorly defined groups. The true risk lies in the lack of alignment between these groups and current business access policies. If group membership isn’t meticulously refreshed and validated, login failures due to missing permissions are a certainty.
Our Expertise
We collaborate with your teams to execute a comprehensive Group Sprawl cleanup and access structure validation. By mapping clean groups to business roles, we avoid downstream permissions issues and accelerate the final cutover.
Handling Legacy and Custom Application Dependencies
Older systems frequently have hardcoded URLs, outdated libraries, or no staging environments. These older systems present unique compatibility challenges.
Our Expertise
We specialize in the complex handling of legacy applications. We flag these early, ensure the proper isolation for extended testing, and develop specialized migration strategies that bypass hardcoded dependencies, ensuring they successfully integrate with the modern Entra ID platform.
Preparing the Post-Migration Security Posture
Removing Okta necessitates a plan for the new Multi-Factor Authentication (MFA) environment. This decision impacts user experience, policy, and security.
Our Expertise
We advise clients on the optimal security roadmap, typically recommending and implementing Microsoft-native MFA. By making this strategic choice early, we integrate the new authentication flow seamlessly into the migration plan, strengthening your security posture from day one.
2. Solving People and Process Bottlenecks
The largest time consumer in any migration is often waiting – waiting for approvals, scheduling, or clarification. We frame these internal challenges not as obstacles, but as opportunities for us to help streamline your operations.
Tackling the Single Biggest Bottleneck: Application Ownership
The most frequent stall we encounter is the “missing owner.” Applications are often orphaned, slowing progress to a crawl as we cannot proceed without clear sign-off. Finding the correct owner can take weeks per application.
Our Expertise
We provide a structured process to help clients audit and reassign application ownership quickly. By prioritizing this step, your organization validates every application’s importance, ensuring our team can move forward with maximum speed.
Strategic Stakeholder Alignment and Communication
Migration requires coordinated effort across IT, security, and business unit application owners. Misalignment results in delayed discovery interviews and inconsistent information.
Our Expertise
We partner with you to develop a robust Stakeholder Alignment and Change Management plan. This includes defining roles, clarifying the impact on their applications, and ensuring internal technical team availability for quick clarifications, preventing project stalls.
Ensuring a Low-Risk Cutover: Testing and Validation
Testing in production is unacceptable. Yet, many organizations lack dedicated staging environments, representative test accounts, or assigned testers for validation.
Our Expertise
We help you define a comprehensive testing strategy. This involves defining validation steps, assisting in the creation of test accounts that represent real business scenarios, and locking in dedicated resources from application teams to ensure immediate, thorough User Acceptance Testing (UAT) post-migration.
The Change Management Imperative
Lack of clear communication about new login URLs, new MFA methods, and expected downtime dramatically increases helpdesk load and user friction.
Our Expertise
We assist in preparing the entire Communication and Change Plan, including pre-migration announcements, user guidance material, and helpdesk readiness. This ensures your end-users are informed, minimizing confusion and supporting a smooth adoption.
Establishing a Rock-Solid Rollback Plan
Without a defined process, even small post-migration issues can disrupt business continuity. Many companies lack clear rollback steps, a temporary switch-back strategy, or a defined escalation path.
Our Expertise
We collaborate with you to define and document a comprehensive Change and Rollback Plan. This proactive approach ensures that we have a defined safety net, allowing us to proceed with confidence and immediately remediate issues without impacting the business.
3. Partnering for Success: Your Pre-Engagement Checklist
By completing these steps before our engagement begins, you maximize the efficiency of our expert services and accelerate your transition timeline.
| Area | Action Item (What You Do) | Our Value Proposition (How We Help) |
|---|---|---|
| Foundation | Build a preliminary, clean Application Inventory with owner names and priority. | We validate and formalize this inventory to create a zero-waste migration scope. |
| Ownership | Confirm or Reassign all Application Owners and ensure contact details are current. | We eliminate the project’s single biggest source of delay, ensuring rapid sign-off. |
| Data Mapping | Prepare your current attribute usage for key apps (especially UPN vs. Email). | We provide the NameID consistency framework to prevent login failures post-cutover. |
| Access | Clean Up Groups and Access Structures (delete unused/merge duplicates). | We map clean groups to business roles, accelerating cutover and preventing permission issues. |
| Security | Select your post-Okta MFA solution (e.g., Microsoft Authenticator). | We seamlessly integrate the new MFA experience into the overall authentication flow. |
| Readiness | Define and internally approve your Migration Windows and Testing Resources. | We use this commitment to create a predictable and guaranteed project timeline. |
The Netwoven Difference
An Okta to Entra ID migration is a critical project. When clients partner with us, they gain more than technical execution – they gain an organized, strategic approach designed to navigate the internal complexities.
Our expertise turns organizational challenge into operational advantage:
- We reduce risk by performing meticulous readiness assessments and implementing comprehensive rollback plans.
- We accelerate timelines by solving ownership and documentation gaps upfront.
- We guarantee identity consistency across the enterprise, minimizing user friction.
Before you start, fix the foundation. By preparing your internal environment, you ensure our partnership is focused on rapid delivery and high-value configuration, leading to a faster, smoother, and more cost-effective Entra ID migration.
Ready to accelerate your cloud identity transition with expert guidance? Contact us today for a structured migration roadmap.























