Introduction
Compliance and data security are two of the most important aspects of any business in the digital age. With the increasing number of cyberattacks, data breaches, and regulatory requirements, businesses need to adopt innovative and effective solutions to protect their data and comply with the relevant laws and standards. The role of a Chief Information Security Officer (CISO) has evolved to become more critical than ever. In this blog post, we will explore four breakthrough ideas that can help businesses achieve compliance and data security in 2024 and beyond. These ideas are innovative, yet practical, and can help you protect your data and meet your compliance requirements.
Security Orchestration, Automation, and Response (SOAR)
This is a technology that enables businesses to automate and streamline their security operations and incident response processes. This means that businesses can use tools and platforms to collect and analyse data from various sources, such as security information and event management (SIEM), endpoint detection and response (EDR), and threat intelligence. They can then execute predefined actions and workflows to remediate and resolve security incidents. SOAR can help businesses improve their efficiency, productivity, scalability of their security teams, reduce the human error and response time.
SOAR platforms can automate a wide range of security tasks, such as
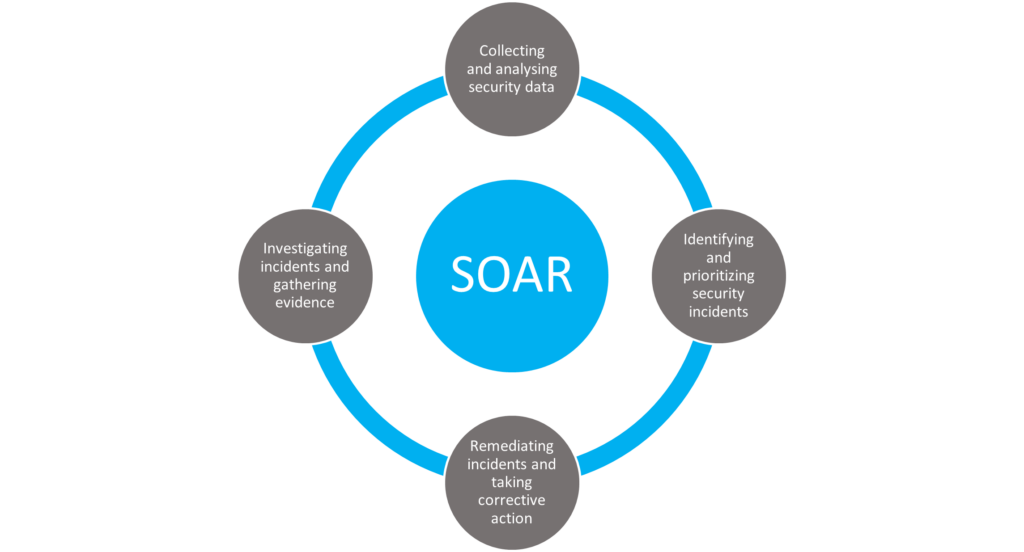
By automating these tasks, SOAR platforms can help companies to reduce the time it takes to respond to incidents and to improve the overall effectiveness of their security posture.
Artificial Intelligence (AI) and Machine Learning (ML)
As cyber threats become more sophisticated, relying solely on traditional security measures is no longer sufficient. AI and ML to enhance their security capabilities, such as threat detection, prevention and prediction, risk assessment and management, and compliance auditing and reporting. Machine learning algorithms can analyse vast amounts of data, identify patterns, and detect anomalies that might indicate a security threat. This not only strengthens your defence but also allows for a more adaptive and resilient security posture which enables organizations to respond swiftly to emerging threats, minimizing the impact of security breaches.

Ebook: Data Security and Governance: 6-Steps to kick start your initiative
This eBook offers authoritative guidance on protecting your organization’s sensitive data. It covers key steps to build a robust security framework, start a scalable and affordable data security program, optimize existing IT investments, and provides a comprehensive roadmap for enhancing data security.
Get the eBookZero Trust Architecture
With the rise of sophisticated cyber threats and the increasing number of remote workers, a new approach is needed.
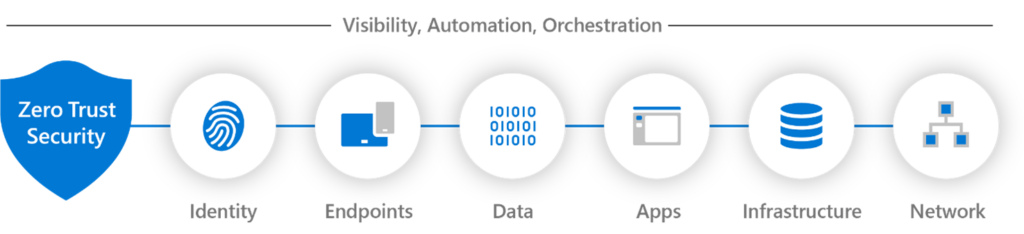
Zero Trust operates under the assumption that no one, whether inside or outside the network, can be trusted by default. Every user, device, and application must authenticate and verify its identity continuously. This model minimizes the risk of a data breach by ensuring that even if a threat actor gains access, they have limited privileges and cannot move freely within the network. This makes it much more difficult for attackers to move laterally within a network and access data.
Zero trust is a breakthrough idea for compliance and data security because it helps to protect against a wide range of threats, including insider threats, supply chain attacks, and ransomware attacks.
An innovative approach to embracing the zero-trust model involves incorporating multi-factor authentication (MFA). MFA requires users to provide two or more factors of authentication, such as a password and a one-time code generated by a mobile app. This makes it much more difficult for attackers to gain unauthorized access to your systems.
Another breakthrough idea is to use micro-segmentation. Micro-segmentation breaks down your network into small segments, and then isolates those segments from each other. This means that if an attacker is able to breach one segment of your network, they will not be able to access other segments.
Implement Blockchain for Immutable Data Integrity
Blockchain technology, known for its role in cryptocurrencies, has applications beyond the financial sector. One groundbreaking idea for improving data security is leveraging blockchain for immutable data integrity.
By storing critical data in a decentralized, tamper-proof ledger, CISOs can ensure that information remains unaltered and trustworthy. This not only enhances data integrity but also provides a transparent and auditable record of all transactions, facilitating compliance with regulatory requirements.
Webinar: Discover, Protect, and Manage Your Sensitive Data Using Microsoft Purview. Watch Now.
Conclusion
As the role of technology continues to expand in the business landscape, CISOs must constantly seek innovative solutions to address the evolving challenges of compliance and data security. Embracing a Zero Trust Architecture, leveraging AI for threat detection, implementing blockchain for data integrity, and integrating automated compliance monitoring are four breakthrough ideas that can redefine the approach to safeguarding sensitive information. By staying at the forefront of technological advancements, CISOs can ensure that their organizations are well-equipped to navigate the complex and ever-changing landscape of data security and compliance.























