Introduction:
Let me get into the context of adding an Azure AD app into the M365 launcher at the onset. As you know, an Azure AD app can potentially enjoy different levels of access into your tenant and hence may need to be added into the app launcher carefully. In our case, we were dealing with a Governance application (Govern 365) having the ability to provision and monitor various Office 365 workloads such as SP Sites, O365 Groups, MS Teams etc.
The formal touch points of services for our Azure AD app can be summarized as follows.
- Application authentication and authorization
- User authentication and authorization
- SSO using federation or password
- Role-based access control – Use the directory to define application roles to perform role-based authorization checks in an application
- OAuth authorization services – Used by Microsoft 365 and other Microsoft applications to authorize access to APIs/resources
- Directory schema extension attributes – Extend the schema of service principal and user objects to store additional data in Azure AD
Given the access sensitivity required for the app, we faced different requirements for adding the app to launcher as was warranted by customer’s IT policy.
There are customers using the product in trial mode would need the app to be made available only to a limited set of users for testing and evaluation purposes.
There are other customers who are not using Premium Azure Active Directory (level 2, with Dynamic Groups), but needing it to be available tenant wise.
To summarize, we needed to have the following flexibilities for adding the app to the launcher.
- Limited list of named users
- All tenant users (without dynamic AAD group)
- All tenant users (with dynamic AAD group)
This article provides step-by-step details for adding the Govern 365 app or any other Azure AD app tile to the M365 application launcher for each of the above options.
Option 1: Limited list of named users
This option is usually used during the trial and testing phases of deployment. During these phases, you usually have a limited set of specific users you intend to participate in the deployment, such that you do not desire to have the Govern 365 app tile shown to all tenant users. Once completed, the assigned users will automatically see the Govern 365 app tile in the M365 application launcher.
Allow Azure AD app to limited users
Azure AD app in Enterprise Azure Active Directory Application Settings
Open the app and if all users except a few are to be restricted, then set “User assignment required?” to “Yes”.
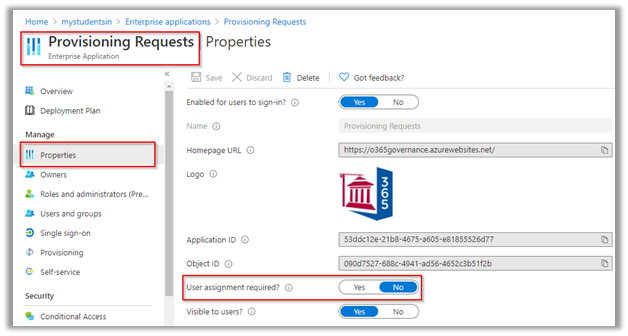
Assign specific named users to the Azure AD app in Azure AD Enterprise Application
From the left menu select “users and groups” and assign all those users to whom access is to be given.
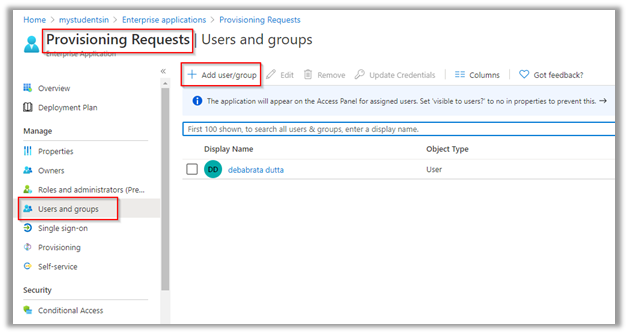
Azure AD App Tile for All Assigned Users
By doing this, the selected users will see the Azure Ad App tiles in M365 App Launcher
You may also like: Learn how to proactively identify and protect your sensitive information
Option 2: All tenant users (without dynamic AAD group)
This option is used for production deployments where dynamic AAD groups are not available, such as during UAT/Pilot scenarios, or production tenants without Azure AD Premium Level 2 licensing. In this option, settings on the provided “Provisioning Request” Azure AD enterprise application will be configured, and the app tile for Govern 365 will be added manually, then pinned to the M365 app launcher.
Azure AD app in Enterprise Azure Active Directory Application Settings
Open that app and as you are enabling all users to use the app, set “User assignment required?” to “No”
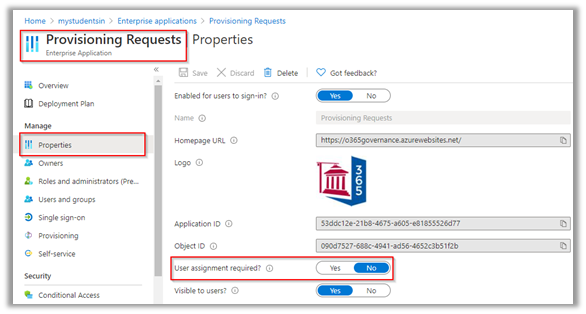
Adding a Custom App Launcher Tile for “Govern 365”
Adding custom tile:
- Sign in to the admin centre as a Global Administrator, go to Settings > Org Settings, and choose the Organization profile tab.
- On the Organization profile tab, choose Custom app launcher tiles.
- Select Add a custom tile.
- Enter a Tile name for the new tile. The name will appear in the tile.

- Enter the URL of website for the tile. This is the location where you want your users to go when they select the tile on the app launcher. Use HTTPS in the URL.
- Enter an URL of the image for the tile. The image appears on the My apps page and app launcher.
- Enter a Description for the tile. You see this when you select the tile on the My apps page and select App details.
- Select Save changes to create the custom tile.
After creating the custom tile, this should appear In App Launcher:
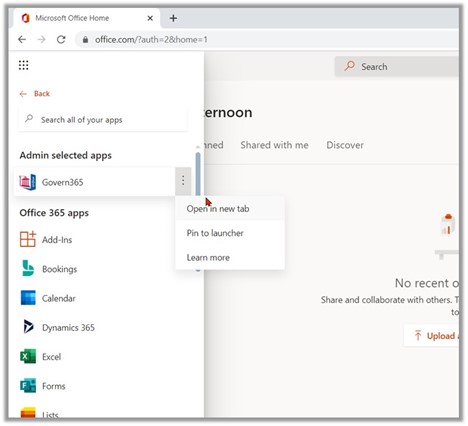
Finally, Pin it to the app launcher.
Option 3: All tenant users (with dynamic AAD group)
This option is generally only used for production deployments of Govern 365, or UAT/Pilot deployments when testing the planned production deployment configuration. To leverage the Azure AD Dynamics Groups capability, you must be a Premium Azure AD subscriber, with license level 2.
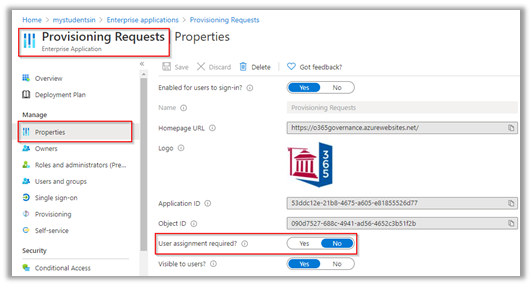
Azure AD App in Enterprise Azure Active Directory Application Settings
Open that app and as you are enabling all users to use the app please set “User assignment required?” to “No”
Create an Azure AD Dynamic Security Group
- Navigate to portal.azure.com
- Create an Azure AD group called “Internal Users Only” or any name you like.
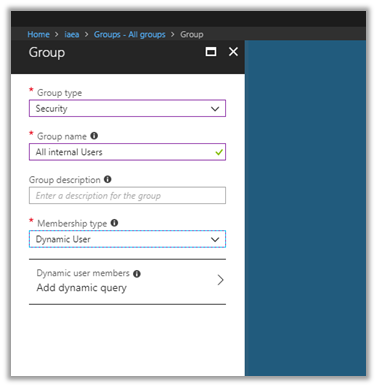
- Now you need to add all internal users to this group.
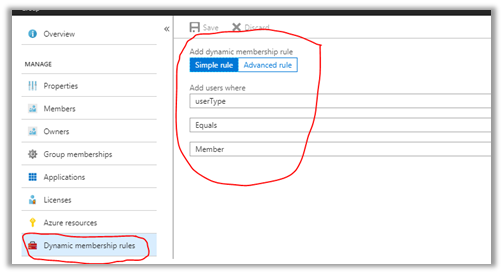
- The easy way is to use Azure AD Dynamic group membership. This will allow users to be automatically added to the group based on some dynamic criteria. For our scenario, the criteria are User Type equals Member.
- If dynamic groups cannot be created then assigned group needs to be created and the membership needs to be maintained manually.
- Find the Azure AD App from Enterprise applications
- Click on Users & Groups from the left-hand panel of the app.
- Click Add user.
- Select the group “All internal users only” from the list. Note that at least Azure AD Premium P2 license is required for adding groups to an Azure AD app
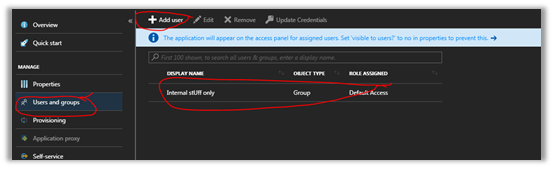
Assigned new dynamic group to the Azure AD Enterprise Application
Now only users in the “All internal users only” group will be able to access the internal application. They will be able to see Govern365 tile in M365 app launcher.
Download the Datasheet to learn more about Netwoven’s Information Protection and Compliance service.
Download the Solution Brief to learn how Netwoven’s solution proactively identifies and protects your sensitive data.
Take aways
I am aware that there is plenty of documentation available from Microsoft regarding how to add an Azure AD app to M365 launcher. Not claiming any big deal here, this is an effort to categorically document different deployment options that one might encounter to add his own custom Azure AD app given customer requirements. I believe that this can serve it’s little purpose as a ready reckoner for those who would otherwise have to grapple with tons of material to find the needle in the haystack. My 2 cents !
Let me know if you have any question.






















