Introduction
For most of the organization it’s intimidating to understand the undergoing morphing changes of Cyber Security concerns. There are increasingly dangerous threats like hacking, data thefts, ransomware checks, and new age system vulnerabilities. Cyber-attacks occur at an alarming rate raising the criticality of the situation. There are also problems with understaffed security teams and skill deficit at root levels of security. To help resolve some of these issues, Microsoft developed Security Copilot, a potent AI assistant meant to refine security measures.
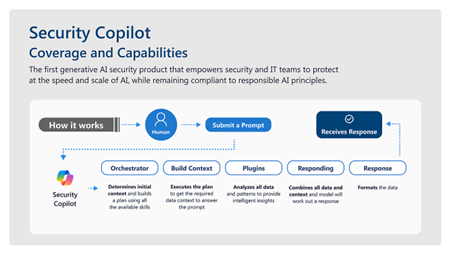
What is Microsoft Security Copilot: Its Features and Composition
Generative AI for Security
With the help of Microsoft Security Copilot, high-level natural language processing (NLP) and LLM enables security inquiries to be effortless and straightforward. Using this technology, security analysts can render information through natural words instead of writing complex grammar queries.
Integrated Plugins and Data Sources
Security Copilot functions with Microsoft inclusive of the following:
- Microsoft Defender for Endpoint XDR
- Microsoft Endpoint Management Intune
- Microsoft Entra for Identity and Access Control
- Microsoft Purview Data Security
- Microsoft Sentinel for Active Threat monitoring
Through these integrations of Microsoft products, Security Copilot can obtain vital pieces of information that most users can act upon to properly and efficiently manage incidents.
Services such as ServiceNow also integrate with Security Copilot, which allows it to access third-party features.
Stateful Experience and Promptbooks
Having a stateful experience is what makes Security Copilot stand out the most among its peers. This feature allows users to easily revert to previous sessions, allowing them to manage investigations and threats more effectively. Using Promptbooks enhances this experience further by allowing automation of workflows and enabling users to complete multi-step processes with little or no effort.
Security Copilot Vs Off-The-Shop LLMs: Comparison
Standard LLMs and its Limitations
Simple large language models are not trained well enough to tackle the intricate nature of cybersecurity work. They can churn out outputs from a pool of general knowledge but end up lacking the focus and nuance required for important decisions in security matters.
Specialized Training for Security Copilot
Microsoft has performed LoRA “Low-Rank Adaptation” fine-tuning on Security Copilot to make it stand out. This means the model can get a lot of training from cybersecurity-scenario-laden environments. With the addition of real-time threat intelligence, Security Copilot is continuously learning to tackle new problems and trends.
Showing The Difference
A side-by-side comparison of Security Copilot and a basic LLM shows these differences perfectly.
For example, Security Copilot can evaluate CVEs and dubious domains and produce insights that are simply beyond an off-the-shelf model’s reach. Real-World Application: Looking into a security incident with Security Copilot. Initial Incident Response. Imagine a security scenario where a user claims that she is unable to access her account. Security Copilot provides details of the user’s account without losing any crucial time. It shows a huge number of logins attempts failures and suspicious tries to access the same account from different devices. This is indicative of a breach in the system. Multi-Step Investigation Using Security Copilot. An analyst can, within a couple of prompts, get needed information, create hunting queries, and link alerts. For instance, an analyst can request Security Copilot to scan for security incidents inflicted on the user’s account with the aim of pattern detection. Remediation and Reporting. Security Copilot offers excellent results when making remediation scripts and summary reports at a higher level. From what has been presented, it allows teams to resolve the security problems in a quick manner while also rapidly notifying relevant stakeholders and keeping everyone updated. Replacing Office Work with Security Operations Through the Embedded copilot Experience. Microsoft Defender Integration. When integrated within Microsoft Defender, Security Copilot improves the quality of investigations concerning incidents. She auto summarizes incidents, allowing teams to answer alerts and apply scripts instantly. Microsoft Intune and Endpoint Management. Security Copilot makes managing Intune policies less complicated.
Compliance policies on device management can be created and managed instantly to reduce the window for risks.
Entra and Microsoft Identity Management Solutions
Admins work with Security Copilot in Entra to govern users and evaluate risks. It has the capability to write risk summaries, propose remedies, and enable identity governance’s execution.
Microsoft Purview and Microsoft Data Security Solutions
In terms of data security, Security Copilot helps manage data loss prevention and insider risks. It assists in a swift creation of required documents, which empower security teams to act against impending threats infringements southern.
Summary: Generative AI and The Near Future of Cybersecurity
By having Microsoft Security Copilot, breaches on cyber security are dealt with much faster and much effectively. Investigation of an incident is done in a record time with decisions made at the appropriate time.
Here’s some examples of prompts to manage a Security Operations Center (SOC) with Microsoft Security Copilot
This will help better understanding of the scope of it:
- Incident Detection and Response:
- “Identify any active security incidents in the network.”
- “Provide a summary of the latest security alerts.”
- “What are the recommended actions for the current high-severity alerts?”
- Threat Intelligence:
- “Fetch the latest threat intelligence reports.”
- “Analyze the potential impact of the latest threat on our infrastructure.”
- “Correlate recent alerts with known threat indicators.”
- Vulnerability Management:
- “List all critical vulnerabilities detected in the last 24 hours.”
- “Provide a remediation plan for the top 5 vulnerabilities.”
- “Check if any systems are affected by the latest CVE.”
- Compliance and Reporting:
- “Generate a compliance report for the last quarter.”
- “Summarize the security posture of our organization.”
- “List all incidents resolved in the past month.”
- User and Entity Behaviour Analytics (UEBA):
- “Identify any anomalous user behaviour in the last 48 hours.”
- “Provide a risk assessment for the top 10 users.”
- “Detect any unusual patterns in network traffic.”
- Automation and Orchestration:
- “Automate the response for phishing email alerts.”
- “Create a playbook for ransomware detection and response.”
- “Schedule a daily security health check.”
- Security Awareness and Training:
- “List upcoming security training sessions.”
- “Provide a summary of the latest security awareness campaign.”
- “Evaluate the effectiveness of recent security training.”

Copilot for Microsoft 365 – Unveiling the Dynamics and Capabilities
Microsoft 365 Copilot is coming soon but is your organization ready? As organizations increasingly embrace Microsoft 365 Copilot for enhanced collaboration and productivity, the strategic planning of its rollout becomes critical. Read our eBook.
Get the eBookConclusion
To learn how Microsoft Security Copilot assists in real-time response to security incidents https://aka.ms/SecurityCopilot. Microsoft will embed Security Copilot into other tools, which only increases its usefulness.























