Introduction
In today’s digital age, businesses are increasingly relying on cloud services to store, manage, and process their data. While the cloud offers unparalleled flexibility and scalability, it also introduces new security challenges as it poses some security risks that need to be addressed. Protecting sensitive information is paramount as data is becoming the lifeline of businesses, and businesses must adopt robust practices to ensure the security of their data in the cloud. In this blog post, we will explore these best practices for securing data in cloud services.
1. Choose a Reputable Cloud Service Provider
Selecting a reputable cloud service provider is the foundation of a secure cloud strategy. Research providers thoroughly, considering factors such as their security certifications, compliance measures, and reputation within the industry. Established providers often invest heavily in security infrastructure, offering a more secure environment for your data.
2. Understand Shared Security Responsibilities
It is important to understand that the cloud provider is not solely responsible for securing your data. Depending on the type of cloud service model (such as Software as a Service, Platform as a Service, or Infrastructure as a Service), the security responsibilities of the cloud service provider and the customer may vary. It is important to understand that the cloud provider is not solely responsible for securing your data.
For example, in a SaaS model, the provider is responsible for most of the security aspects, such as the application, the data, the network, and the infrastructure. In an IaaS model, the customer is responsible for most of the security aspects, such as the data, the operating system, the network, and the firewall. Businesses should understand their security responsibilities and obligations and ensure that they are met.
3. Implement Encryption (Data at Rest, in Transit, and During Processing)
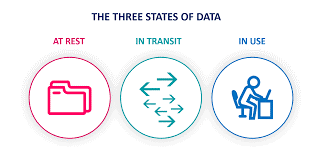
Implement robust encryption practices to protect your data at all stages. Encrypt sensitive information at rest in the cloud storage, during transit between your system and the cloud, and even during processing within the cloud environment. This ensures that even if unauthorized access occurs, the data remains unreadable without the proper decryption keys. Also, the keys should be stored in a safe location. It is also recommended to implement the Data Loss Prevention.
4. Regularly Update and Patch Systems
Software updates are important for fixing bugs, improving performance, and enhancing security. Businesses should check and update their software for vulnerabilities on regular basic and promptly apply patches, including their operating systems, applications, browsers, and antivirus programs, to reduce the risk of exploitation by malicious actors or cybercriminals. They should also enable automatic updates whenever possible and avoid using outdated or unsupported software.
5. Use strong authentication

Implement strong authentication and access controls to restrict access to your cloud data and resources. This includes using multi-factor authentication (MFA) for all users and enforcing least privilege access. MFA adds an extra layer of security by requiring users to verify their identity through multiple methods, such as a password and a mobile authentication code before accessing sensitive data. This significantly reduces the risk of unauthorized access.
6. Regular Monitoring and Auditing
Continuous monitoring and auditing of user activities in the cloud environment can help detect suspicious behavior and potential security incidents. This includes reviewing configurations, access logs, and user activities. Automated tools can assist in identifying and mitigating potential security risks, helping you stay one step ahead of potential threats.
Parallelly, regular security audits and deployment of robust monitoring and logging solutions helps detect potential vulnerabilities, weaknesses, and unusual activities in your cloud infrastructure. Set up alerts for suspicious behaviour, unauthorized access attempts, or changes in data access patterns and establish response protocols to address incidents promptly. The quicker you can identify and respond to security threats, the better you can protect your data. The most useful technique is to implement a Security Information and Event Management (SIEM) solution. Which can collect and analyse security logs from your cloud environment to identify suspicious activity and potential security threats.
7. Implement Access Controls
Enforce strict access controls to limit who can access your data at all levels, including the application level, network level, and user level. Use identity and access management (IAM) tools to grant the minimum necessary permissions to users and applications. Implement role-based access controls (RBAC) to restrict permissions based on job roles. Regularly review and update permissions as roles within your organization change. It is recommended to adapt and implement the Zero Trust Security model in your organization affectively.
8. Back Up Data Regularly
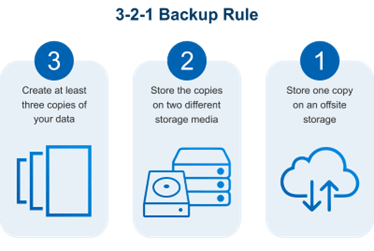
Data loss can occur due to various reasons, including accidental deletion, hardware failures, natural calamity, or cyber-attacks. Regularly back up your data to a separate, secure location and test the restoration process to ensure quick recovery in the event of a data loss incident. It is recommended to keep at least one set of backups outside of the current cloud infrastructure to ensure that they are not affected by a cloud outage or security breach.
9. Using of VPN and Firewall
A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection between a device and a network. A VPN can help businesses protect their data in the cloud by hiding their IP address, encrypting their traffic, and preventing eavesdropping and interception by third parties. Businesses should use a VPN when accessing their cloud services, especially from public or untrusted networks, such as Wi-Fi hotspots.
A firewall is a device or software that monitors and controls the incoming and outgoing network traffic, based on predefined rules. A firewall can help businesses protect their data in the cloud by blocking or allowing specific types of traffic, such as ports, protocols, or IP addresses. Businesses should use a firewall to secure their network perimeter and configure it according to their security needs and objectives.
10. Have an Incident Response Plan
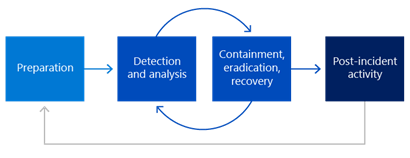
Even with the best security measures in place, there is always the risk of a security incident. Develop a comprehensive incident response plan that outlines the steps to take in the event of a security breach. This plan should include communication strategies, legal considerations, and a clear roadmap for restoring normal operations along with containment, eradication, and recovery.
11. Conduct Regular Security Training
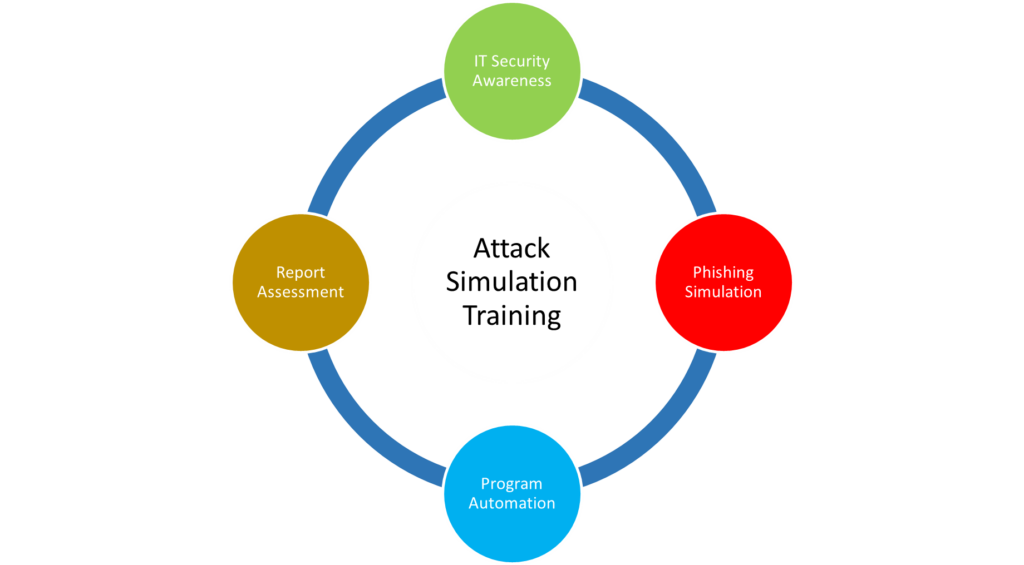
Employees are often the weakest link in the security chain, as they may fall victim to phishing, malware, or social engineering attacks, or may unintentionally expose or compromise data in the cloud. Businesses should educate their employees about the security risks and best practices of cloud computing and provide them with clear and enforceable policies and guidelines. They should also train their employees on how to detect and report suspicious or malicious activities, and how to use the cloud services securely and responsibly. The best practice is to conduct Attack Simulation Training to employees periodically.
Conclusion
Securing data in cloud services requires a proactive and multifaceted approach. By adhering to these recommended practices, organizations can fortify their security framework, safeguard critical data, and guarantee the resilience of their cloud infrastructure. The threat landscape is ever evolving, and staying informed is crucial. Regularly update your knowledge about emerging cybersecurity threats and trends. Embrace the power of the cloud securely and navigate the digital landscape with confidence.























