Introduction:
In an integrated Azure world, applications need to interact with each other often with highly empowered credentials that cannot be compromised at any cost. More often than not, you would need to borrow such credentials for accessing other applications and the IT admin would want an absolutely guaranteed impunity to any leakage.
As you know, Azure Key Vault is the most secure way to handle such situations in today’s world. There are two ways available to access the Key Vault when you are using Azure AD.
- Using ClientId and secret
- Using ClientId and certificate
Obviously, there are few pros and cons for both as well as applicability and we shall discuss the second one in this narrative.
The objective is to high light the nuances around it with reference to an actual implementation. I will try to point out few exacting details which a custom app can possibly leverage.
Background
In a recent requirement, we had to use service user credential to communicate with SharePoint portals. Since it was a highly privileged account having access to many different systems, it was imperative not to keep the credential in any unsecured way even within the context of the application. We decided to use Azure Key Vault to store the credentials. Obviously, the access to the vault is to be setup for an app instead of any individual user. Let us go through the process of how to set it up to start with.
Creation of Azure Key Vault and Add Secrets
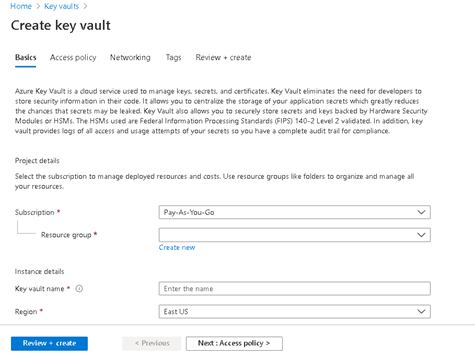
First, we need to create a Key Vault. Key Vault is like a container. We can create a single vault and add many keys under that vault. Here are the steps to create the key vault in Azure. It is well documented and I just created one!
- Login to azure portal
- Search for the service – “Key vaults”
- Click on Add(+) button

- Provide the required Resource group and other details and create the vault

- Let’s assume that we create a key vault named “SIPPTestKeyVault”
- Once vault is created, Select “Secrets” from the left panel
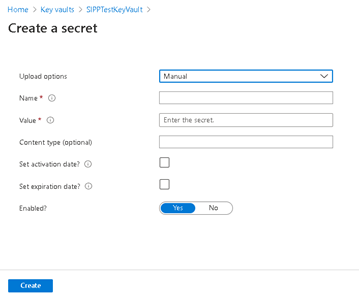
- Click on “Generate/Import(+)” button to add new secret

- Provide the details and create the secret

So far so good and we have created a key vault and also added the secrets that we want.
Access Key vault secrets programmatically
Once we are done with key vault setup, we need a way to access the secrets. We cannot access the vault keys with user credential simply because that would defeat the very basic purpose. Hence, we set the permission for an Azure AD App to access the key vault data using App authentication. Here are the 2 steps process that is to be followed:
Provide Azure AD app access to Key Vault Secrets
- Go to the vault and click on “Access policies” from left hand side navigation menu

-
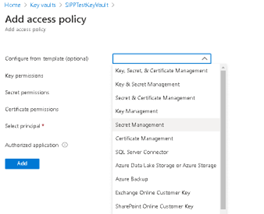
Click on “Add Access Policy”

- Select the “Secret Management” Template from the dropdown. Provide the other details:

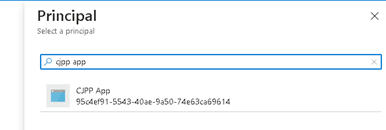
- Select the app as “principal”

- Click on “Add” button
We are done with providing the app permission to the key vault secrets. We can now use this app to access the secret programmatically.
Access the secret programmatically
-
We need to first generate the access key token with the help of the azure ad app:
private static async Task
GetAsyncTokenForKeyVaultAPI(string authority, string resource, string scope) { AuthenticationContext context = new AuthenticationContext(authority, TokenCache.DefaultShared); ClientAssertionCertificate cac = new ClientAssertionCertificate(UtilConfigInfo.ApplicationId, UtilConfigInfo.AppCertificateFromStore); AuthenticationResult result = await context.AcquireTokenAsync(resource, cac).ConfigureAwait(false); return result.AccessToken; } -
Generate the Key Vault Client
internal static KeyVaultClient AzKeyVaultClient { get { return new KeyVaultClient(new KeyVaultClient.AuthenticationCallback(KeyVaultAuth.GetAsyncTokenForKeyVaultAPI)); } } -
Using the above client, get the value of the secret
public static string GetVaultSecretValue(string secretKey) { string keyvaultSecretVal = null; try { var keyvaultSecret = KeyVaultAuth.AzKeyVaultClient.GetSecretAsync(UtilConfigInfo.AzureVaultBaseUrl, secretKey).GetAwaiter().GetResult(); keyvaultSecretVal = keyvaultSecret.Value; } catch(Exception exKey) { // Silently handle and return null as value } return keyvaultSecretVal; }
Takeaways
This was meant to be a primer for developing any custom app using the Azure Key Vault with Secrets and elaborating on the exact steps that need to be performed. The hope is you would not have to grapple with your code at all if you use this as a reference.
Look out for more here! The Key Vault can also be accesses without writing any code if the target application e.g. App Service or Function App, is hosted in Azure. Stay tuned.
Please reach out to me in case of any clarifications or suggestions























How to generate secret programmatically using .net sdk
Hi Amit,
You can use Azure Key Vault Secret client library to set or get the secret programmatically. Please go through the below documentation from Microsoft for your understanding:
https://docs.microsoft.com/en-us/azure/key-vault/secrets/quick-create-net
Please refer the following section of the code for the given console app sample:
Console.Write($”Creating a secret in {keyVaultName} called
‘{secretName}’ with the value ‘{secretValue}’ …”);
await client.SetSecretAsync(secretName, secretValue);
Console.WriteLine(” done.”);