Scenario: Need to secure application configuration credentials (like database connection/payment gateway credentials) for different environment like developer & production. Also need to manage database connection string for different type environment from outside the application for multiple application.
So, if we store the connection string in application settings, we need to change the connection string every time at the time of deployment for different environments.
But using Azure Key Vault we can handle the situation easily from a central location without touching the application.
Azure Key Vault is a cloud-hosted HSM (Hardware Security Modules)-backed service for managing cryptographic keys and other secrets.
Both Keys and secret are referred to as object and Key Vault. The object is uniquely identified within Azure Key Vault using a URL such that two objects don’t have the same URL.
Structure/Formatting of Key Vault URL
The URL includes object-type, object-name and version in that format.
https://{keyvault-name}.vault.azure.net/{object-type}/{object-name}/{object-version}
Key Vault names are selected by user and are globally unique.
Object type indicates whether it is keys or secrets.
Object name is user-specified and provided at the time of object creation. It must be unique within the Key Vault.
The object version is optional. When it is specified it identifies the specific version of the object. when not specified it will identify the latest version of the object. It is a system generated 32-character string.
Keys
The initial release of Azure Key Vault supports only RSA Keys (asymmetric cryptography)
Secrets
From a developer’s perspective, Key Vault APIs accept and return secret values as strings. Internally, Key Vault stores and manages secrets as sequences of octets (8-bit bytes), with a maximum size of 25k bytes each.
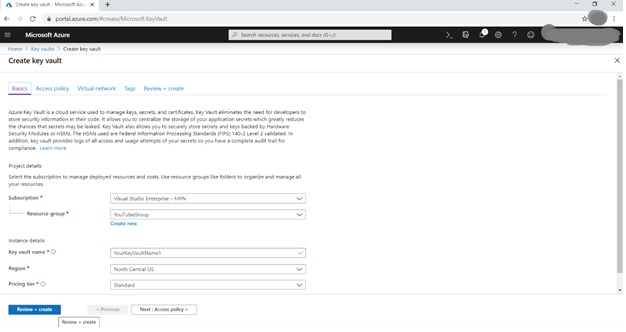
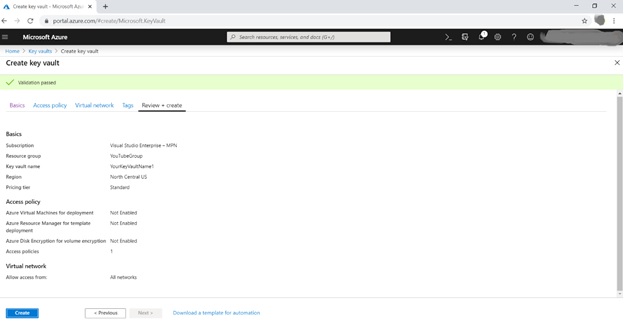
Create Azure Key Vault
Click on Add button to Create New Key Vault
Create Secrets in Azure Key Vault
Click on Secrets link to create secret within your Created Key Vault
Click on Generate/Import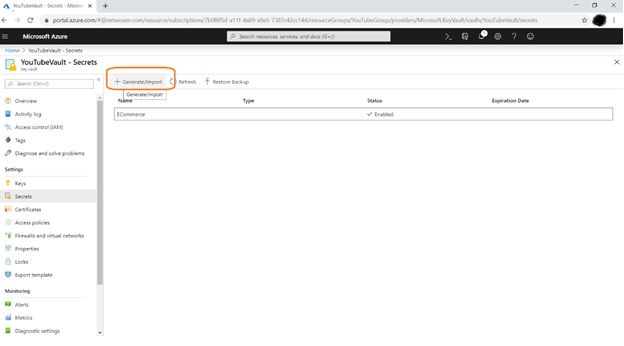
After putting the Secret Name & its Value [Example: my azure database connection string], click on Create link.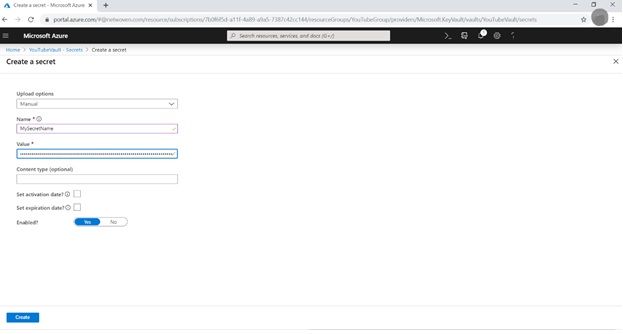
After successfully created, click on secret name to get the secret url.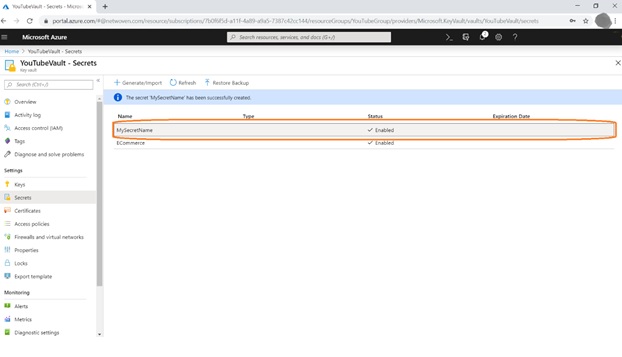
Now copy the secret Url from the Secret Identifier field.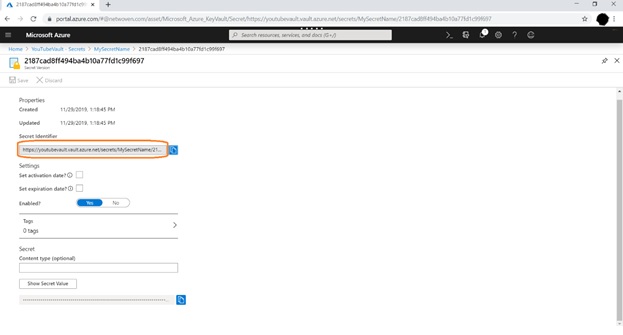
For an application like Azure Function to retrieve the secrets from vault it needs to authenticate with the vault using a token from Azure Active Directory Application.
Create an Azure Active Directive Application & get ApplicationID & Application SecretID.
Map Azure Active Directory Application with Azure Key Vault
Now go to Azure Key Vault that we have created before. Then go to Access Policy.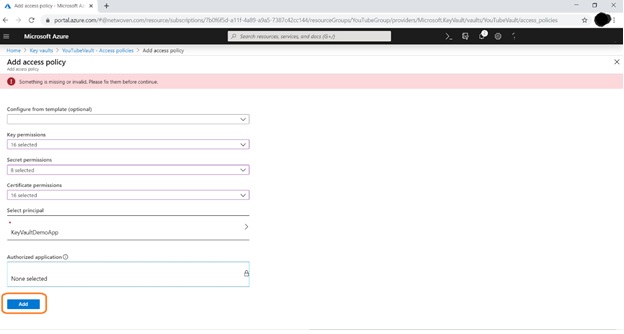
Click on Add Access Policy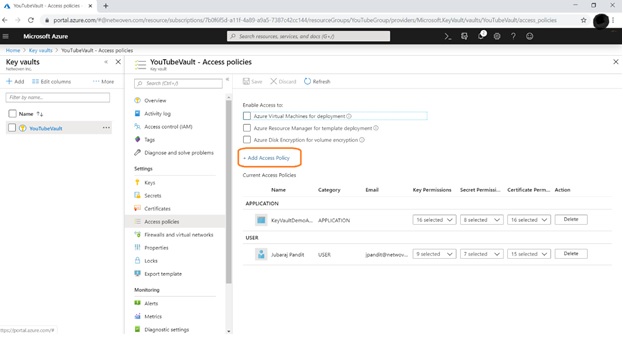
Then click on Add Button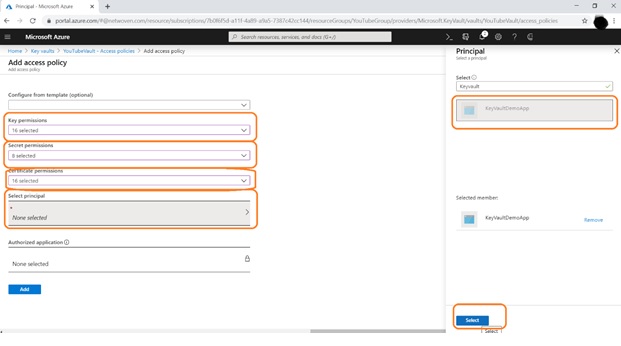
Once the access policy has been created, we can use the key vault from the client application.
Retrieve Secrets from Azure Key Vault to Client Application Like Azure Function
Now we will create a http trigger function from Visual Studio.
Install NuGet Package for Microsoft.Azure.KeyVault from NuGet Package Manager.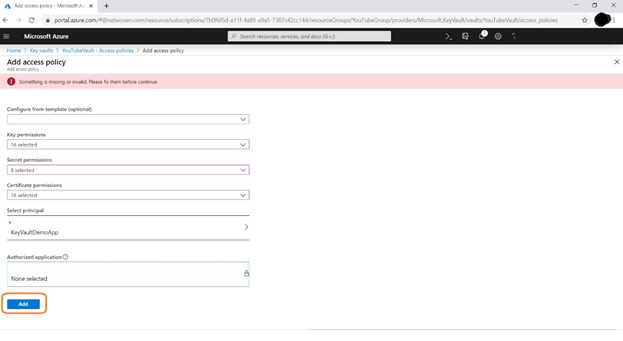
Install NuGet package for Microsoft.IdentityModel.Clients.ActiveDIrectory from NuGet Package Manager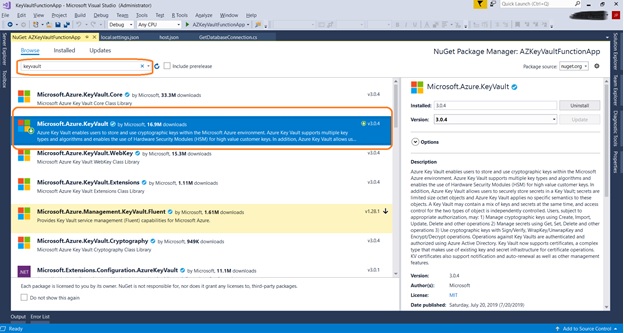
Now modify the Code as below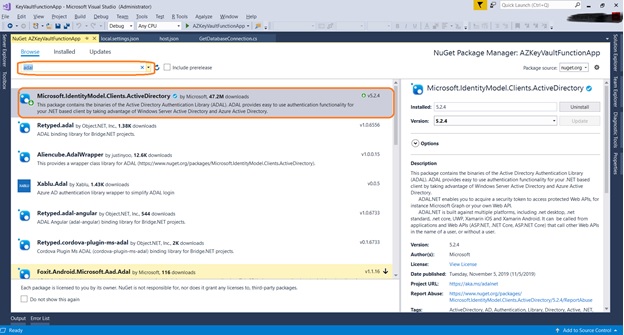
In this application, applicationId & applicationSecret are my Azure Active Directory Application’s ApplicationID & SecretKey values.
SecretIdentifier is my created Key Vault’s SecretIdetifier Url.
{secret.Value} will return my database connection string on output from Azure Function.






















