Introduction:
In today’s digital age, data has become the lifeblood of enterprises, driving innovation, competitiveness, and success. However, alongside the benefits of digital transformation, a new threat has emerged: insider risk. Insider risk refers to the potential harm posed by individuals within an organization who have authorized access to sensitive data but misuse or compromise it for personal gain, negligence, or malicious intent. This blog explores the rising concern of insider risk and highlights the importance of proactive measures to safeguard enterprise data.
The Insider Threat Landscape:
- Detection and prevention require technology, policies, and employee vigilance.
- Building a culture of security emphasizes responsibility, accountability, and reporting.
- Response and incident management plans involve collaboration and timely actions.
- Technology solutions like DLP, UBA, SIEM, and encryption enhance detection and prevention.
- Continuous monitoring, evaluation, and improvement are essential for ongoing security.
Microsoft Purview Insider Risk: Empowering Enterprises to Tackle Insider Threats
Microsoft Purview Insider Risk Management utilizes signal correlation to detect potential insider risks, including IP theft, data leakage, and security violations. It allows us to create policies for managing security and compliance. The platform prioritizes privacy by design, with default pseudonymization of users and implementation of role-based access controls and audit logs to protect user-level privacy.

By utilizing Purview’s Insider Risk Management, data governance, and analytics capabilities, organizations can gain better visibility into data access, automate processes, and ensure compliance. This enhanced visibility allows businesses to identify the departing employees who had access to sensitive data, making it easier to manage and mitigate risks effectively.
Purview’s continuous monitoring capabilities enable organizations to track and analyze access patterns in real-time. This helps in promptly identifying suspicious activities and potential data exfiltration attempts, allowing for immediate intervention.
Let’s take a closer look at a use case highlighting the significance of departing employees as insider risks and how Microsoft Purview can help mitigate these risks effectively.
When employees leave an organization, they become prime custodians of insider risk due to their access to sensitive data and knowledge of internal systems. To address this growing concern, organizations can leverage Microsoft Purview, which offers a powerful suite of tools.
The illustration below depicts the landscape of the ever-evolving insider risk threat to organizations, highlighting the importance of Insider Risk Management in triaging and addressing risks in alignment with compliance regulations.
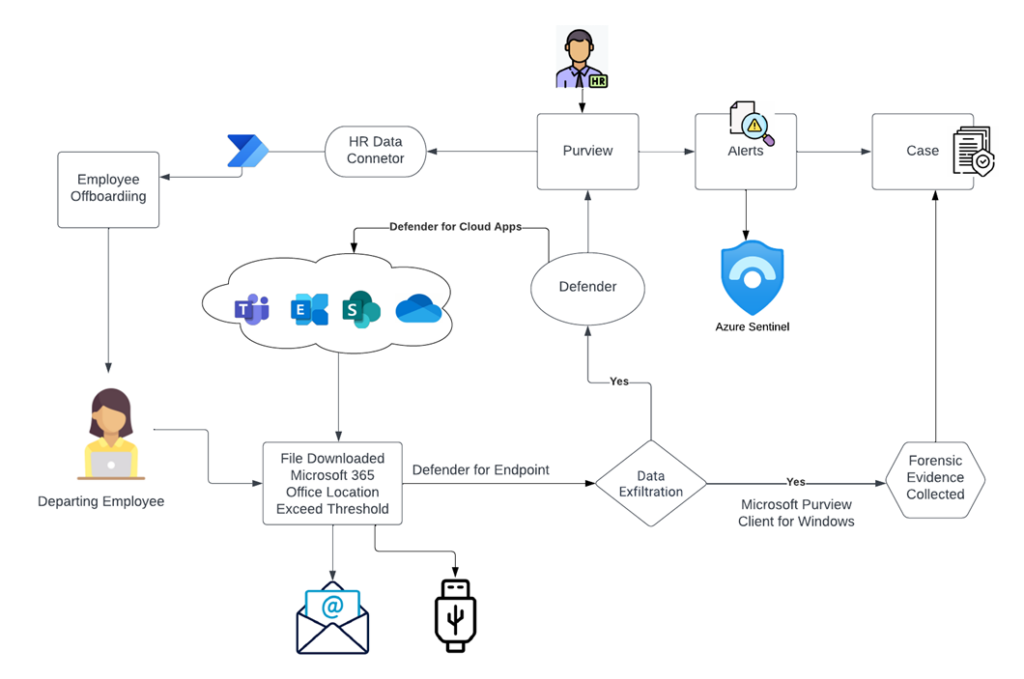
The result from Purview:
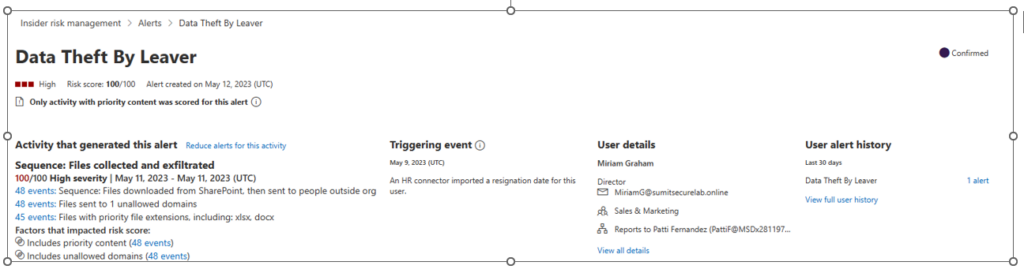
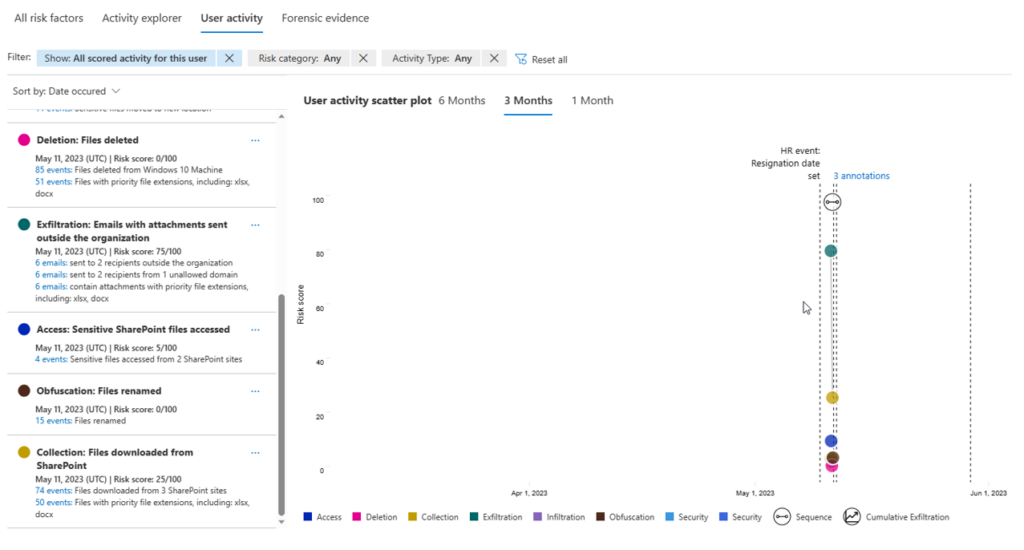

Insider Risk Management supports the import of user and logs data from third-party risk management and HR platforms, with the Microsoft 365 HR data connector enabling integration of CSV-based HR data that includes termination dates, employment history, performance-related notifications, review actions, and job level changes.

Ebook: 4 ways Microsoft Purview can help you identify and mitigate insider threats
This eBook provides expert guidance on managing insider threats, including how to identify potential threats, investigate incidents, implement remediation strategies, and establish preventive measures to protect your organization.
Get the eBookTo detect potentially risky activities, Insider risk management policies are defined, assigning users, and configuring risk indicators for alerts. The policy wizard simplifies the creation of new policies.
For example, in the context of a departing employee use case, HR connectors are connected to Microsoft Purview, and a policy is defined based on the default Departing Employee template. The required threshold and indicators, such as downloading multiple files or sending them as attachments to personal email or copying them to USB, are well-defined to trigger alerts for potential data exfiltration.
Webinar: Identify Insider Risks and Prevent Data Exfiltration using Microsoft Purview. Watch Now.
Conclusion:
Insider Risk Management plays a crucial role in detecting and mitigating insider risks within organizations. It receives signals through designated agents or Defender for Endpoint, generating alerts on the portal. These alerts are correlated with context from Microsoft Defender Cloud Apps, providing valuable insights into potential risks. By leveraging the Microsoft Purview agent installed on user systems, evidence can be captured to build a case against departing employees or support the identification of actual data exfiltration for the legal and compliance teams.
Furthermore, the integration of Insider Risk Connector with Microsoft’s renowned SIEM solution, Sentinel, enables automated triage, incident response, and streamlined workflows. This comprehensive approach enhances visibility and reduces false positives, allowing organizations to effectively address insider risk challenges.
In partnership with Netwoven, organizations can establish a well-integrated baseline and framework to strengthen their insider risk management practices. By leveraging the capabilities of Microsoft Purview Insider Risk Management and implementing tailored solutions, Netwoven helps ensure peace of mind for compliance teams and enhances the ability to combat the growing threat of insider risk breaches in today’s enterprise landscape.























