Introduction:
This is the third blog in a series about Microsoft Information Protection best practices that began with our first two blogs. Since Microsoft Purview is continually being upgraded and undergoing incredible improvements in data protection and governance, it is what we will mostly discuss here.
Microsoft Purview is a new brand that unifies the previous Azure Purview and Microsoft 365 compliance solutions and services. These technologies work together to give your company visibility into all its data assets, security, and risk management solutions. It empowers to manage end-to-end data risks and regulatory compliance while protecting and managing sensitive data across clouds, apps, and endpoints.
Data Security in Depth Approach

Organizations have multiple types of sensitive information across their data estate, both personal and organizational. The exponential growth of data, blurring of traditional organizational boundaries, and acceleration of collaboration among the workforce have made protecting and governing important data more challenging than ever.
These interactions between data and devices, apps, and other nodes can feel fragmented and lead to exposure gaps which create risks.
- Organizations don’t only need to understand what data they have but need to rationalize the use of the data across devices, apps, networks, users, etc. Understanding that context can help organizations protect against threats like data theft, and data leaks and meet regulatory requirements.
- Organizations need to take a defense-in-depth approach to data protection. They need to discover and classify the data, put protection and governance policies in place like sensitivity and retention labels, leverage user context to manage risks and prevent data loss through apps, services, and endpoints. Each of these controls (discovering, protecting, and so on) provides an additional layer of defense for the data.
The idea is to build these as layers of defense around the data – organizations can choose which layer they want to start with – but they need all to achieve comprehensive protection.
Data protection framework
We recommend a comprehensive approach to data protection – a set of products and solutions that together help keep your data safe. The Microsoft comprehensive set of solutions enables you to protect and govern your data, throughout its lifecycle – wherever it lives, or wherever it travels.
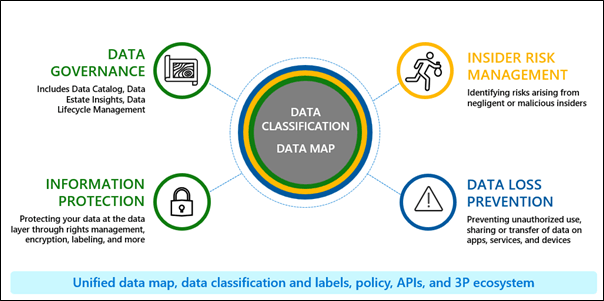
These solutions form layers of defense for the data.
- Information Protection helps you protect the data through rights management, encryption, labels etc.
- The Data Governance solutions help you govern the data through its lifecycle so that you aren’t storing data that you don’t need or storing them for longer than you need.
- As you are building the data protection strategy, you also need to manage data security risks within the organization, and Insider risk can help with that – adding yet another layer of defense.
- And then there is DLP which enables a balance between protection and productivity, ensuring the proper access controls are in place and policies are set to prevent actions like improperly saving, storing, or printing sensitive data.
Customers are in different stages on their data protection journey. We want to them to choose their own path and realize that a holistic data protection strategy would include all these different layers.
Webinar: Discover, Protect, and Manage Your Sensitive Data Using Microsoft Purview. Watch Now.
Information Protection Landscape
Microsoft Purview Information Protection is not just one feature, platform of offerings- it’s not the next generation of Azure Information Protection
It is a framework, a suite of products, that work together to provide visualization of sensitive data, lifecycle protection for data, and data loss prevention.
So, let’s review the framework piece by piece:
The foundation of this is our ability to classify data – when we light up dark data, we enable all the goodness in our platform.

Protect Sensitive Information with Microsoft Purview
Download the ebook to learn why this single unified solution helps you secure data wherever it lives, prevent data loss with the right policies, and even manage insider risk. You’ll also get details on how to use Microsoft Purview to automate data security too. Get the ebook now.
Get the eBookMicrosoft Purview Best Practices
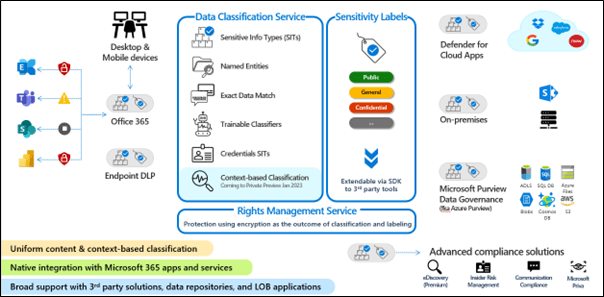
Step 1: Discover Sensitive Information and Classify
We can classify based on out-of-the-box sensitive data types, data types that are important to most of our customers, that can be identified through standard formats, checksums, their proximity to other data and so on – like SSN’s, Credit Card numbers and so on. This is a great place to start and a quick way to get a program up and running but for our sophisticated customers, it won’t be enough.
They’ll need custom-sensitive data types.
These include Regular Expressions that can be articulated using Boolean logic and Kusto Query Language such as an employee ID number.
It includes keywords including many that form a Dictionary uploaded by a customer.
It includes keywords including large numbers of keywords that form a Dictionary uploaded by a customer.
It can include Exact Data Match (EDM) where a customer can take millions of pieces of data like SSNs or Credit Card numbers and use them to inform DLP or Defender for Cloud Apps policies. The database can be updated dynamically. The database for this exact match can have up to 100 MM rows of data. This is good for say if a retailer wants to put rules around sensitive information like Credit Card numbers with strict rules around the specific numbers it has for its customers and perhaps less strict rules for Credit Card numbers identified from the out-of-the-box classifiers.
EDM does not require that the sensitive information that informs the rules be uploaded to the Microsoft cloud. Instead, it is hashed on the endpoint and only the hashes go to the cloud.
We recognize that some types of sensitive information can’t be identified by out-of-the-box, Regex, or exact data match – for these, we need machine learning – Trainable Classifiers. No data science or AI skills are needed here. We upload 50 to 500 relevant files directly from the user interface in the Compliance Portal. The solution reasons over these and then the admin reviews the guesses made by the tool as to whether each file is relevant or not. This trains the model so it can be published. Once published, the Trainable Classifier identifies sensitive information types just like the out-of-the-box and custom types. Recently we’ve added the capability to retrain the model with additional relevant documents as time goes on.
Step 2: Extend to Protection
We see how we can identify sensitive data – with sensitive data types – this gets powerful when we apply Sensitivity Labels. These labels can be applied manually by users from inside applications like those of O365. They can be applied by users from SharePoint or File Explorer. They can also be applied automatically – based on the identification of sensitive data in the document – either on a mandatory basis or through a recommendation by an application like O365 or one with information protection integrated like AutoCAD including using the SDK. If a user decides they don’t like the recommendation, they can choose a lower classification. The recommendation can be “Confidential” and the user can decide to override this and apply a “General” label. If they do this, they’ll be asked to provide a short justification that is auditable and saved for future reference.
The Labels can be applied just to identify data, or they can enforce policies like encryption, watermarking or revocation of access after a period.
This protection is part of the metadata of the file. It travels with the file throughout its lifecycle – even when it’s sent outside an organization’s environment – to a customer or partner.
The encryption policy associated with the file contains granular rights that can allow different audiences to have different permissions when accessing the protected file. For example, a document shared with an external partner may mean internal employees have permission to view, edit, copy, or print while the partner can only view the content to prevent data extraction.
Step 3: Protect Data Beyond M365
Now let’s look at how Information Protection extends beyond M365. Here’s Microsoft Defender for Cloud Apps. Defender for Cloud apps does a lot to enable security and governance, one of those things is to regulate and govern sensitive documents in third party cloud solutions like Salesforce, Box, and Google Workspace. Defender for Cloud Apps can prevent documents with sensitivity labels of selected types from being moved to cloud properties per company policy. It can also apply a sensitivity label to documents based on their sensitive content.
Most sophisticated organizations have data on-premises as well as in O365 or other cloud properties. Azure Information Protection Scanner allows our customers to inspect its on-premises repositories for sensitive information and apply labels and protection. This includes SharePoint on-premises and file shares.
Now it’s expanded Microsoft Purview Information Protection to include not just selected file types like documents and email. With Microsoft Purview Data Governance (the solutions formerly under the Azure Purview umbrella) we now cover Azure Blobs, Cosmos DB, SQL databases, and Amazon Web Service S3 repositories, providing a similar sensitivity information type and labeling experience. This is another foundational change for Microsoft information protection – making it a holistic information protection solution.
Step 4: Prevent Data Exfiltration from Endpoint Devices
Information Protection also now includes endpoint DLP. This is currently for Windows 10 and 11, Edge Chromium browser, and MacOS.
Endpoint DLP does not need additional management agents which gives it a big advantage over third-party solutions. This allows a better user and admin experience. We can regulate what goes on USB drives, what can be copied to the cloud, to network drives, printed or moved to a clipboard among other features.
Step 5: Make Your Environment MPIP Aware
Microsoft Purview unifies information protection, data governance, risk management, and compliance solutions so that customers can manage their data all from one place. Now, they can leverage that visibility across their environment to help close exposure gaps, simplify tasks through automation, stay up to date with regulatory requirements, and keep their most important asset, data, safe. And of course, happening across our stack is support for a robust ecosystem – that includes multi-cloud, hybrid, and SaaS data, as well as our third-party/partner ecosystem.
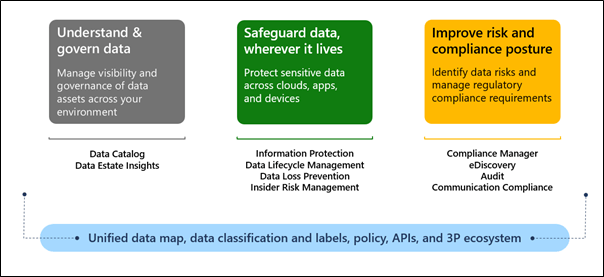
Knowing your data, protecting your data, and governing your data are all outcomes that are powered and enriched by an intelligent platform. This includes A common approach to data classification, no matter where the data resides; a unified policy configuration and management experience for IT; an analytics dashboard to monitor and remediate issues; and a set of APIs that enables the ecosystem to extend our information protection and governance capabilities to their own apps and services.
Takeaway
By adhering to Purview best practices and embracing its comprehensive data governance capabilities of Microsoft Purview, organizations can gain invaluable insights, ensure data compliance, and drive informed decision-making. As we continue to innovate and evolve, Microsoft remains committed to empowering businesses with powerful tools to harness the full potential of their data assets. Explore the world of data with Microsoft Purview and pave the way to a brighter, data-driven future. Unlock the possibilities today!






















