Introduction
This is a deep dive into Microsoft 365 Security and Compliance center OOTB reports and more importantly what potential solutions may be evolved after analysing those reports indicating the current security posture of the enterprise.
The discussion is intended as a multipart series starting with the various reports available and what they mean to the organization. Beyond that, a set of possible solution schemes are fielded based on our current experience in live projects.
Read on!
Few Important Reports
The Security & Compliance Center enables organizations to manage data protection and compliance. The prerequisite is to have the appropriate license and permission, for the security dashboard to enable checking and analysing security and threat protection status in the tenant.
Depending on what your organization’s subscription includes, the Security Dashboard includes several widgets, some of the most prominent features are the Threat Management Summary, Threat Protection Status, Global Weekly Threat Detections, Malware. The commonly used reports are described in short.
Compromised User Report
This report is available in Microsoft 365 organizations with Exchange Online mailboxes. It’s not available in standalone Exchange Online Protection (EOP) organizations.
This report shows the number of user accounts that were marked as suspicious or restricted within last 7 days. These are accounts with problematic or in compromised state. Security and compliance center through Identity and access management and unified audit logging event can track these suspicious user accounts peeping in your organization. To prevent these user account compromise microsoft recommends enforcing modern authentication aka MFA(multi factor authentication). Along with normal auditing, mailbox auditing is also supported in remediation process.
Encryption Report
The Encryption report is available in EOP (subscriptions with mailboxes in Exchange Online or standalone EOP without Exchange Online mailboxes). Organization’s security team can use this report to identify patterns and proactively apply or adjust policies for sensitive email messages.
M365 can identify sensitive information in email and with the help of mail flow rule(aka transport rule) then it can apply auto encryption. Azure rights management has a built in service named as Office 365 Message Encryption (OME) which enforces the encrypted message transport and improve this report score. Microsoft 365 also provides IRM(Information rights management) as an encryption solution that applies usage restrictions on emails along with S/MIME (Secure/Multipurpose Internet Mail Extensions) which is a certificate-based encryption solution that allows you to both encrypt and digitally sign a message. Encryption with Rights Protection can be leveraged to reduce the ability for users that receive encrypted messages to forward them to unintended recipients, print, or access them within certain time restrictions.
To view this report, open the Security & Compliance Center, go to Reports > Dashboard and select Encryption report.
You may also like: Learn how to proactively identify and protect your sensitive information
Mail flow Status Report
The mail flow status report gives the information’s for malware, spam, phishing and edge blocked messages.
View complete information pertaining to all inbound and outbound emails that met the conditions of your organization’s transport or mail flow rules. Anything not complying will be filtered and projected in this report. Take a look at this report and act to help protect against ransomware by blocking executable file types and Office file types that contain macros. Based on this report you can prevent auto-forwarding of email to external domains.
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select Malware detections in email.
Malware and Spam Detection
The malware detection report tracks the incoming and outgoing email messages and gives report about malware’s presence there. This is part of exchange online protection (EOP). The Spam detections report shows spam email messages that were blocked by exchange online protection or EOP. Messages are counted individually, not per recipient.
Using O365 Manager Plus, admins can comprehensively monitor all inbound and outbound traffic in their Exchange Online environment and get scheduled reports on spam and malware detections. Admins can also set alert notifications for early detection so they can take immediate steps to remediate any such issues. Enabling mailbox auditing is a crucial and finegrained steps to take control of malwares and spams flowing in users mailbox.
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select Malware detections/Spam detections in email.
Sent, Received and Forwarded Email Report
This report gives information about malware, spam, mail flow rules and some advanced malware detections. Precisely it contains information about incoming and outgoing mail and their mail flow status report.
Exchange Online Protection (EOP) is the core of security for Microsoft 365 subscriptions and helps keep malicious emails from reaching your employee’s inboxes.
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select Sent and received email.
Spoof Detection Report
Spoof detection report contains information about how many spoof messages have been detected. Based on this report your organization can implement anti spoofing protection by EOP.
Spoof intelligence in the Security & Compliance Center on the Anti-spam settings page helps to review all senders who are spoofing sender email addresses in your organization’s email domains or spoofing sender email addresses in external domains. We can define Spoofing Filter Rule which help limit the amount of phishing emails that are delivered.
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select Spoof detections.
Threat Protection Status Report
This report is available in both EOP(Exchange online protection) and Office 365 ATP. This report provides info about malicious content detected with email messages like files or urls those were blocked by anti-malware engine or ATP anti phising.
Depending on the type of subscription this report helps us with below facts on the context of therat management.
| EOP but not Microsoft Defender for Office 365 | Malicious email that was detected and blocked by Exchange Online Prtection (EOP) |
| Microsoft Defender for Office 365 | Malicious content, emails detected and blocked by EOP and aggregated count of unique email messages with malicious content blocked by the anti-malware engine. |
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select Threat protection status.
User Reported Message Report
The User-reported messages report provides information about email messages that users have reported as junk, phishing attempts. Audit logging must be turned on in order to capture the activities in this report.
To view the report, open the Security & Compliance Center, go to Threat management > Dashboard > User-reported messages.
Threat management > Review > User-reported messages.
URL Threat Protection Report
This report is available in Office365 ATP (advanced threat protection). This report provides summary and trend views for threats detected and actions taken on URL clicks as part of Safe Links. This report will not have click data from users where the Safe Links policy applied has the “Do not track user clicks” option selected.
Safe Links is a feature in Defender for Office 365 that provides URL scanning and rewriting of inbound email messages in mail flow,thus giving protection from malicious hyperlinks.
To view the report, open the Security & Compliance Center, go to Reports > Dashboard and select URL protection report.
In this limited sphere it is not possible to discuss all these different features in details, so I will highlight security, compliance and threat management dashboard.
Permission Requirement
Now to access the mentioned reports you must have an appropriate role assigned for both the Security & Compliance Center and the Exchange admin center.
You must be a global administrator, a security administrator, or a security reader to view the Security Dashboard.
If you are interested to explore more on permissions requirement then you can check below two links to get further details on permissions.
- https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/permissions-in-the-security-and-compliance-center?view=o365-worldwide
- https://docs.microsoft.com/en-us/exchange/permissions-exo/feature-permissions
Security Dashboard
In the Security store (https://security.microsoft.com/securescore) you can get an overview of your organization’s security aspect and areas of improvements and recommendations.
You can review and act on the security related information’s. Here is a glimpse of how it appears.
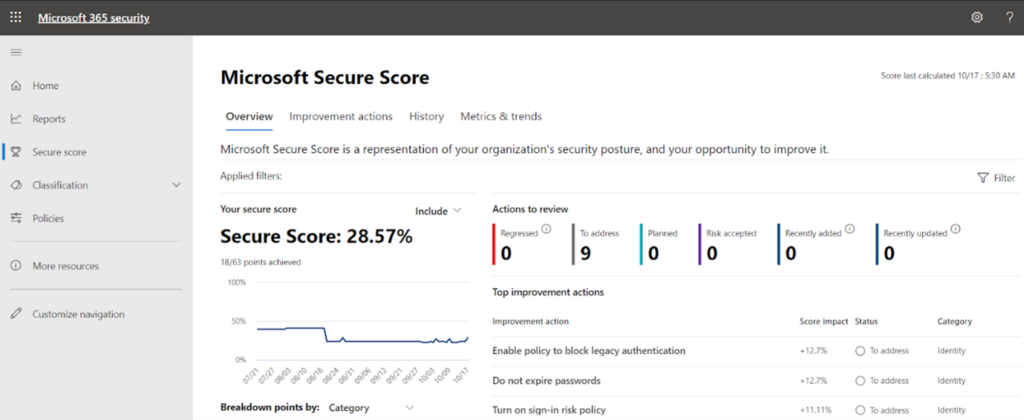
Some of the salient features we get there:
- No of threats blocked by Microsoft Information Protection.
- No of messages reported by users
- Malicious contents detected and blocked
- Email protection status and health of email security
- If subscription entails then we can monitor advanced threat protection status and mitigate them.
- Overall trends in security in terms of mail classification, high priority alerts etc.
- In a nutshell, the security center provides security administrators and risk management professionals with a centralized dashboard and specialized workspace that enables them to manage and take full advantage of Microsoft 365 intelligent security solutions for identity and access management, threat protection, information protection, and security management.
Compliance Dashboard
Compliance score (https://compliance.microsoft.com/compliancescore) surfaced later but has come up to be as extremely useful. This dashboard shows your current compliance score, helps you see what needs attention, and guides you to key improvement actions.
Some of the salient features we get:
- Continuous assessment of compliance.
- Default view showing score of compliance in terms of data protection baseline.
The compliance store dashboard looks like the one in the below image. The compliance percentage varies depending on the compliance aspect of each tenant.
Compliance dashboard provides greater visibility into the organization’s compliance posture against key regulations and standards like the GDPR, ISO 27001, NIST 800-53, and many more on the homepage. This can also help to monitor employees’ non-compliant behaviors .You can perform risk assessments and follow step-by-step guidance (mentioned in below) to enhance your compliance and privacy controls.
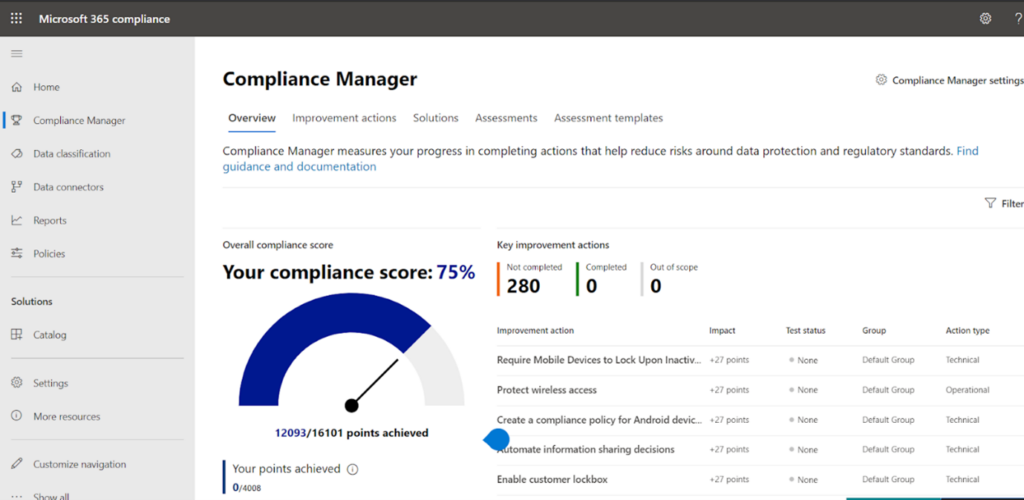
This security and compliance overall scores give holistic insight to an organization’s security perspective in Office 365 environment. The Secure Score is assigned based on the security configurations and activities enabled in an Microsoft 365 environment. As an admin you can analyze current score compared to the maximum score. Though a perfect Secure Score doesn’t provide absolute guarantee that an organization’s security won’t be breached, it does ensure that admins have taken necessary steps towards mitigating the risk of such known security breaches.
Security & Compliance Proposed Solutioning
So, now you know how the Compliance Centre may be used to assess your current security posture. But the job starts there. You need to identify and implement pertinent security solutions based on your alert level and business requirement.
Some of the baseline solutions which can be implemented to minimize the security risks and augment compliance score are highlighted below in short. Discussing those in details would be the focus of my future articles in this area.
- Creating solution for auto classifying and labelling the files based on sensitive type it contains.
- Leverage Microsoft information protection(MIP) labels to protect files and emails residing in cloud.
- Employing appropriate DLP policies to track and prevent any leak and data breach.
- Using label analytics to control how sensitive and retention labels are being used.
- Implement Conditional access policy for guest and external users in Microsoft 365 cloud apps such as Microsoft Teams, Exchange Online, and SharePoint.
- Using Microsoft cloud access security (MCAS) solution for elevating security posture by taking control of your cloud applications and services
- Using Intune’s security baselines to help secure and protect your users and devices.
- Using Defender ATP Network Protection capabilities to block unauthorized endpoint device access to cloud apps.
- Other solutions based on the assessment.
It is exciting to have M365 Security and Compliance centre to tell you where you are but the buck starts there.
Download the Datasheet to learn more about Netwoven’s Information Protection and Compliance service.
Download the Solution Brief to learn how Netwoven’s solution proactively identifies and protects your sensitive data.
We will continue to elaborate on each of these potential solutions mentioned above in subsequent articles.
Till then stay tuned, and let me know if you need any more details in particular.
























