Summary:
As the COVID-19 pandemic has been dramatically altering typical business strategies, the coming decade will be marked by significant transformation worldwide. Data protection has already started playing a massive role in IT as most people are working with corporate data in unspecified networks or home networks, creating more opportunities for cyber-criminals and unauthorized third parties.
Also Read: Best Practices for Microsoft Azure Information Protection Part-1
Digital security is all about allowing defenders to defend and protect employees, data, work, and personal safety. Data protection, which began as a regulatory requirement, is increasingly being viewed as a long-term opportunity to establish greater trust with customers and further unlock employee collaboration and productivity. An organization should understand how critical and sensitive their data is and what needs to be done to protect their environment without any downtime to their business.
The intelligent compliance solutions in Microsoft 365 help assess and manage your compliance risks and leverage the cloud to identify, classify, protect, and monitor sensitive data residing in hybrid and heterogeneous environments. In the previous blog, we discussed regarding the best recommendations provided by Azure Information Protection (AIP). In this blog, we will learn about the new model of data protection in which Microsoft has included various automation that work across all platforms.

Step 1: Discover Sensitive Information
Microsoft Information Protection provides four steps to the data protection landscape. Will discuss the entire lifecycle of protection in four phases.

You may also like: Learn how to proactively identify and protect your sensitive information
Migrate Unified Labeling
If you are still using the classic Azure Information Protection client, you must plan immediately to migrate your environment to Microsoft Information Protection Unified Labeling platform as the AIP (Classic) client has been discontinued from March 31, 2021.
 Note that, while enabling the migration, it does not change the label production capabilities till you publish a label policy. In case you have mails that are already labeled and sent internally, these labels will be visible in Outlook on the Web (formerly known as Outlook Web App). Follow the instructions here for more information.
Note that, while enabling the migration, it does not change the label production capabilities till you publish a label policy. In case you have mails that are already labeled and sent internally, these labels will be visible in Outlook on the Web (formerly known as Outlook Web App). Follow the instructions here for more information.
Discover Your Sensitive Data
If you have a heterogeneous environment and data resides in on-prem & cloud, you must extend your discovery to find sensitive information everywhere. There are various ways to execute the discovery, evaluation, and tagging, but the result is that you may have to discover a large number of documents and emails that are tagged and classify them with one or multiple labels.
Sensitive Information Type
Most businesses possess sensitive data types that are often created and used. A pattern that can be identified by a regular expression or a function defines a sensitive information category. In addition, confirmative evidence such as keywords and checksums can be used to identify the sensitive information type.
There are two types of sensitive information types:
- Built-In: Microsoft 365 comes with more than 90 built-in sensitive information types. They can be used in various policies.
- Custom: You can also create your own custom-sensitive information types to detect organization-specific content.
How sensitive information type helps to discover data?
- Run the scanner in discovery mode to create reports that check what happens when your files are labeled. It uses the sensitivity labels and discovers the documents based on the built-in sensitive info type matches in the documents.
- Run the scanner to discover files with custom sensitive information, without configuring labels that apply automatic classification. The scanner uses the conditions (custom sensitive info type) that are specified for labels.
Use Azure Information Protection Scanner to discover & classify sensitive information
AIP Scanner allows you to search your on-premises data repositories for sensitive Microsoft 365 data types and custom kinds built using keywords or regular phrases. Once the data has been found, the AIP Scanner can aggregate the results and display them in Analytics reports, allowing you to visualize your data risk and see recommendations for putting up content-based protection rules.
Usage of AIP Scanner
The AIP scanner runs as a service on Windows Server and lets you discover, classify, and protect files on the following data stores in your on-premise environment.
- UNC paths for network shares that use the Server Message Block (SMB) protocol
- NFS shares – Private Preview
- SharePoint document libraries and folders for SharePoint Server 2019 through SharePoint Server 2013. SharePoint 2010 is also supported for customers who have extended support for this version of SharePoint.
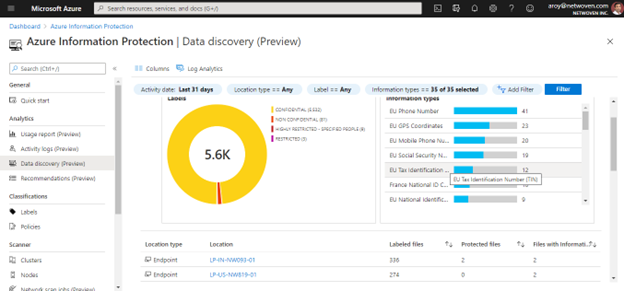
The data discovery dashboard provides information on the location of sensitive data within your organization, such as the location of documents labeled as confidential, data containing PCI, and other highly regulated information.
You can drill into file repositories (scanned by the AIP Scanner) to inspect where sensitive data resides, as well as what sensitive content they contain (such as financial information, PII, or other information, based on content inspection).
If you wish to audit raw data, export the result to Excel or Power BI, or write your own custom queries. You can do so by clicking on the Log Analytics icon from the dashboard. AIP audit log data is stored in table: InformationProtectionLogs_CL.
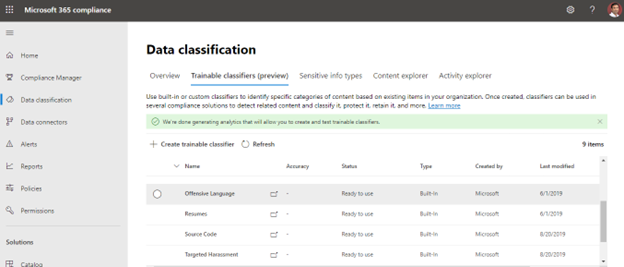
Trainable Classifier
This classification strategy is best for content that is difficult to identify using either manual or automatic pattern matching methods. This approach of classification is more about teaching a classifier to recognize an item based on what it is, rather than on the item’s components (pattern matching). A classifier learns how to identify a type of content by looking at hundreds of examples of the content you’re interested in classifying.
You start by feeding it examples that are in the category for sure. Once it processes those examples, you test it by giving it a mix of both matching and non-matching examples. The classifier then makes predictions if any given item falls into the category you’re building. You then confirm its results, sorting out the true positives, true negatives, false positives, and false negatives to help increase the accuracy of its predictions.
When you publish the classifier, it sorts through items in locations like SharePoint Online, Exchange, and OneDrive, and classifies the content. After you publish the classifier, you can continue to train it using a feedback process that is similar to the initial training process.
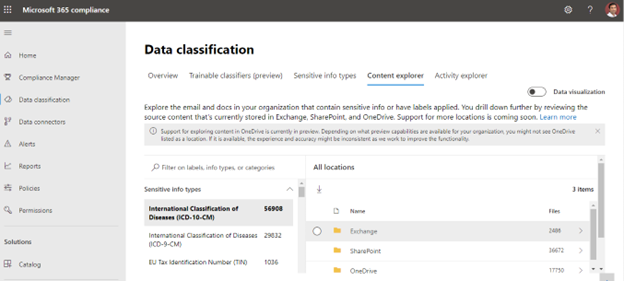
Content Explorer
Content Explorer aids in the discovery of emails and data including sensitive information and labels. You can edit the report to meet your needs and export it in CSV format for additional study.
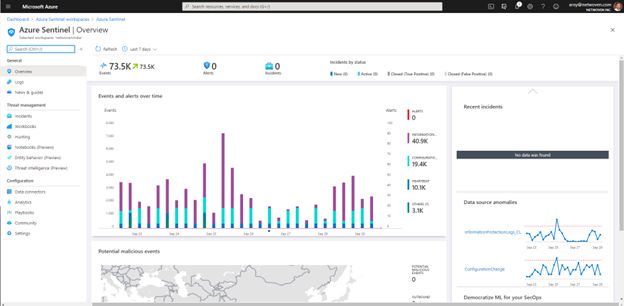
Microsoft Azure Sentinel
Microsoft Azure Sentinel is a robust Security Incident and Event Management (SIEM) solution that can help you collect security data from devices, users, apps, servers, and any cloud across your organization. Using these data sources, you can build a more complete picture of the threats that your organization faces, conduct deep threat hunts across your environment, and use the power of automation and orchestration in the cloud to help free up your security analysts to focus on their highest-value tasks.
Communication Compliance
Communication Compliance in Microsoft 365 enables enterprises to intelligently detect regulatory compliance and code of conduct violations inside their communications, such as workplace threats and harassment, and respond quickly to policy infractions. Communication Compliance introduces enhanced insights to make the review process simpler and less time-consuming, through intelligent pattern detection to prioritize alerts of repeat offenders, through a global feedback loop to improve Microsoft detection algorithms, and through rich reporting capabilities.
New features include additional third-party connectors to extend the capabilities to sources like Bloomberg Message data, ICE Chat data, and more. Additionally, the solution will see improved remediation actions through Microsoft Teams integration, such as the ability to remove messages from the Teams channel.
Step 2: Protect Sensitive Data & Information
Here we will discuss the second part of the information protection strategy which starts with the protection or classification of documentation based on the needs of the organization.
Data Protection Strategy
Sensitivity Label & Policy
Sensitivity labels from the Microsoft Data Protection framework allow you to classify and secure your organization’s data and ensures that user productivity and their ability to collaborate are not compromised.
Create labels: Create and name your sensitivity labels as your organization’s classification style for the content of different sensitivity levels. Use common names or terms that your users can understand.
Define what each label can do: You should configure the security settings associated with each label. For example, if you want to apply only titles or footers to low-sensitive content (such as a ‘Generic’ label), high-sensitive content (such as a ‘Confidential” label) should have watercolor and encryption.
Publish the labels: Once your sensitivity labels are configured, publish them using a label policy. Decide which users and groups should have labels and which policy settings should be used. A single label is reusable – you can define it at once and then incorporate it into several label policies assigned to different users.
Check out the previous blog about best practices for creating and publishing labels.
Microsoft 365 Message Encryption
Microsoft 365 Message Encryption is an online service built on Microsoft Azure Rights Management (Azure RMS) that is part of Microsoft Data Protection. This includes the principles of encryption, identity, and authentication to protect your email. You can encrypt messages using the Rights Management template, Do Not Forward option, and Encrypt-Options option only.
Microsoft Information Protection Software Development Kit
MIP SDK opens labeling and security services from the Microsoft 365 Security and Compliance Center on third-party applications and services. Developers can use SDK to create local support for labeling and protection of files. Developers should act if specific labels are found, and MIP can argue over encrypted information. Labels and protections applied to information across a suite of Microsoft services. Continuity allows applications and services to read and write labels in a simple, predictable way that MIP supports.
High-level MIP SDK use cases include:
- A Line-of-Business application that applies classification labels to files on export
- A CAD/CAM design application provides native support for Microsoft Information Protection labeling
- A cloud access security broker or data loss prevention solution reasons over data encrypted with Azure Information Protection
Step 3: Prevent Data Leak
When the protection policy is in place, we must plan precautionary measures against leaking information by which accidental and intentional sharing of information outside the organization can be prevented.
Following are the strategies for implementing life cycle to prevent data breaches-
Data Loss Prevention
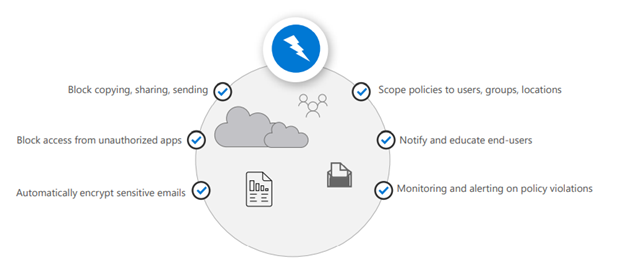
Endpoint Data Loss Prevention
Microsoft Endpoint DLP allows you to monitor Windows 10 devices and detect when sensitive items are used and shared. This gives you the visibility and control you need to ensure that they are used and protected properly, and to help prevent risky behavior that might compromise them.
MCAS Data Protection
Data protection through full MCAS can be applied in many cases. Microsoft 365 and third-party connected applications have multiple data protections from using our data classification services or built-in services using proxies using Data Location Prevention (DLP) that depend on each other. Bring strong DLP experience.
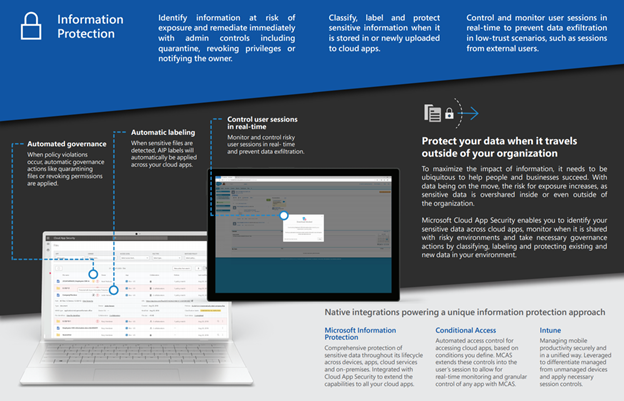
Step 4: Govern and Data Compliance
To help you conform with Data Privacy Policy, Microsoft has designed a workflow to guide you through an end-to-end process to plan and implement expertise across Microsoft 365 to ensure secure access, threat protection, data protection, and data management. In this section, we will discuss each component and guide you through the process to implement your governance policy.
Retention Label
Retention labels are mostly used to keep or remove content, but you can also use them without enabling any retention or other actions. You can simply use a retention label as a text label in this situation, without imposing any actions.
A retention policy can be applied to the following location-
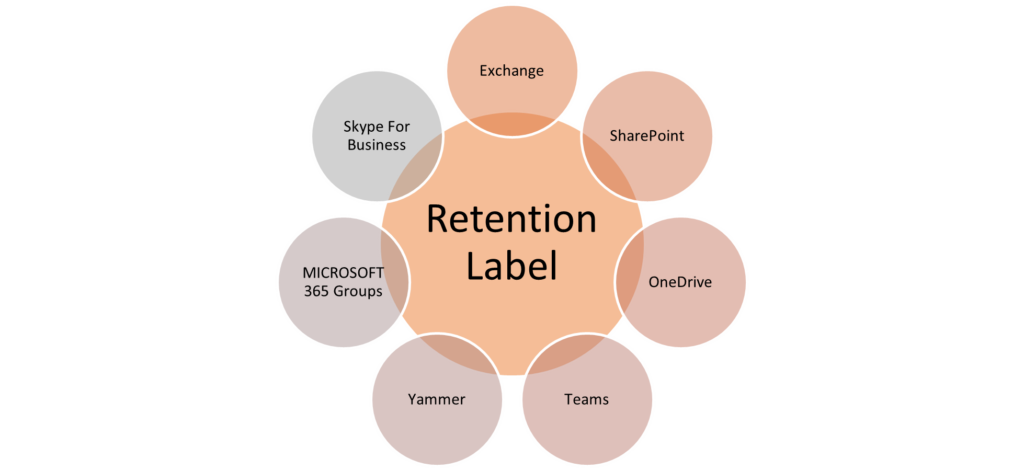
If you currently use these older features, they will continue to work side by side with retention policies and retention labels. However, we recommend that going forward, you use retention policies and retention labels instead. They provide you with a single mechanism to centrally manage both retention and deletion of content across Microsoft 365.
Auto-Labeling
This policy is required to label the document based on predefined criteria or custom criteria.
There are two different methods for automatically applying a sensitivity label to content in Microsoft 365, Client-side labeling, and Server-side labeling-
Client-side labeling
This method supports recommending a label to users, as well as automatically applying a label. In both cases, the user decides whether to accept or reject the label, to help ensure the correct labeling of content.
Server-side labeling
This labeling is applied by services rather than by applications, so you don’t have to worry about what apps users have and the version. As a result, this capability is immediately available throughout your organization and is suitable for labeling at scale.
Conditional Access Policy
This allows you to control your data access depending on the specific conditions such as which application will be used, what is the status of the device, in which region data access will be allowed. This reduces the risk of data breaches.
Information and Records Management
You can create and manage retention labels from Information governance in the Microsoft 365 compliance center, file plan from Records management has additional management capabilities:
- You can bulk-create retention labels by importing the relevant information from a spreadsheet.
- You can export the information from existing retention labels for analysis and offline collaboration.
- File plan descriptors support additional and optional information for each label.
File plans can be used for all retention labels, even if they don’t mark content as a record.
Insider Risk Management
Detect risks like sensitive data leaks and intellectual property theft. Investigate alerts to determine whether user activity was malicious or inadvertent. Quickly take actions to help meet your organization’s compliance goals.
Key Takeaways
This blog will help you plan and drive your information protection in your environment. Most of the Information Protection tools offered by Microsoft are mentioned here and Microsoft is making huge changes in several areas of Information Protection. For the latest updates and roadmap, visiting Microsoft Docs is recommended.
We hope the information is of value to you. In addition, we’re offering a FREE one-hour customized workshop to help assess your current security stance, discuss common threats and best practices to counter them. Contact us here to learn more
Download the Datasheet to learn more about Netwoven’s Information Protection and Compliance service.
Download the Solution Brief to learn how Netwoven’s solution proactively identifies and protects your sensitive data.
























