Introduction:
In Part 1 of this blog series, we explained in detail what Endpoint Detection & Response (EDR) is and the importance of the powerful Defender for Endpoint tool.
After a major security product re-brand and feature/functionality enhancements, the Defender suite takes shape:
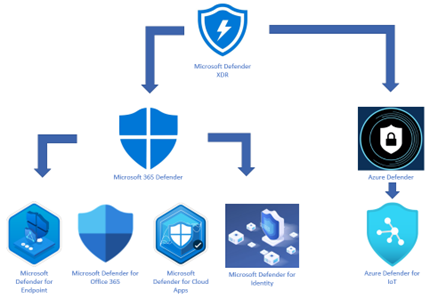
Defender Branding Updates
| New Name | Old Name |
| Microsoft 365 Defender | Microsoft Threat Protection |
| Defender for Endpoint | Microsoft Defender Advanced Threat Protection |
| Defender for Identity | Microsoft Defender for Identity |
| Defender for Office 365 | Microsoft Defender for Office 365 |
| Azure Defender for Servers | Azure Security Center Standard |
| Azure Defender for IoT | Azure Security Center for IoT |
| Azure Defender for SQL | Advanced Threat Protection for SQL |
What is EDR?
Endpoint Detection and Response (EDR), also known as endpoint threat detection and response (ETDR), is a cybersecurity technology that continually monitors an ‘endpoint’ (e.g., mobile phone, laptop, Internet-of-Things device) to mitigate malicious cyber threats.
Endpoint detection and response technology are used to identify suspicious behavior and Advanced Persistent Threats on endpoints in an environment, and alert administrators accordingly. It does this by collecting and aggregating data from endpoints and other sources. That data may or may not be enriched by additional cloud analysis. EDR solutions are primarily an alerting tool rather than a protection layer, but functions may be combined depending on the vendor. The data may be stored in a centralized database or forwarded to a SIEM (Security Incident & Event Management) tool.
Enabling EDR in Block Mode
Requirements:
Firstly, let us check the requirements needed for EDR in Block Mode enablement:
| Requirement | Details |
| Permissions | You must have either the Global Administrator or Security Administrator role assigned in Azure Active Directory. |
| Operating system | Devices must be running one of the following versions of Windows: – Windows 11 – Windows 10 (all releases) – Windows Server 2022 – Windows Server 2019 – Windows Server, version 1803 or newer – Windows Server 2016 and Windows Server 2012 R2 (with the new unified client solution) |
| Microsoft Defender for Endpoint | Devices must be onboarded to Defender for Endpoint. See the following articles: - Minimum requirements for Microsoft Defender for Endpoint - Onboard devices and configure Microsoft Defender for Endpoint capabilities - Onboard Windows servers to the Defender for Endpoint service - New Windows Server 2012 R2 and 2016 functionality in the modern unified solution (Preview) |
| Microsoft Defender Antivirus | Devices must have Microsoft Defender Antivirus installed and running in either active mode or passive mode. Confirm whether Microsoft Defender Antivirus is in active or passive mode. |
| Cloud-delivered protection | Microsoft Defender Antivirus must be configured such that cloud-delivered protection is enabled. How to. |
| Microsoft Defender Antivirus platform | Devices must be up to date. To confirm, using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator. In the AMProductVersion line, you should see 4.18.2001.10 or above. |
| Microsoft Defender Antivirus engine | Devices must be up to date. To confirm, using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator. In the AMEngineVersion line, you should see 1.1.16700.2 or above. |
Wikipedia Endpoint detection and response – Wikipedia
Enabling
Once you have confirmed the above requirements have been addressed, we can move on and enable them.
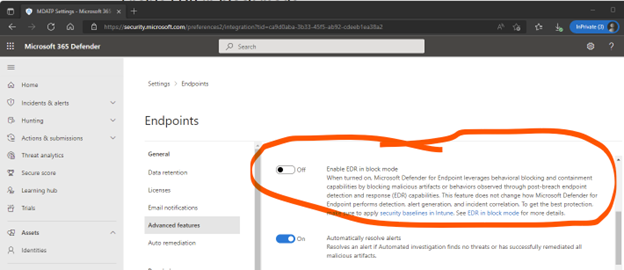
Go to your Microsoft 365 Defender portal @ https://security.microsoft.com and select:
- Settings > Endpoints > General > Advanced Features
- Scroll down to “Enable EDR in block mode”
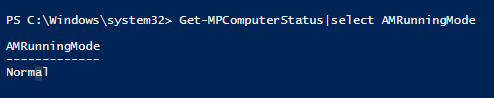
To verify if EDR in block mode is active use the following PowerShell command:
- Get-MPComputerStatus|select AMRunningMode
If the result shows as below, Microsoft Defender Antivirus is in active mode and not EDR Block Mode:
IF EDR Block Mode is successfully activated, you will see the result shown below:
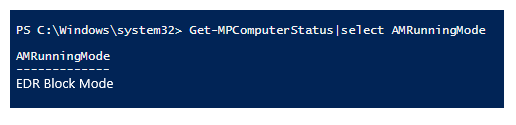
[Bear in mind, if you wish to disable EDR in Block Mode it can take up to 30 minutes to completely disable.]
What next?
To get the best bang-for-your-buck (or ROI!) EDR in Block Mode should be enabled coupled with the latest security baseline for Windows 10 or 11.
What is a security baseline?
Security Baselines bring together the best practice configuration/settings for Windows, think of them like templates. They are designed to help both apply and enforce very granular security settings that have been recommended by the various Microsoft Security teams.
It can be a great thorough starting point; you can then customize to your exact needs the settings desired for your environment. When you create a security baseline profile in Intune, you are creating a template that consists of multiple device configuration profiles.
As quoted by Microsoft:
- A security baseline includes the best practices and recommendations on settings that impact security. Intune partners with the same Windows security team that creates group policy security baselines. These recommendations are based on guidance and extensive experience.
- If you are new to Intune, and not sure where to start, then security baselines give you an advantage. You can quickly create and deploy a secure profile, knowing that you are helping protect your organization’s resources and data.
- If you currently use group policy, migrating to Intune for management is much easier with these baselines. These baselines are natively built into Intune and include a modern management experience.
These are updated throughout the year, here are the baselines for Windows 10/11
You should keep track and check when new baselines are released and see if they would be relevant to your environment and keep them updated.
We hope you found this blog series useful in understanding the advantages of Microsoft Defender for Endpoint and Endpoint Detection and Response (EDR) and how it offers enterprise-grade protection to your endpoints & organization. Please reach out to us so that we can put our decades of experience and expertise in the powerful Microsoft technologies security services to secure your organization.























