Introduction:
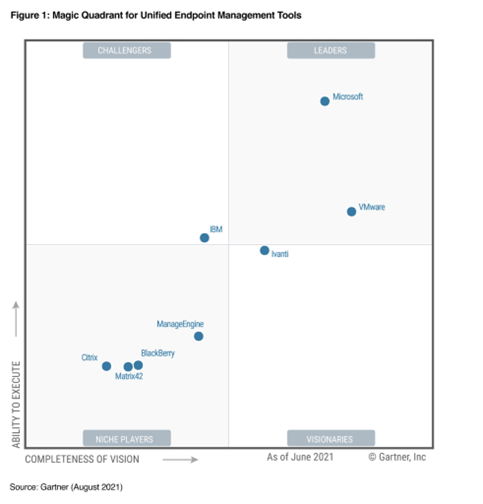
After a swift product shuffle and re-branding we find Microsoft Endpoint Manager emerging to rise up the Gartner ranks to become the leader in Unified Endpoint Management Tools.
So what is it?
Microsoft Endpoint Manager is the umbrella over services you may already be familiar with:
- Microsoft Intune
- Configuration Manager
- Desktop Analytics
- Co-management
- Windows Autopilot
What does it focus on:
- Modern workplace
- Modern management
- Securing your data
- Zero Trust principles
Endpoints are the new workplace
With the unprecedented shift to Remote Working recently, it has ben apparent that endpoints are the new workplace – wherever &, whenever access to your organizations apps and data is needed. This can be PC’s, mobile phones, operating systems, and the critical applications that drive the business.
So where to start?
Here are a few scenarios that may help you decide:
Does your organization provision a lot of new devices?
Start with Windows Autopilot.
To learn more about Netwoven’s Identity & Access Management Capability, Click here.
Does your organization add rules and control settings for your users, apps, and devices?
Start with Intune.
If Configuration Manager is used to deploy apps, and want to use conditional access based on security requirements…
Start with co-management.
If Configuration Manager is responsible for keeping Windows 10 devices current
Start with Desktop Analytics.
If you’re getting started with MDM and MAM, or use ADMX templates to control Office, Microsoft Edge, and Windows settings
Start with Intune.
How can it help secure your endpoints?
Using the Security Admin role you can leverage the “Endpoint Security” node within Intune – here these Endpoint security police s are designed to help focus on security of your devices and also to mitigate risk. This Endpoint Security node pulls all the tools within Intune into one place so you can keep devices secure.
Here’s some of the tasks you can take care of through the Endpoint Security node:
- Review status of all managed devices High level device compliance with drill down to specifics of which compliance policies we not met
- Get security baselines – which align best practice security settings for devices For Windows devices, pre-configured Windows settings to help apply a configuration recommended by relevant security teams
- Manage security configurations on devices via policies Focused policies for all aspects of device security such as disk encryption, antivirus etc.
- Device and user requirements through compliance policy Set the rules that both devices and users must meet before they are compliant, for example OS version, password requirements.